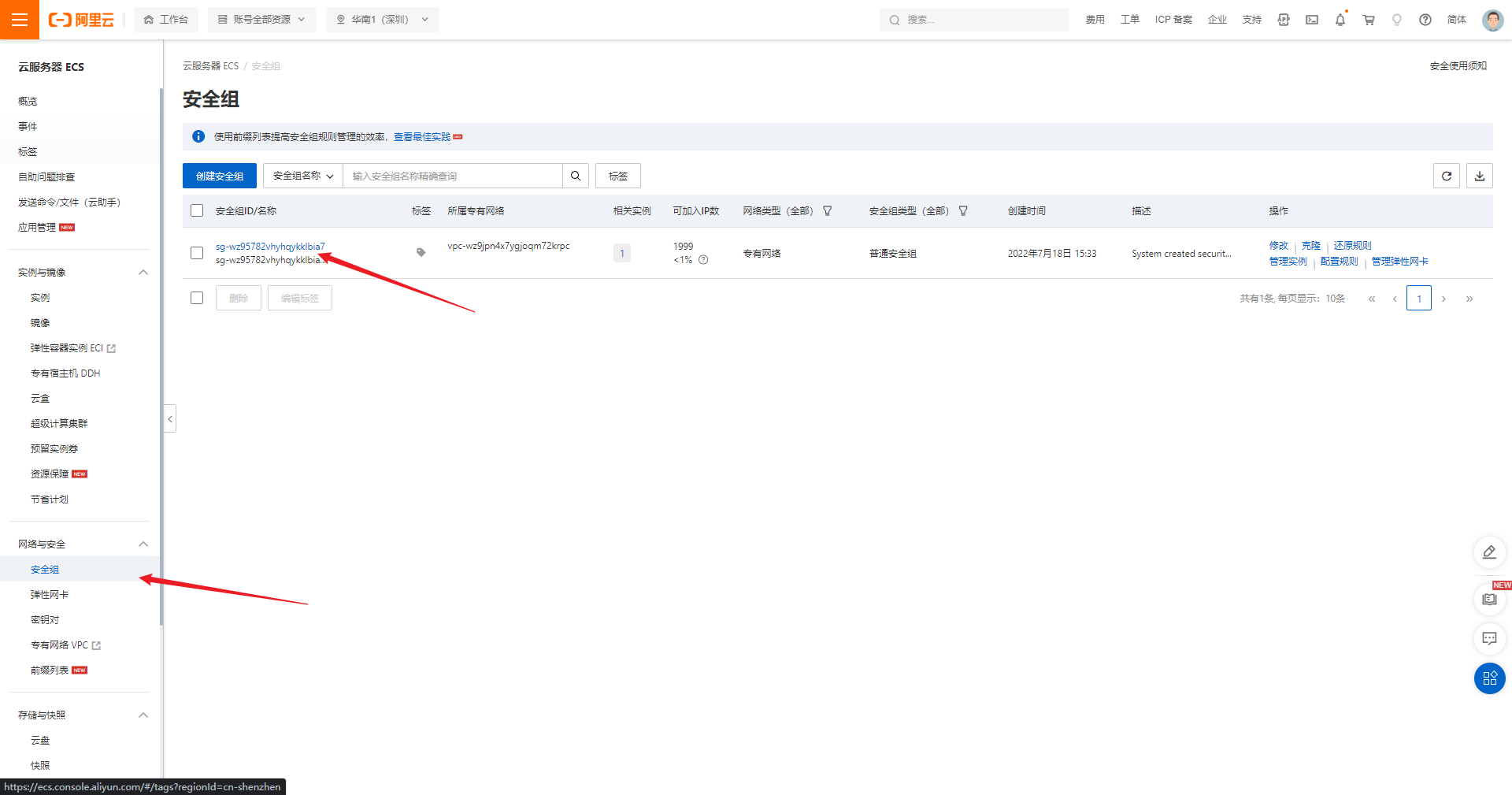
当前位置:网站首页>树莓派ssh登录
树莓派ssh登录
2022-07-23 17:32:00 【十年哞一剑】
ifconfig

出现十六进制 说明没配置
ssh 配置 两步
1 配置网络
1 命令确认能否搜索到你想要的wifi
sudo iw dev wlan0 scan |grep SSID
如下
ChinaNet-iPVN 是我的 (根据情况而定)
2 配置wifi (配置密码 账号)
sudo nano /etc/wpa_supplicant/wpa_supplicant.conf

不要以分号结束
1 ctl +o 保存
2 回车
3 ctl+x 退出
sudo reboot :重启

验证 有无网络 ping 192.168.XXXXXX.7

2 固定ip
sudo nano /etc/rc.local

3 再次重启

ssh 登录

实际ip 多少就多少 名字也是 直接回车

细节处理
热点链接不上 换路由器
边栏推荐
- Application of jishili electrometer in testing scheme of new energy battery
- lendingclub贷款状态loan status业务详解-current,charge off,issued,Fully Paid,grace period
- As a background developer, you must know two kinds of filters
- Four principles of interface design
- C # split usage, split split split string
- Implementation of IIC protocol with FPGA (I) IIC bus protocol
- ZigBee集成开发环境IAR安装
- Elk notes 25 - experience APM quickly
- Cell array processing
- Notes of benthos
猜你喜欢

J9数字论:数字行业的FOMO现象我们应该怎么克服?

Testing scheme of granite dielectric constant by network

Digital security giant entrust revealed that it was attacked by blackmail software gangs in June

LM393 low power dual voltage comparator parameters, pins, application details
使用 frp 实现内网穿透

记一次被网络诈骗的经历

11. Basic concepts of neural network
FPGA implementation of IIC bus of IIC protocol (II) (single read / write drive)

多线程与高并发day11

Todo fix bug tag feature and other configurations
随机推荐
Shell
Electronic components - resistance
not all arguments converted during string formatting
二叉树高度 [log2n]+1与log2(n+1)是否相等
一道题目初探组合数学与DP关系,可重集组合公式推导
SQL statement exercise
多线程与高并发day11
FPGA flash reading and writing based on SPI
Three ways to realize multithreading
小鱼送激光雷达啦 | 恰饭即抽奖第一期
H7-TOOL的CANFD/CAN接口脱机烧写操作说明, 已经更新(2022-07-12)
【C语言】程序环境和预处理
Learn and understand Architecture Design from business development
Application of jishili electrometer in testing scheme of new energy battery
微信小程序自己实现一个全局事件总线
C语言小项目 -- 通讯录(静态版+动态版+文件版)
Mbio | the sun Chaomin formation of Ocean Institute has verified in situ the new pathway of microbial mediated elemental sulfur formation in the deep sea
记一次被网络诈骗的经历
树学习总结
Source code analysis of ThreadPoolExecutor