当前位置:网站首页>Another award | opensca was selected as the "top ten open source software products in the world" at the China Software Expo
Another award | opensca was selected as the "top ten open source software products in the world" at the China Software Expo
2022-07-23 16:15:00 【Open source China Information】
In the near future , China ( nanjing ) The international software products and Information Services Trade Expo was held “ Global open source software product selection ” The award ceremony .OpenSCA With technological innovation 、 Pattern differentiation 、 Market competitiveness and open source community contribution were selected “ Top ten open source software products in the world ”.

chart 1 The suspension mirror is safe OpenSCA Stand out with high scores
SourceClear According to the survey report of , The number of global open source projects has shown an exponential growth trend ,2026 It's expected to exceed 3 Billion . The frequent occurrence of open source software security incidents , But it has greatly affected the prosperity of the open source ecosystem . Open source risk management has become an urgent need of most enterprises at present and even in the future .
Actively practice the safety of hanging mirror “ Do open source risk management in an open source way ” This original idea , Will the source of its mirror OSS Open source threat control platform open source , For the majority of enterprises and developers to provide professional OpenSCA Technical support and community ecological services . Rely on the user participation friendliness of the community and the community operation ability driven by the product delivery ability ,OpenSCA I just won GVP(Gitee Most valuable open source projects ) Annual honors .
As The world's first open source enterprise SCA Technical products ,OpenSCA Inherited the source code OSS Leading open source application security defect detection 、 Multi level open source dependency mining 、 In depth code homology detection and other core capabilities , Through software component analysis 、 Dependency analysis 、 Characteristics analysis 、 Reference recognition 、 Compliance analysis and other methods , Deeply tap various security vulnerabilities and open source protocol risks hidden in components .
Compared with other open source SCA Tools ,OpenSCA It has the following four advantages :
01 Rich programming language and knowledge base support
Support Java、JavaScript、PHP、Python、Go And other mainstream programming languages
Real time component library of cloud platform 、 Vulnerability Library 、 License Library 、 Feature base and other massive knowledge base support
02 Component dependency resolution , visualization SBOM analysis
Analysis of direct and indirect dependencies of components
Component security vulnerability analysis , Quickly locate the impact scope of the vulnerability and repair it in time
visualization SBOM( Software bill of materials ), Help quickly sort out internal software assets
03 License compliance analysis , Intellectual property security
Support the check-out of mainstream licenses
Analyze the compliance and compatibility risks of open source licenses
04 Enterprise class core engine , Higher detection and lower false alarm
Have enterprise class SCA Core detection engine and analysis engine
Based on massive knowledge base and multi-source SCA Open source application security defect detection and other algorithms , Accurately identify the feature file , Improve the detection rate of components

chart 2 OpenSCA Won many awards
This time, it won another big award in the open source field , It further proves that the industry is OpenSCA Full affirmation of technical ability and the construction of open source community . future ,OpenSCA We will continue to make efforts in the construction of open source ecological security and the development of technological innovation . More developers and users are welcome to download applications and participate in the discussion , Put forward your own opinions and ideas , And OpenSCA Hand in hand , Jointly safeguard the security of China's software supply chain .
Participation and contribution , Build open source projects
Thank every member of the open source community for OpenSCA Your support and contribution . We encourage more partners to participate in OpenSCA In the construction of open source projects , Become an open source contributor , Any suggestions can be posted in the comment area or Gitee、GitHub On OpenSCA Project Issues in . Let's embrace open source , Build an open-source and safe ecosystem , Promote the healthy development of open source industry .
OpenSCA It's under the safety flag of hanging mirror Yuanjian OSS Open source version of open source threat control products , Inherited Yuanjian OSS Multiple sources of SCA Open source application security defect detection and other core capabilities .
OpenSCA Do open source risk management in an open source way , Committed to being the escort of software supply chain security , Protect the security of China's software supply chain .
OpenSCA Your code will be in GitHub and Gitee Continuous iteration , welcome Star and PR, Become our open source contributor , You can also submit questions or suggestions to Issues. We will refer to your suggestions and constantly improve OpenSCA Open source project , Please look forward to the support of more functions .
GitHub:
https://github.com/XmirrorSecurity/OpenSCA-cli/
Gitee:
https://gitee.com/XmirrorSecurity/OpenSCA-cli/
OpenSCA Official website :
https://opensca.xmirror.cn/

Welcome to scan the code and contact Xiaojing
Join in OpenSCA Community technology exchange group
边栏推荐
- 七、jmeter发出请求的逻辑
- 后缀表达式(暑假每日一题 4)
- Reproduce various counter attack methods
- 剑指 Offer II 115. 重建序列 : 拓扑排序构造题
- 【云原生】持续集成和部署(Jenkins)
- Bean Validation规范篇----03
- Alamofire 框架封装与使用
- 虚拟主播、偶像代言产品出问题谁负责?律师解析
- php:filter伪协议之[BSidesCF 2020]Had a bad day
- [attack and defense world web] difficulty Samsung 9-point introductory question (middle): ics-05, easytornado
猜你喜欢

冒泡排序-看着一篇就够啦

CS5363,CS5350,CS5328几款太阳能板电池充电管理IC的功能特性与参数对比

High cost performance, high anti-interference touch IC that meets a variety of keys: vk3606d, vk3610i, vk3618i have high power voltage rejection ratio

It's too hard! Tencent T4 boss was still staying up late at 4 a.m. and was actually sorting out the distributed transaction notes

软件测试周刊(第81期):能够对抗消极的不是积极,而是专注;能够对抗焦虑的不是安慰,而是具体。
SOC的第一个Hello_World实验
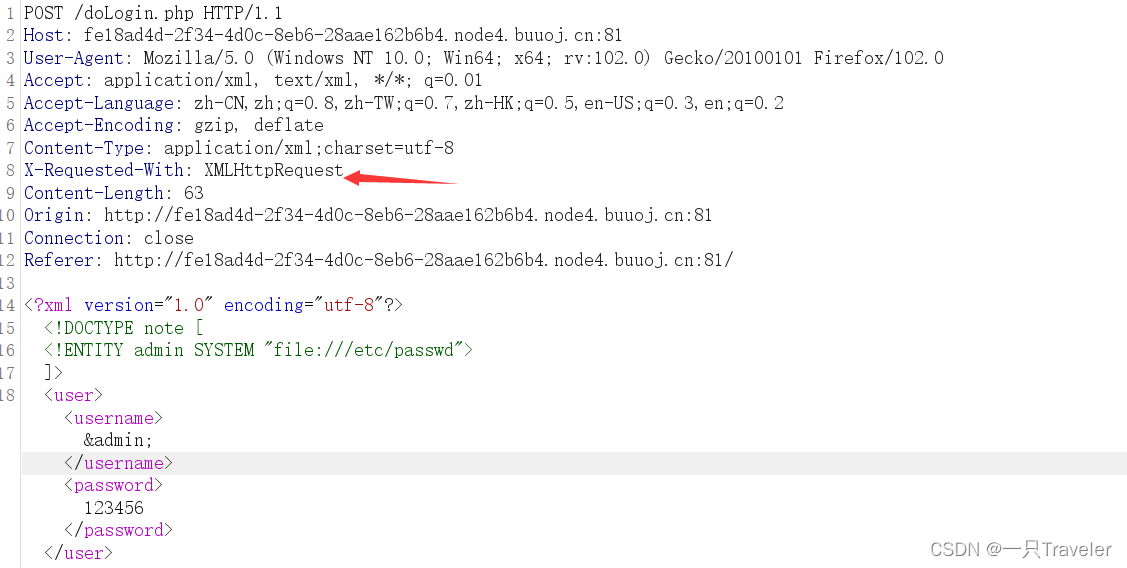
Fake XML cookbook of XML xxE vulnerability

Ultra detailed MP4 format analysis

SSB signal modulation and demodulation based on MATLAB (with source code)

Mathematical Modeling Typesetting
随机推荐
Gear 月度更新|6 月
redis 安装
2022蓝帽杯初赛wp
来自大佬洗礼!2022头条首发纯手打MySQL高级进阶笔记,吃透P7有望
Mysql—六大日志
The difference between deadlock, hunger and dead cycle
php:filter伪协议之[BSidesCF 2020]Had a bad day
PHP code audit 4 - SQL injection vulnerability
云原生(十一) | Kubernetes篇之Kubernetes原理与安装
七、jmeter发出请求的逻辑
ICML 2022 | 稀疏双下降:网络剪枝也能加剧模型过拟合?
SOC的第一个Hello_World实验
现代商业无代码开发平台的治理和网络安全
如何成为一个优雅的硬件工程师?
Leetcode high frequency question: the array can be changed into a non descending state after at least several operations
Bean Validation入门篇----02
Summary of server performance tuning experience
MySQL 灵魂 16 问,你能撑到第几问?
關於初始化page入參的設計思路
ECS remote monitoring