当前位置:网站首页>Detailed sorting of HW blue team traceability process
Detailed sorting of HW blue team traceability process
2022-06-26 13:29:00 【zkzq】
Zero basic hacker , Search official account : White hat left
background :
During the authorized attack and defense drill , The attacker tried every means to infiltrate the target . Generally, the attack chain includes : scout 、 Weaponization 、 deliver 、 utilize 、 install 、 Command and control 、 Steal target data . In traceability , Security personnel analyze the attack characteristics of an attacker at a certain stage , Combined with the known threat intelligence data, the attack characteristics and data are clustered , Can effectively master the attacker's attack tactics and IP 、 Domain name assets, etc .
The goal is :
Master the attacker's attack techniques ( for example : Specific Trojan horse 、 Weapon delivery method );
Master the attacker's IP Domain name assets ( for example : Trojan horse C2、 Trojan horse storage site 、 Asset characteristics );
Master the attacker's virtual identity 、 identity ;
Master the detection or discovery methods of the attacker's weapons , Form new clues from the captured data .
methodology :
For delivery 、 utilize 、 install 、 Command and control the data captured in the four stages for in-depth analysis , Clustering extracts data characteristics and forms rules . The rules are applied to some security devices to produce high reliability alarms for defense , Or combined with intelligence data ( Such as sample information 、 Domain name information 、IP Information, etc ), Information that will trace the source in depth ( Such as identity information 、 Attack team, etc ) Produce .
1. The key points of the traceability of the attack chain :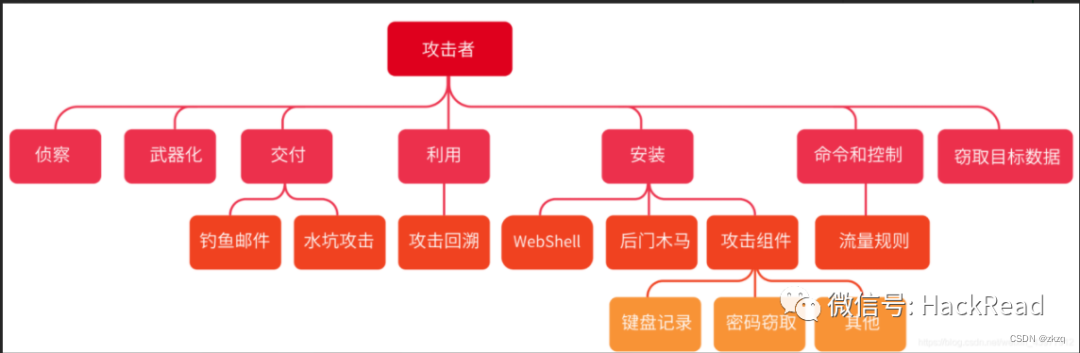
2. The traceable method and utilization point of the utilization stage of the attack chain :
The key points of attack backtracking can be divided into two categories :
Attack categories : Exploit packet characteristics according to the attacker's vulnerability ( Such as : String format 、 Special string ).
Attacker information : Attackers use their companies ( personal ) Unique vulnerability exploitation tools , There may be companies in the request package ( personal ) Information .
3. The traceability method and key points of phishing emails :
Hair parts IP、 Sending account number 、 Email content ( Format features, etc ) Can be used to categorize messages delivered by attackers ;
There may be personal information in the sending account , Such as :“ account number @qq.com”、“ nickname @gmail.com” And so on , Retrieving this string can be used to mine identity information ;
Mail content can be roughly divided into the following three categories :
Deliverable ( Back door Trojan 、 Other attack components )
Phishing site , Contains domain names 、IP Etc
other , You need to study the strings in the message , The message may exist in other accounts of the attacker ( In real scenes ) Hair parts IP、 Sending server , Is an attacker's asset .
4. Backdoor Trojan horse Traceability Method and key points :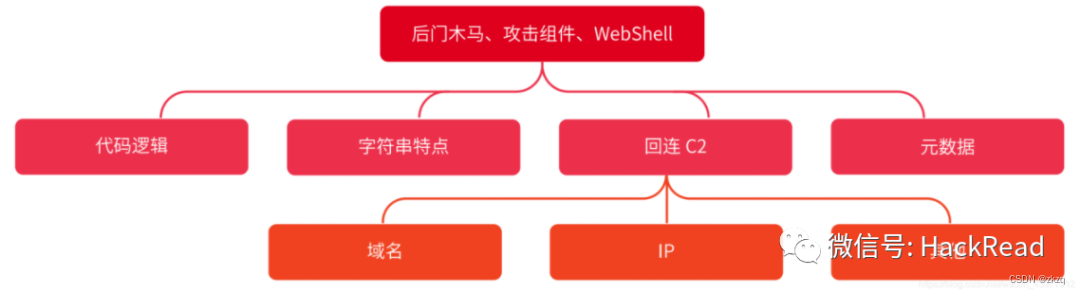
Code logic , Because of human inertia , Red team developers may reuse some of the previous code . For example, the code features are obvious , It can be used for classification and line extension .
String characteristics , It is used to classify the samples delivered by the red team and expand more samples , Analyze the retrieved samples , Analyze historical samples ( Such as the sample in the test stage ) See if more information will be revealed .
Metadata ( The bait delivered is different , The metadata obtained is different . The types of lures include :LNK、EXE、DOCX etc. ).
EXE file : There is PDB Information , Some developers store projects on their desktops , This causes compilation information to be brought into the developer's terminal name ( Most likely a personal nickname ).
LNK file : because LNK The computer name will be brought in when the file is created , This can be used for extension and classification of samples , Personal nicknames are rarely found .
DOCX file : Possible “ Last editor's name ”.
Huilian C2, Is an attacker's asset .
5. The traceability method and key points of attacker's asset dimension :
The domain name has its own characteristics , Such as : Nickname string
Build a website ( Detect the existing data and historical data of assets through the four methods in the figure )
Other attack components of the red team may exist on the website
There is a personal nickname on the website 、 Introduction, etc
Website filing information
Whois Information , May contain : Registrant email 、 Phone number, etc
IP Information needs to consider the following two points :
Whether to locate the geographic location of a security company
Whether to mark as the gateway of a security company
6. The data that can be generated during the command and control phases 
For defense , Deploy the mastered traffic rules in the security equipment to accumulate data , Master more Trojans 、 assets , Support various traceability methods in the above
7. The traceability direction of identity information :
Virtual identity
Information exposed by the attacker's assets , Such as :Whois Information 、 Personal website profile 、GitHub Personal profile
Information exposed by the sample , Such as :PDB Information 、 Personal Nickname 、 Store Tema's Github account number
Honeypot capture , Such as : Baidu ID、 Sina ID etc.
Use the password retrieval function , Such as : Alibaba cloud IP Retrieve 、 Tencent password Retrieval 、 Email password retrieval
identity
Social networking platform ( Such as Baidu Post Bar 、QQ Space 、 Sina Weibo, etc ) Expose real name 、 Phone number
Alipay transfer function , Search mailbox 、 cell-phone number
Known clues ( mailbox 、QQ、 Nickname, etc ) Search the recruitment website for
Using search engines , Such as : Mobile phone number and real name are stored together XXX School forms
Company information
IP Asset positioning 、 domain name Whois Information
Information exposed by specific vulnerability exploitation tools , Such as :User Agent、Cookie、Payload
Social networking platform , Such as : nailing 、 Enterprise wechat, etc
Work experience in the attacker's resume
technological process :
1. in the light of ip Through open source intelligence + Open port analysis query
You can use the website :
https://x.threatbook.cn/( The main )
https://ti.qianxin.com/
https://ti.360.cn/( The main )
https://www.venuseye.com.cn/
https://community.riskiq.com/
When you find something IP After the attack , You can try this IP Go back to the attacker
First, through http://www.ipip.net Website or other interface , Query the IP by IDC Of IP、CDN Of IP Or the export of ordinary operators IP.
If IP You can go to the webmaster's house to check the domain name whois Check or go back https://whois.domaintools.com/ Wait for the website to query the registration information of the domain name 、http://whoissoft.com/ Query filing information, etc .
port : See open services for further use
Consider using masscan Quick view of open ports :
masscan -p 1-65535 ip --rate=500
Re pass nmap Identify open ports
nmap -p 3389,3306,6378 -Pn IP
Find relevant useful ports , Mining and utilizing port related vulnerabilities .
2.ip Query location
ip Positioning tools :
High precision IP location :https://www.opengps.cn/Data/IP/LocHighAcc.aspx
rtbasia(IP Inquire about ):https://ip.rtbasia.com/
ipplus360(IP Inquire about ):https://www.ipplus360.com/
IP Address query online tool :https://tool.lu/ip/
Through IP Location technology traceability process , Attention should be paid to the following :
If IP Too many domain names have been found , Consider that CDN 了 , There's no need to keep checking .
If it is the export of ordinary operators IP Only some high precision IP The location tool roughly estimates the attacker's address , If you need to specifically locate people , More information is needed .
3. ID track 、 Get used to id information gathering
Through IP After locating, the technology tracks the attacker , Through the fingerprint Library 、 Social work library or other technical means to grab the attacker's microblog account 、 Baidu ID Etc , It is generally realized by the following technical means :
Conduct QQ Wait for the same name to search 、 Search by forum and other methods with the same name 、 Social work library matching, etc .
Such as ID It's the mailbox , Then match the password through the social work Library 、 Previous registration information, etc .
Such as ID It's mobile phone number. , Then search the relevant registration information through the mobile phone number , And mobile phone number, user name, etc .
Other methods :
(1) Baidu information collection :“id” ( Double quotation marks are in English )
(2) Google Information Collection
(3) src information gathering ( The major src Ranking List )
(4) Microblog search ( If you find a microblog record , You can use tg Inquire about weibo Leaking data )
(5) WeChat ID collect : Wechat ID Search for ( Send out the nail group and check it together )
(6) If you get a mobile number ( You can search Alipay directly 、 Social accounts, etc )
Be careful : Get your mobile phone number if you don't have much information , Report directly to the nail group ( Using the sharing channel to carry out secondary social work )
douban / tieba / You know / affectionately All the social platforms you can know , Collect information

for example , When passed ID Tracking technology means to locate an attacker's QQ Number 、QQ Net name and other information , Through the professional social worker library, the attacker can be further tracked QQ Other registered network numbers ID, To get more information about attackers , To determine the identity of the attacker .
Be careful : cell-phone number 、 nickname ID All are key data , If you can't find too much information , Report directly to the headquarters .
4. Forewarning equipment information forensics
The data above is nothing , We can consider screening the behavior of the attack , Try to determine if it has fingerprint features .
If an attacker uploads an attack program to the target during the attack ( Such as phishing Software ), By analyzing the malicious program uploaded by the attacker , And combine IP location 、ID Trace and other technical means to analyze and trace the source of the attack , Common malicious program analysis websites are :
Ø Micro step online cloud sandbox :https://s.threatbook.cn/
Ø Virustotal:https://www.virustotal.com/gui/home/upload
Ø Eye of fire (https://fireeye.ijinshan.com)
Ø Anubis(http://anubis.iseclab.org)
Ø joe(http://www.joesecurity.org)
5. Springboard information collection ( Trigger )
Enter the red team springboard machine for information , If the host desktop does not have sensitive information , Information can be collected for the following documents .
Last: Check login success log
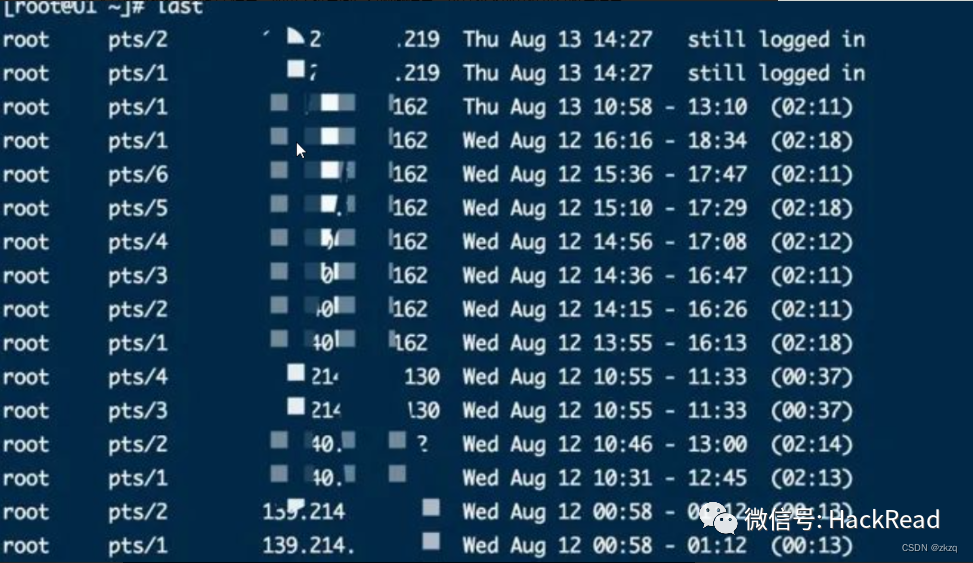
Cat ~/.bash_history Look at the operating instructions

Ps -aux Check the process


Cat /etc/passwd
See if there's something like ID Users of
Focus on uid by 500 The above login users
nologin You can't log in 

边栏推荐
- Oplg: new generation cloud native observable best practices
- MySQL explanation (I)
- 2. Introduction to parallel interface, protocol and related chips (8080, 8060)
- Mysql database explanation (IV)
- Map value
- Hdu1724[Simpson formula for integral]ellipse
- 橋接模式(Bridge)
- Processsing function random
- es常用语法一
- Electron official docs series: Processes in Electron
猜你喜欢

MySQL数据库讲解(三)

Bifu divides EtherCAT module into multiple synchronization units for operation -- use of sync units

mysql讲解(一)
NVM installation tutorial

Here Document免交互及Expect自动化交互

【Spark】. Explanation of several icons of scala file in idea

Mediapipe gestures (hands)

ES基於Snapshot(快照)的數據備份和還原

Firewall introduction

网络远程访问的方式使用树莓派
随机推荐
Mysql database explanation (V)
IDC report: the AI cloud market share of Baidu AI Cloud ranks first for six consecutive times
I have a good word to say, and I admire myself
[how to connect the network] Chapter 2 (next): receiving a network packet
外观模式(Facade)
Processing polyhedron change
Some conclusions about Nan
Uva11582 [fast power]colossal Fibonacci numbers!
Bridge mode
Thinking caused by the error < note: candidate expectations 1 argument, 0 provided >
C language: Exercise 2
G - Cow Bowling
B - Bridging signals
原型模式(prototype)
A primary multithreaded server model
Mysql database explanation (III)
Prototype
LAMP编译安装
偶言佳句,孤芳自赏
sed编辑器