当前位置:网站首页>Some assembly instructions specific to arm64
Some assembly instructions specific to arm64
2022-06-25 11:05:00 【Hua Weiyun】
adrp Instructions (address page)
It's an address read instruction , Is used to calculate the specified data address to the current PC The relative offset of the value .
Here is its specific usage and explanation
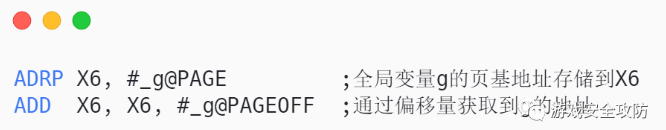
Get a size of 4KB The base address of the page , And there are global variables in the page g The address of ;ADRP That is to say, the base address of the page is stored in the register X6 in ;
ADD The command will calculate g The address of ,X6+#[email protected],#[email protected] It's an offset ; So you get g The address of X6;
• Memory read and write instructions (ldr、ldur、ldp, str、stur、stp)
STR、STP、STUR Instructions for storing data ( notes : With ST The beginning is represented as a storage instruction )
LDR、LDP、LDUR In order to get the data instruction ( notes : With LD The first expression is to take out the data )
The following is the specific instructions and assembly code analysis
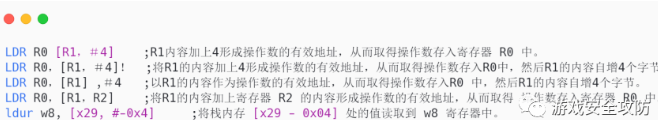
STR Instructions : Read the data out of the register , Store in memory .
STUR Instructions : Read out the negative data in the register , Put it in memory .
STP Instructions : Represents the stack instruction .

LDR Instructions : Taking data out of memory , Put it in the register .
LDUR Instructions : Take out the negative data in memory , And stored in a register .
LDP Instructions : Represents the stack instruction
边栏推荐
- 今天16:00 | 中科院计算所研究员孙晓明老师带大家走进量子的世界
- Array structure collation
- 【图像融合】基于形态学分析结合稀疏表征实现图像融合附matlab代码
- 每日3题(2)- 找出数组中的幸运数
- 报名开启|飞桨黑客马拉松第三期如约而至,久等啦
- 西门子PLCS7-200使用(一)---开发环境和组态软件入门
- Get to know Prometheus
- Google Earth Engine(GEE)——evaluate實現一鍵批量下載研究區內的所有單張影像(上海市部分區域)
- 成长:如何深度思考与学习
- 【文件包含漏洞-04】经典面试题:已知某网站仅存在本地文件包含漏洞时,如何GetShell?
猜你喜欢

【文件包含漏洞-04】经典面试题:已知某网站仅存在本地文件包含漏洞时,如何GetShell?

垃圾回收机制

ZABBIX distributed system monitoring

OpenCV学习(一)---环境搭建

查询法,中断法实现USART通信
![[file containing vulnerability-03] six ways to exploit file containing vulnerabilities](/img/4f/495c852eb0e634c58e576d911a2c14.png)
[file containing vulnerability-03] six ways to exploit file containing vulnerabilities

Nuxtjs actual combat case
![[observation] objectscale: redefining the next generation of object storage, reconstruction and innovation of Dell Technology](/img/82/8cac87231e51698ab17f1274b3a0bd.jpg)
[observation] objectscale: redefining the next generation of object storage, reconstruction and innovation of Dell Technology

Compilation of learning from Wang Shuang (1)

FPGA displays characters and pictures based on VGA
随机推荐
Handling of NPM I installation problems
Opencv learning (I) -- environment building
软件测试 避免“试用期被辞退“指南,看这一篇就够了
【文件包含漏洞-03】文件包含漏洞的六种利用方式
性能之文件系统篇
Is it safe to speculate in stocks by mobile phone?
COSCon'22 讲师征集令
Task03 probability theory
金仓KFS数据集中场景(多对一)部署
Application of global route guard
Previous string inversion topic
Upload and modify the use of avatars
好好思考
Google Earth engine (GEE) - evaluate enables one click batch download of all single images in the research area (some areas in Shanghai)
Oracle彻底卸载的完整步骤
[the path of system analyst] Chapter 6: Double inventory demand engineering (comprehensive knowledge concept)
【文件包含漏洞-04】经典面试题:已知某网站仅存在本地文件包含漏洞时,如何GetShell?
Floating window --- create a system floating window (can be dragged)
ZABBIX distributed system monitoring
Sign up to open the third session of the "flying oar hacker marathon". It's been a long time