当前位置:网站首页>[business security-02] business data security test and example of commodity order quantity tampering
[business security-02] business data security test and example of commodity order quantity tampering
2022-06-27 13:47:00 【Like the wind 9】
Catalog
0 Preface
Data security in business is not only whether the data stored in the background and database will be illegally stolen or modified , It also includes whether the data in the transmission process has been illegally stolen or modified .
1 Commodity payment amount tamper test
summary : E-commerce websites in the whole business process , Need to be right Business data integrity ( Tampering is not allowed ) and Uniformity ( coherence ) To protect , In particular, ensure that the user client and service 、 Consistency of data transmission between business system interfaces , Usually in the ordering transaction data process , It is easy to see that the server fails to perform mandatory verification on the business data submitted by the user , Tampering vulnerability of commodity amount caused by over trusting the business data submitted by the client .
methods : Commodity amount tampering test , It is to modify the transaction amount and other fields in the business process through packet capturing , To detect whether there is an amount tampering vulnerability .
Purpose : This test is mainly aimed at the process of order generation There are business security risk points caused by incomplete verification of commodity payment amount , A business logic vulnerability that usually causes an attacker to order goods with an amount actually paid much less than the amount paid for the order .
Example : Grab the amount field of the goods in the request on the payment page , Modify the amount into any data and submit , Check whether the business process can be improved with the modified amount data . For example, I bought a refrigerator for a penny .
2 front end JS Limit bypass test
summary : Many goods are limited to the number of users in promotional activities , If The server only passes through the page JS Script restrictions , The quantity submitted by the user is not verified on the server , Then there is the modification of the request packet sent by the client JS Business vulnerability of transaction data generated and processed by the client .( Other query services may limit the time period , Similar vulnerabilities may exist )
methods : Change the quantity of goods in the request to be greater than the maximum displayed value , Check whether the business process can be completed with abnormal business transaction data .
Purpose : This test is mainly aimed at e-commerce platforms Because the transaction restriction mechanism is not rigorous 、 Some business logic problems caused by imperfections .
3 Business cap test
summary : The business ceiling test is mainly aimed at some e-commerce applications in the business processing process , The server does not have the query scope submitted by the user 、 Order quantity 、 Strictly verify the amount and other data And caused some business logic vulnerabilities .
methods : Usually , In the business process, submit to the server Data higher or lower than expected To verify whether the server performs expected verification on the submitted data . Applications with such vulnerabilities , It usually shows that the query finds more information than expected 、 Order 、 Or exchange commodities beyond the expected range .
Purpose : This test mainly judges Whether the application responds correctly to business requests that are outside the expected scope of the business .
4 The order quantity of goods is tampered with
summary : The commodity quantity tampering test is modified by capturing packets in the business process Quantity of goods ordered Etc , To determine whether the server has a commodity order quantity tampering vulnerability .
methods : Change the quantity of goods in the request to any Unexpected amount 、 negative And so on , Check whether the business system can complete the business process in the modified quantity .
Purpose : This test is mainly aimed at the process of ordering goods , The server lacks risk control mechanism for abnormal transaction data processing And lead to related business logic vulnerabilities .
Example :damiCMSV5.4 Take online shopping mall as an example . Please refer to the article 《 E-mall business logic vulnerability —— Tampering with transaction data 》.
5 Request replay test
summary : Request replay vulnerability is a common vulnerability caused by design defects in the business logic vulnerability of e-commerce platform , Usually, the safety problems caused by the first successful purchase of goods , Refer to the normal process of ordering goods to request , Replay operations that completely simulate the normal ordering business process , Can achieve “ One purchase and multiple receipts ” And other results that violate the normal business logic .
Purpose : This test is mainly aimed at the e-commerce platform order exchange business process For each transaction request Uniqueness Judge the business logic problems that lack effective mechanisms , Through this test, we can verify that random number 、 Time stamp Whether the data generation mechanism is normal .
6 Example of tampering with the order quantity of goods
6.1 The experiment purpose
(1) Deepen understanding of the importance of business data security ;
(2) Master the method of testing whether there is any vulnerability of tampering with transaction data in business data .
6.2 Experimental environment
6.2.1 Experimental target
Experimental target ——win2008 virtual machine : The experimental range of this section is at win2008 The system is based on phpstudy Build a simple website ,win2008 And phpstudy The installation process of can refer to 《【 Language environment 】WAMP Environment deployment and optimization — With win2008R2SP1 For the operating system 》, The construction process of the website can refer to 《【(SQL+HTML+PHP) comprehensive 】 A case of comprehensive development of a simple forum website ( With user registration 、 Sign in 、 Cancellation 、 Modify the information 、 Message and other functions )》.
attack : Real machine . Note that the target and attacker are on the same LAN .
6.2.2 Build a range —damiCMS-V5.4
build damiCMS-V5.4 The steps of shooting range are as follows
(1) download damiCMS-V5.4 edition CMS Electronic mall code .
- link :https://pan.baidu.com/s/1b-Z6RaFBZ6CsSIErY46Pyg?pwd=q8qq
- Extraction code :q8qq
(2) Unzip and copy the folder to the root directory of the target website . Different versions phpstudy The directories generated during software installation may be different , this paper dami_5.4 Path as follows .
(3) Real machine browser input 172.16.1.1/dami_5.4 visit damiCMS( Because it's not installed yet , You need to install... According to the following steps first CMS), Slide the page to the bottom , Check and click continue .
(4) Click to continue .
(5) Fill in information :
- phpstudy Account and password in the database , By default, it can be set to root, Fill in the database name damicmsv54.
- The administrator user and password are set to admin.

(6) installation is complete , Click to visit the home page of the website .
(7) Click on the top right corner to register , Fill in the user name 、 password 、 mailbox , And click OK to register .


(8) Click the upper right corner to enter the login page , Try logging in to the account just now , Login successful 


6.3 Experimental process
(1) Real machine browser access 172.16.1.1/dami_5.4, Log in to the account just now , Login successful , Return to the following page .


(2) Click on “ Recharge online ”→“ I want to withdraw cash ”. You can see that the current account balance is 0.

(3) Enter the product selection display → Choose a product .
(4) Change the quantity on the page to -1, Click buy now .
(5) Just fill in something , The payment method is station deduction , Click submit order .
(6) Enter the member center again in the upper right corner of the website , Check the account amount again , Found more 6000. That is, the one just entered -1 The quantity in turn adds an amount to the account , This is the business vulnerability .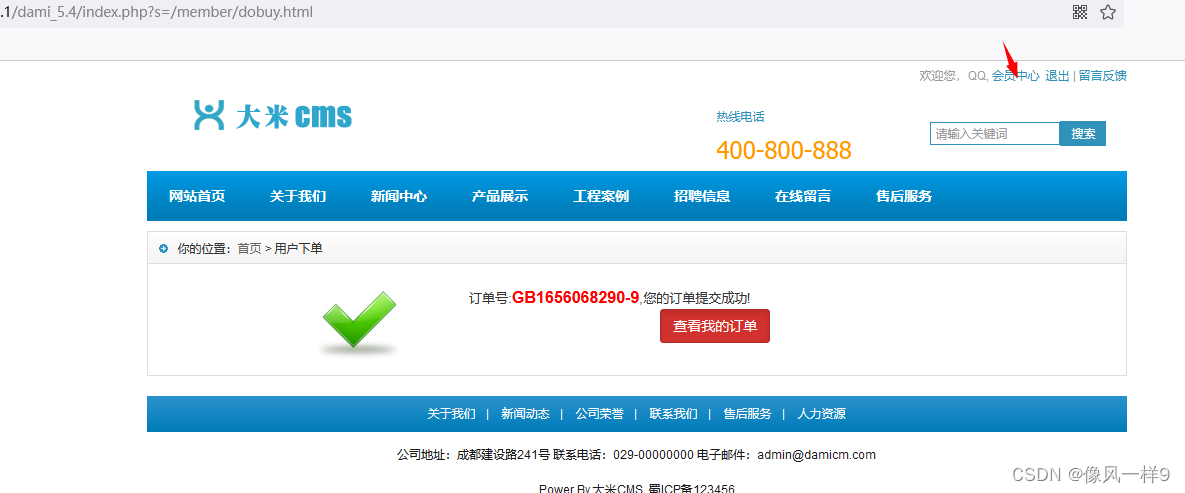

7 summary
(1) Understand which locations or processes have business data security risks ;
(2) Master the test methods of different risk points .
(3) Deepen the understanding of business logic vulnerabilities .
(4) Master the test method of business logic vulnerability of tampering with transaction data .
边栏推荐
- Does Xinhua San still have to rely on ICT to realize its 100 billion enterprise dream?
- 新华三的千亿企业梦,还得靠吃ICT老本来实现?
- Summary of basic usage of command line editor sed
- crane:字典项与关联数据处理的新思路
- A statistical problem of shell script
- Explore tidb lightning source code to solve the found bugs
- Crane: a new way of dealing with dictionary items and associated data
- 以前国产手机高傲定价扬言消费者爱买不买,现在猛降两千求售
- 线程同步之信号量
- Dynamic Networks and Conditional Computation论文简读和代码合集
猜你喜欢
What else can PLM do?

Summary and Thinking on interface test automation
![[acwing] explanation of the 57th weekly competition](/img/ef/be89606b0e7fffac08280db0a73781.gif)
[acwing] explanation of the 57th weekly competition
【业务安全-01】业务安全概述及测试流程

Redis持久化

The second part of the travel notes of C (Part II) structural thinking: Zen is stable; all four advocate structure

Crane: a new way of dealing with dictionary items and associated data
Realization of hospital medical record management system based on JSP

A pang's operation record

每日刷題記錄 (六)
随机推荐
How to set postman to Chinese? (Chinese)
爱可可AI前沿推介(6.27)
Domestic database disorder
AXI总线
Daily question brushing record (6)
Journal quotidien des questions (6)
JVM performance tuning and monitoring tools -- JPS, jstack, jmap, jhat, jstat, hprof
同花顺能开户炒股吗?安全吗?
高德地图IP定位2.0备份
Postman如何设置成中文?(汉化)
Cesium realizes satellite orbit detour
【第27天】给定一个整数 n ,打印出1到n的全排列 | 全排列模板
Prometheus 2.26.0 新特性
事务的四大特性
How to solve the problem of missing language bar in win10 system
高效率取幂运算
Axi bus
防火墙基础之华为华三防火墙web页面登录
[XMAN2018排位赛]通行证
Quick news: Huawei launched the Hongmeng developer competition; Tencent conference released the "Wanshi Ruyi" plan