当前位置:网站首页>Web novice problem of attacking and defending the world
Web novice problem of attacking and defending the world
2020-11-08 09:40:00 【osc_5emtajt2】
Through self-study for a month web Theoretical knowledge , Also on web After a preliminary understanding of the basic loopholes of , I began to attack and defend the world of brush topic journey . in order to The senior's task Summing up the knowledge, I wrote this article wp Among them also draw lessons from the idea of a few big man on the net . Let's not talk much nonsense and get to the point .
The first question is view_source
 Just in CTF web There must be some uncertainty about the direction , Source code habits , But the first question found that the right mouse button can not be used , The simplest way to view source code has been disabled . But don't panic , We have another artifact , Developer toolbar , Click on the web page F12, Call up to view the source code ,flag It's hidden in it .
Just in CTF web There must be some uncertainty about the direction , Source code habits , But the first question found that the right mouse button can not be used , The simplest way to view source code has been disabled . But don't panic , We have another artifact , Developer toolbar , Click on the web page F12, Call up to view the source code ,flag It's hidden in it .

This question examines the way we look at the source code , There are only two ways to solve this problem . Here I refer to the data to summarize the way to query the source code .
1. The simplest way is to click the right mouse button to query .
2. use F12 Open the developer toolbar to view .
3. use PHP Script to query .
4 Can pass JS Code to view .
The second question is robots
 The title description is obvious , Namely Robots agreement , But I just started Don't understand ,
The title description is obvious , Namely Robots agreement , But I just started Don't understand , Everyone laughs and everyone is Xiaoning , There's too much basic knowledge , Now we are looking for the materials to review . therefore Robots What does the agreement mean . Baidu Encyclopedia link I put here robots agreement If you are interested, you can have a look at it yourself , In popular terms, it means robots.txt Give the reptile a range to crawl , The equivalent of a crawler restraint . Since the title reminder is robots agreement , So we open the website robots.txt Go and see what's inside

It was found that there was flag The file of .PHP The name of the file is known , We can open files directly on the website without a crawler .
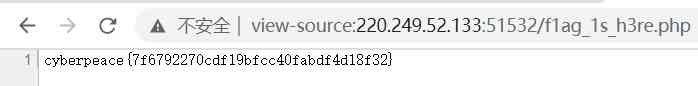 obtain flage. In fact, this question is about Robort Understanding of the agreement , A very basic problem .
obtain flage. In fact, this question is about Robort Understanding of the agreement , A very basic problem .
Third question backup
 At the beginning, I asked for some questions , Find a backup file , How to find ...
At the beginning, I asked for some questions , Find a backup file , How to find ...
But when I open the real URL , The subject slapped the answer on my face , It's a basic question .

indx The backup file is directly used indx The suffixes of the backed up files are tested one by one . The common suffixes of backup files are .gif .svn .swp .~ .bak .bash_hidtory .bkf After the URL After adding these suffixes, one experiment found that .bak There is .
 Here's what I've done over and over again, and there's three files .
Here's what I've done over and over again, and there's three files .
Open the notepad and you get Flag

This topic is to investigate the mastery of backup files , The title is simple. .
Fourth question cookie

Another question to write the answer on your face , Go directly to the web page and open the developer toolbar to find the web page cookie.
 When you see the prompt, open this PHP file
When you see the prompt, open this PHP file
 notice http There's a flag.
notice http There's a flag.
But we should not confine ourselves to writing the title , among cookie And how to use cookie To do something, we should understand .cookie In fact, it is a user certificate , The server uses this to determine the identity of the user , But when hackers take advantage of our cookie It's hard for us to disguise ourselves . The most typical vulnerability is CSRF Loophole .CSRF Vulnerability Details If you are interested, you can learn something about .
Fifth question disabled_button
 The title page looks like this , The stem has given us a clue disable Property is disabled , We guess at form Some of the elements in are disabled . So is it what we're guessing , Let's get into the topic and have a look at
The title page looks like this , The stem has given us a clue disable Property is disabled , We guess at form Some of the elements in are disabled . So is it what we're guessing , Let's get into the topic and have a look at

See this, we open the source code of the page to see
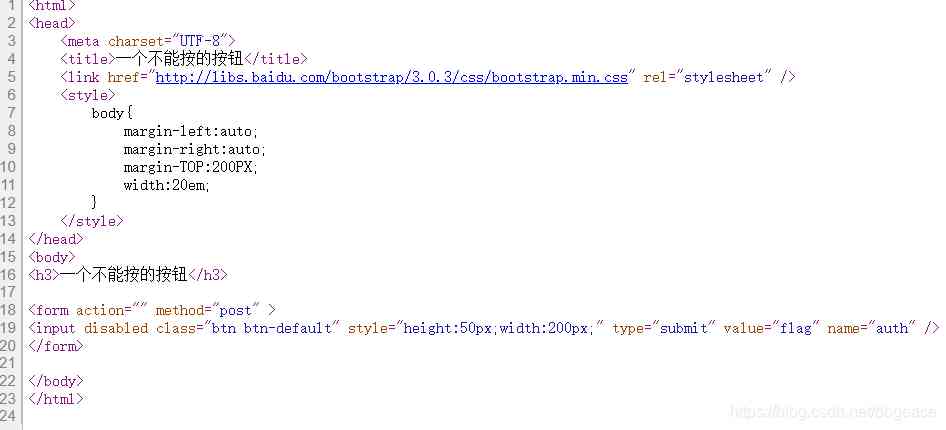 stay 19 OK, we found that there was disable The existence of , We delete it to get
stay 19 OK, we found that there was disable The existence of , We delete it to get
 Found it can click on , When we click, we get what we want flage.
Found it can click on , When we click, we get what we want flage.

Therefore, the purpose of this study is to let us understand HTML The role of each tag element of , Focus on the foundation .
Sixth question weak_auth

The title gives an obvious hint of weak password problem , In this topic, we need to use tools other than browser , I was highly recommended by my schoolmaster for its powerful function .
Let's start with a simple experiment with the login of the web page

When we log in with a random password 
Found that the alert user name is admin, Then the rest is left to the tools . But it's important to remember that the choice of dictionary to crack is particularly important , I was writing this question because of the wrong choice of dictionary , Test tens of thousands of samples , Still no answer . Bad memory . After our constant attempts, we finally got the code 123456

In the end, I got flag.
This question is actually to examine the use of tools , If you can't use tools ... One hour self-study starts , Don't ask me how I know , Asking is for nothing .
Sixth question simple_php
 The title here probably means
The title here probably means C Language is the best language Xiao Hong wrote a PHP Code then let's solve the problem and click into the page, and we find that 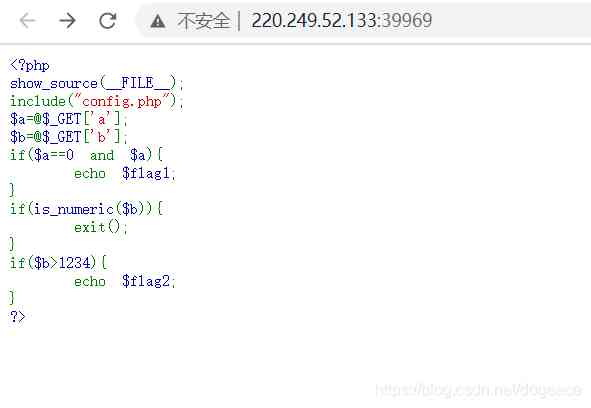 Who am I? Where am I? What happened . Why? a0 a It's not a constant ,b>1234b It's not a number ?? So omnipotent Baidu came out , This involves PHP According to the basic grammar of PHP When a string is valued as a numeric value , The results and types are as follows : If the string does not contain ’.’,’e’,’E’ And its numerical value is in the range of shaping , The string is treated as int To take a value , In all other cases, it is used as float To take a value , The beginning of the string determines its value , If the string starts with a legal value , Then use this value , Otherwise, it's worth 0 Such as :“0e11”"0e22" When comparing , This kind of string will be recognized as the number of science and Technology Law , therefore 0 To the power of zero .“A”==0 When comparing , Will A Convert it to a number , Forced conversion , because A Is string , The result of the transformation is 0 Nature and 0 equal .“1A”==1 When comparing 1A Convert it to a number 1; but “A1“==1 It turns out to be false, That is to say "A1" Transformed into 0.
Who am I? Where am I? What happened . Why? a0 a It's not a constant ,b>1234b It's not a number ?? So omnipotent Baidu came out , This involves PHP According to the basic grammar of PHP When a string is valued as a numeric value , The results and types are as follows : If the string does not contain ’.’,’e’,’E’ And its numerical value is in the range of shaping , The string is treated as int To take a value , In all other cases, it is used as float To take a value , The beginning of the string determines its value , If the string starts with a legal value , Then use this value , Otherwise, it's worth 0 Such as :“0e11”"0e22" When comparing , This kind of string will be recognized as the number of science and Technology Law , therefore 0 To the power of zero .“A”==0 When comparing , Will A Convert it to a number , Forced conversion , because A Is string , The result of the transformation is 0 Nature and 0 equal .“1A”==1 When comparing 1A Convert it to a number 1; but “A1“==1 It turns out to be false, That is to say "A1" Transformed into 0.
So among them a It's converted to when it's cast 0 But it's not a number , Empathy 1234b, The effect is the same . So in URL I'll add ?a=a&&b=12345a Will come to flag

The knowledge involved in this question is PHP The weak type problem of , I don't know much about this as a beginner
This question I also refer to this big man's blog this question solution Blog links It also gives an understanding of PHP Weak type place Learn more PHP Weak type
Question seven get_post
 get,post Are two common ways to send a request So we open the topic
get,post Are two common ways to send a request So we open the topic

The title is simple and clear get send out a=1, So we are URL Followed by ?a=1 send out
 So we're using post send out b=2, Because I'm using Google browser post Request can only be used postman Plugins send , I spent a lot of time working on this plug-in
So we're using post send out b=2, Because I'm using Google browser post Request can only be used postman Plugins send , I spent a lot of time working on this plug-in  Open send post request b=2,
Open send post request b=2,
 Get what we want flag. In fact, there is no difficulty in this question , It's just an investigation get,post The implementation of the . Review two ways to submit forms .
Get what we want flag. In fact, there is no difficulty in this question , It's just an investigation get,post The implementation of the . Review two ways to submit forms .
The eighth question webshell
 The problem of Trojan horse is obvious , This is a very dangerous behavior , For example, I smashed my own house , Never imitate , OK, let's get to the point , Actually, it is to test our use of kitchen knife software . Entering the topic, we find that
The problem of Trojan horse is obvious , This is a very dangerous behavior , For example, I smashed my own house , Never imitate , OK, let's get to the point , Actually, it is to test our use of kitchen knife software . Entering the topic, we find that

The content of Trojan horse is given directly. Let's show our protagonist kitchen knife ,

Click Add to 
Get into html You can see flag

Open to get flag.
For reasons of time , Just let this out for the time being 8 The analysis of the problem , In fact this 8 All the problems involve big knowledge, the most basic part of which is, for example, the eighth question webshell There are many kinds of classifications of , These questions just let us know CTF There's a simple understanding , I also found my own knowledge loopholes when doing these questions , So I hope I can try to improve myself after reading the analysis . I'll post the rest on my next blog , For the first time, I hope you can point out my mistakes .
版权声明
本文为[osc_5emtajt2]所创,转载请带上原文链接,感谢
边栏推荐
- Insight -- the application of sanet in arbitrary style transfer
- The most detailed usage guide for perconaxtradbcluster8.0
- 413【毕设课设】基于51单片机无线zigbee无线智能家居光照温湿度传输监测系统
- Game mathematical derivation AC code (high precision and low precision multiplication and division comparison) + 60 code (long long) + 20 point code (Full Permutation + deep search DFS)
- 数据科学面试应关注的6个要点
- 比Python快20%,就问你兴不兴奋?
- Is blazor ready to serve the enterprise?
- How does spotify drive data-driven decision making?
- shiyou的数值分析作业
- Cloud Alibabab笔记问世,全网详解仅此一份手慢无
猜你喜欢

Wechat nickname Emoji expression, special expression causes the list not to be displayed, export excel error report and other problems solved!

Deeplight Technology Bluetooth protocol SRRC certification services

游戏优化性能杂谈(十一) - 知乎

PCR and PTS calculation and inverse operation in TS stream

413【毕设课设】基于51单片机无线zigbee无线智能家居光照温湿度传输监测系统

Px4 adds new applications

Basic concepts of computer network (5) basic principles of local area network

November 07, 2020: given an array of positive integers, the sum of two numbers equals N and must exist. How to find the two numbers with the smallest multiplication?

ASP.NET A complete solution based on exception handling in MVC

Visual studio 2015 unresponsive / stopped working problem resolution
随机推荐
How can a technician take over a complex system?
Julia 是如何风靡起来的?
python_scrapy_房天下
vivoY73s和vivoY70s的区别 vivoY73s和vivoY70s哪个值得入手
攻防世界之web新手题
Game optimization performance (11) - Zhihu
模板链表类学习
2020-11-05
函数周期表丨筛选丨值丨SELECTEDVALUE - 知乎
IOS learning note 2 [problems and solutions encountered during the installation and use of cocopods] [update 20160725]
M-end software product design considerations - Zhihu
Solve the problem of rabbitmq message loss and repeated consumption
NOIP 2012 提高组 复赛 第一天 第二题 国王游戏 game 数学推导 AC代码(高精度 低精度 乘 除 比较)+60代码(long long)+20分代码(全排列+深搜dfs)
Littlest JupyterHub| 02 使用nbgitpuller分发共享文件
Sum up some useful functions
5g/4g工业无线路由器
FORTRAN77从文件中读入若干数据并用heron迭代公式开方
nvm
November 07, 2020: given an array of positive integers, the sum of two numbers equals N and must exist. How to find the two numbers with the smallest multiplication?
2020-11-05