当前位置:网站首页>5g/4g工业无线路由器
5g/4g工业无线路由器
2020-11-08 08:09:00 【osc_oo6krp7m】
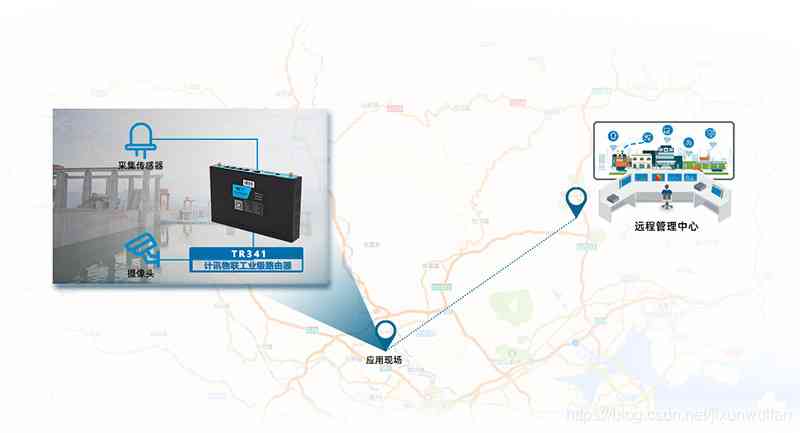
TR341系列工业级路由器可帮助用户快速接入高速互联网,实现安全可靠的数据传输,广泛应用于交通、电力、金融、水利、气象、环保、工业自动化,能源矿产、医疗、农业、林业、石油、建筑、智能交通、智能家居等物联网应用。
工业级物联网无线路由器(又名物联网工业网关),设计完全满足工业级标准和工业用户的需求,采用高性能的工业级32位通信处理器,软件多级检测和硬件多重保护机制来提高设备稳定性。支持中国电信4G/3G,中国联通4G/3G、中国移动4G/3G并往下兼容EDGE、CDMA 1X及GPRS网络,同时支持多种VPN协议(OpenVPN、IPSEC、PPTP、L2TP等)来保证数据传输的安全性。支持RS232(RS485可选)、以太网接口和Wifi功能。






版权声明
本文为[osc_oo6krp7m]所创,转载请带上原文链接,感谢
https://my.oschina.net/u/4400107/blog/4707848
边栏推荐
- FORTRAN 77 reads some data from the file and uses the heron iteration formula to solve the problem
- Search and replace of sed
- Swiper window width changes, page width height changes lead to automatic sliding solution
- 5g + Ar out of the circle, China Mobile Migu becomes the whole process strategic partner of the 33rd China Film Golden Rooster Award
- Blazor 准备好为企业服务了吗?
- iOS上传App Store报错:this action cannot be completed -22421 解决方案
- Visual studio 2015 unresponsive / stopped working problem resolution
- C language I blog assignment 03
- 哔哩哔哩常用api
- Littlest jupyterhub| 02 using nbgitpuller to distribute shared files
猜你喜欢

Learn Scala if Else statement

5g + Ar out of the circle, China Mobile Migu becomes the whole process strategic partner of the 33rd China Film Golden Rooster Award

M 端软件产品设计思虑札记 - 知乎

面部识别:攻击类型和反欺骗技术

These core technology of object-oriented, after you master it, you can have a good interview

Lay UI left tree Dtree right list table

Simple use of future in Scala

Face recognition: attack types and anti spoofing techniques

Cryptography - Shangsi Valley
![[solution] distributed timing task solution](/img/3b/00bc81122d330c9d59909994e61027.jpg)
[solution] distributed timing task solution
随机推荐
Adobe Prelude / PL 2020 software installation package (with installation tutorial)
Qt混合Python开发技术:Python介绍、混合过程和Demo
Wechat nickname Emoji expression, special expression causes the list not to be displayed, export excel error report and other problems solved!
Get tree menu list
leetcode之判断路径是否相交
Qt混合Python开发技术:Python介绍、混合过程和Demo
The road of cloud computing: a free AWS cloud server
Fortify漏洞之 Privacy Violation(隐私泄露)和 Null Dereference(空指针异常)
[original] about the abnormal situation of high version poi autosizecolumn method
nvm
IOS learning note 2 [problems and solutions encountered during the installation and use of cocopods] [update 20160725]
More than 50 object detection datasets from different industries
The real-time display of CPU and memory utilization rate by Ubuntu
PerconaXtraDBCluster8.0 最详尽用法指南
GET,POST,PUT,DELETE,OPTIONS用法与说明
Mouse small hand
归纳一些比较好用的函数
C语言I博客作业03
Face recognition: attack types and anti spoofing techniques
Unparseable date: 'mon Aug 15 11:24:39 CST 2016', time format conversion exception