当前位置:网站首页>A simple SQL injection shooting range exercise
A simple SQL injection shooting range exercise
2022-07-25 08:05:00 【Colorful @ star】
One simple SQL Injection range practice
List of articles
Preface
In order to consolidate SQL Injection and actual combat practice , Let's do a simple about SQL Injected actual range practice
One 、 Target download
Range download address :
https://download.vulnhub.com/pentesterlab/from_sqli_to_shell_i386.iso
the reason being that linux System , You should pay attention to the installation of linux Of Debian System , The system can operate normally , Then place in the settings iso CD is OK .
Once installed , We can carry out target penetration
Two 、 Range penetration
1. Port scanning
We enter the target plane , see ip Address 
ip by 192.168.171.131, After entering kali Do a full port scan , See which ports are open 
Found open 80 port , see 80 Service of port 
Open this page , There's no idea , Next , Take a look at the sensitive information or login page of the source code 
found id Parameter injection page , You can try injection 
Of course , Also found the path of file upload , Click in , It's a picture 
When back to uploads Catalog time , It is found that the page has not been safely set , There are files and pictures , You can also guess that it should be the path and location of file upload 
When back to admin Catalog time , Discovery is a login page , Failed to use weak password , You can only get the user's information by checking the database 
When I checked the source code before, I found id Parameter injection , Whether there is SQL Injection? , So let's test that out , Try putting a single quotation mark
http://192.168.171.131/cat.php?id=1’

Wrong report , Try two more
http://192.168.171.131/cat.php?id=1’’
I found that I also reported wrong , If there is injection , It may not be character injection , But digital injection , There is no single quotation mark , We assume digital injection , Try blind injection with time delay , See if there is SQL Inject
When we type in 1-- when , Back to success
http://192.168.171.131/cat.php?id=1–
We type in
192.168.171.131/cat.php?id=1 and sleep(3)–
Found that the system has been turned 3 Seconds later , And return to another page 
Description is digital injection , And there are SQL Inject , To save time , Direct use sqlmap For injection , Get database information
We just use kali Self contained sqlmap Scanned
sqlmap -u http://192.168.171.131/cat.php?id=1 -batch -dbs

Sweep out this library photoblog, Explain that the user information is in this library , Continue to explode table and field information , In order to view all information directly , Enter all the data directly
sqlmap -u http://192.168.171.131/cat.php?id=1 -batch -D photoblog -dump-all

Found to have 3 Tables , The user information is in the middle users In the table 
Successfully obtain login account and password
admin/P4ssw0rd
Let's go back to the login page to login 

There is a place to upload files in the lower left corner , Go in and have a look 
We tried to upload a picture of a one sentence Trojan horse , obtain shell, I just upload a local file 

After uploading it , Found an error , Because the file name does not meet the length limit , Let's change the length of the file name 

After uploading, I found that php file , Can't upload , So it's filtered .php suffix , We use upper and lower case or double case , Try to bypass .
We change it to hao.php Change it to hao.Php Go around 

Successfully uploaded , Next , Find the image path directly , Just connect with ant sword .
Let's click on the picture to see 
I found that this URL is not a picture path , But the one mentioned before
http://192.168.171.131/admin/uploads/hao.Php
The picture can be opened , We demonize the connection as soon as we see you , obtain shell
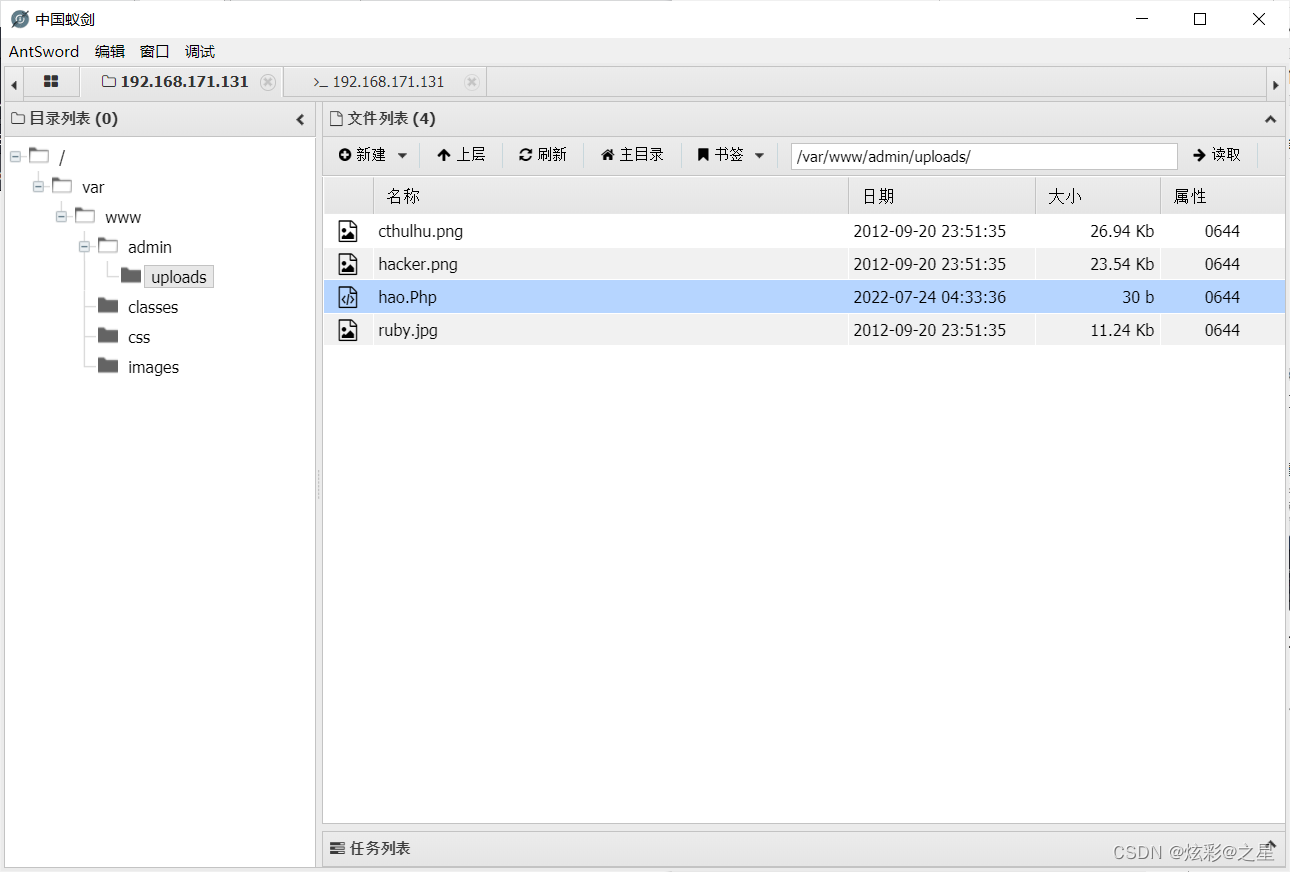
Connect the , Let's open it and have a look 
Check successfully , The target plane is officially penetrated here ,, Mainly practice SQL Application of injection and file upload vulnerabilities , I will continue to work hard later .
summary
The target plane experiment is over , Relatively simple , If you have time later , We are doing a target plane experiment combining external network and internal network penetration , everyone , Work together .
边栏推荐
- The two Nobel Prize winners became the chief scientist of the sky high price Baijiu of "taishanglaojun holding a dream"
- 整数a按位取反(~)后的值为-(a+1)
- 机器学习理论及案例分析(part1)--机器学习基础
- [unity introduction program] basic concept - preform prefab
- 【FFmpeg】mp4转yuv
- 【音视频】图片YUV数据格式
- [unity introduction program] basic concepts GameObject & components
- efcore在Saas系统下多租户零脚本分表分库读写分离解决方案
- C# 43. 获取UDP可用端口
- Can Flink's current capabilities support the synchronization of a table from source (MySQL) to sink (MySQL) to separate databases and tables
猜你喜欢
Advanced C language (XIII) - Example Analysis of dynamic memory management
P1086 [noip2004 popularization group question 2] peanut picking

Raspberry connects EC20 for PPP dialing

VS2019 C# MFC安装

Vs2019 C MFC installation

Introduction and principle explanation of 30 common sensor modules in IOT embedded devices

Today in history: Intel was founded; The first photo was posted on the world wide web; EBay spins off PayPal

CAS操作

How to create a simple electron desktop program

App power consumption test
随机推荐
Problems easily ignored by POM
P1047 [NOIP2005 普及组 T2] 校门外的树
475-82(230、43、78、79、213、198、1143)
enq: HW – contention等待引起的故障分析
Interview questions: common faults and occurrence scenarios of redis
7.24模拟赛总结
Raspberrypico analytic PWM
Didi eta (estimate the travel time)
If Debian infringes the rust trademark, will it be exempted by compromising and renaming?
[paper notes] next vit: next generation vision transformer for efficient deployment in real industry
由两个栈组成的队列
Changes were made to tables that cannot be recreated or the prevent saving changes that require the table to be recreated option was enabled
Teach you to understand the computer optometry sheet
One of C language multithreading programming
Raspberry connects EC20 for PPP dialing
Network file storage system (II) practical operation of Minio distributed file system
Redis core principles
C# 43. 获取UDP可用端口
Dijkstra序列(暑假每日一题 5)
[QNX hypervisor 2.2 user manual]9.3 CPU
![P1086 [noip2004 popularization group question 2] peanut picking](/img/f0/5c311d1fb1e320a29cbcbc05d2f334)