当前位置:网站首页>Penetration test target combat SQL injection getshell
Penetration test target combat SQL injection getshell
2022-07-25 04:05:00 【yummy11111】
SQL Inject getshell
- The host found ( Check the number of surviving addresses in the same network segment )( Use kali Tools in zenmap)
You can see that there are four hosts scanned , among 16 It's physical IP,39 yes kali Of ip,18 It's an unknown host , notice 192.168.197.138 It is a virtual machine host , in the light of 138 Do port probing
- Yes 192.168.197.138 Perform a fast port scan
You can see that the open ports are ssh22 Ports and http80 port , Ports can be used
- ( Don't go backstage first ) Use the weak password tool to 22 Port simple detection :
( Use the super weak password checking tool ) It can be seen that the password is not scanned , So I can't ssh Connect , So the next normal visit 80 port
- visit :( You can see that it is a normal website page )
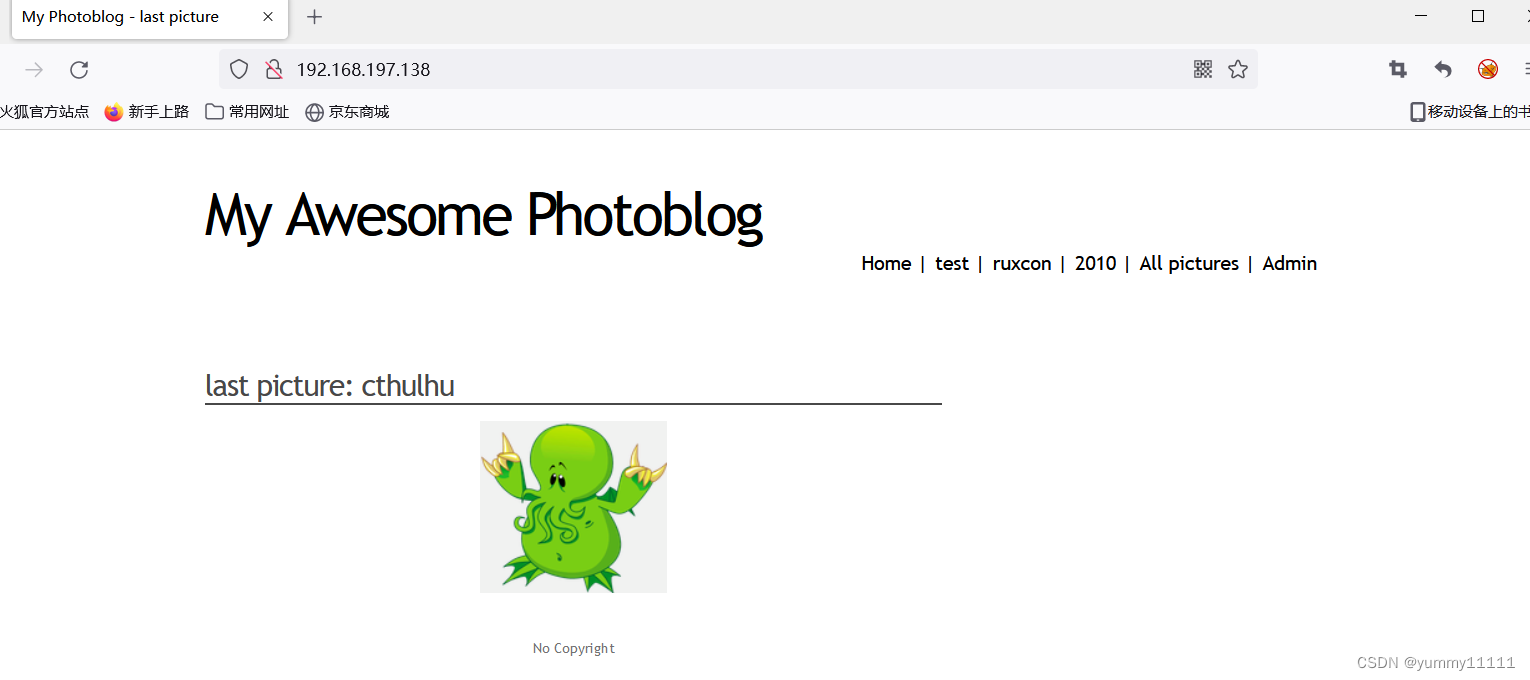
- You can find a background login page : Try weak password cracking
bp Grab the bag and run to the dictionary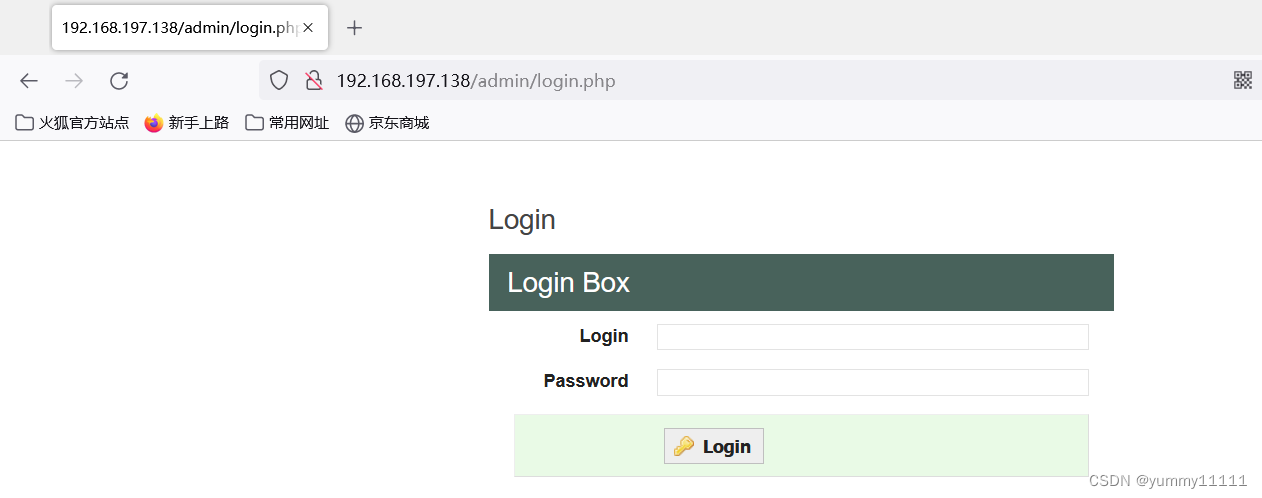
- It can be seen that it is transmitted in clear text , You can try brute force :

- Put it in repeater You can see that the response status is 302, Indicates a jump


- Blasting :( You can find , There is no result of explosion ) Try something else

Check whether there are injection points : First, I see an injection point :http://192.168.197.138/cat.php?id=1
Use common ideas and 1=1 and 1=2 Determine if there is an injection point :
You can see and 1=1 Return to the normal page , and and1=2 The error page is returned

- Use sqlmap To test :
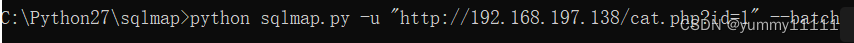
You can see that the detected database is MySQL database
The existing injection point is id
First try :
Find no way
Try :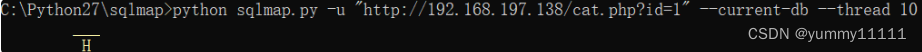
You can see The current database is :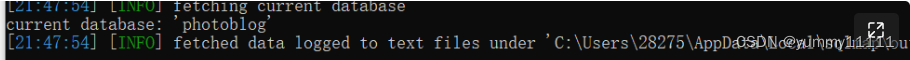
Get the database name , Then look up the table name :
You can find three table names in the database :
After getting the table name , Find column (users surface )
You can see that the column names include id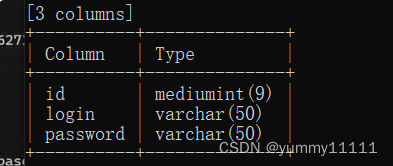
Run user name and password :
You can see the last user name and password
After getting the user name and password, log in backstage :
See an upload point :
Upload a one sentence Trojan horse :
open bp Carry out the bag , You can see that uploading is not allowed php file :
You can try to modify content-Type:image/jpeg;
It is found that the modification is still not possible :
Try case bypass : Found upload successful


But we don't know the upload path , Next, find the path
See the picture ,f12 Review element ; You can see that there is an absolute path :
Yes url Splicing :
You can see that the whole page is white , It shows that it has succeeded

Use the ant sword to connect :
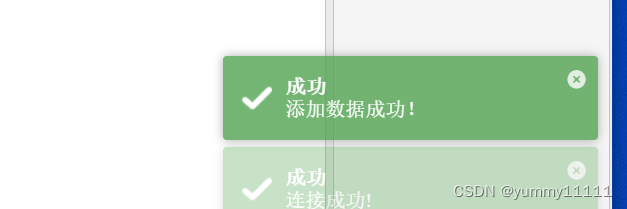
success getshell
To test :( Successfully viewed IP)
summary : Mainly through sql Inject vulnerability and log in to the background , Then upload the Trojan file , Use case to bypass uploading , Finally, use the ant sword link webshell, Finally, I got shell
边栏推荐
- Servlet个人实操笔记(一)
- Interview question 05.06. integer conversion
- Roleapp focuses on Web3 and opens the door of Web3 with the key of "data can be held"
- Oracle uses FY_ recover_ Data recover truncate deleted data
- [kaggle] how to effectively avoid oom and the long process of alchemy
- [Flink] transform operator filter
- Max matrix and JS
- To clarify the tax arrears: there is no tax arrears, and will continue to operate in compliance, rooted in China
- Localization distillation for dense object detection cvpr2022
- "Introduction to interface testing" punch in to learn day04: how to abstract the procedural test script into a test framework?
猜你喜欢

Student thinking vs workplace thinking
Emergency response stack

Moveit2 - 8. Motion planning API

You are only one SQL statement away from the tdengine Developer Conference!

How should enterprise users choose aiops or APM?
![[Flink] submit the jar package to the Flink cluster and run it](/img/9b/076949a4b9fe75ee248c400ee21474.png)
[Flink] submit the jar package to the Flink cluster and run it

Traditional architecture of enterprise digital transformation to medium platform micro service architecture

Pytorch deep learning practice lesson 8 importing data

Network security - information hiding - use steganography to prevent sensitive data from being stolen
.net6 miniapi (V): Options
随机推荐
弹性布局(display:flex下 align-content、justify-content、align-items三个属性的作用和效果
Servlet个人实操笔记(一)
300. Longest increasing subsequence
Roleapp focuses on Web3 and opens the door of Web3 with the key of "data can be held"
MySQL
基于SSH婴幼儿产品销售系统
Codewars notes
Creativity: presentation of AI oil paintings with high imitation mineral pigments
Hbuilderx eslint configuration
An article takes you quickly to learn flex layout
What are the models of asemi from the manufacturer of rectifier bridge and how about the electroplating process of the manufacturer of rectifier bridge?
Multithreading advanced Step2
[file upload] parse text files and store them in batches through JDBC connection (dynamic table creation and dynamic storage)
Spirng security (VIII) multiple filter chains coexist
13. Talk about the expiration strategy of redis
考研经历
Nested if selection structure and switch selection structure
Bond network card mode setting
Oracle uses FY_ recover_ Data recover truncate deleted data
Debezium series: when there are a large number of DML operations in the record source database, the debezium consumption data time lags behind the data generation time by several hours