当前位置:网站首页>Data-driven anomaly detection and early warning of item C in the May 1st mathematical modeling competition in 2021
Data-driven anomaly detection and early warning of item C in the May 1st mathematical modeling competition in 2021
2022-06-25 09:26:00 【Building block mathematical modeling】
2021 May 1st Mathematical Modeling Contest C topic Data driven anomaly detection and early warning
C topic Data driven anomaly detection and early warning
Original high-quality ideas Identify us The links below

High quality 、 original 、9.9 that will do Official account number 5 Discount sale
link :
https://mianbaoduo.com/o/bread/YZmVlJdw
C topic Data driven anomaly detection and early warning
Data description :100 A sensor 24 Hour time series data ( No data name given )

Data description diagram
Data processing :100 A sensor , Do not know the data name , It is necessary to filter variables . The first calculation is 100 The Euclidean distance between columns is clustered and then filtered . This is the simplest , An effective plan .
to update 1: Data processing 100 Column data to do matlab Of cluster Dimension reduction ,matlab Of cluster The function seems to have failed ( Maybe the dimension is high ) I don't know why , Still use here R Language helps us do well , Directly send the data set with good dimensionality reduction .
to update 2:pdist Function can solve , No correlation coefficient . Be careful , The data dimensionality reduction here should not be standardized 、 normalization , Not much to explain . The results are placed below , Just select a few of each class as the new data set , The code and data results will be sent soon .
We use the code Get the... After data processing 10 Column ( Relatively independent data ) after , Take a brief look at their trends and characteristics :

It can be seen that , The processed data has its own characteristics , It shows that our processing method is basically reliable ( For reference only ).
According to the above time series ( chart ) It can be seen that , It basically conforms to the properties given in the title : Such as the independent point of the picture in the lower right corner , The periodicity of the Chinese pictures on the .
Question 1 : Establish risk abnormal data detection model ( Give an assessment of risk and non risk )
According to the picture above , The above four properties of the time series of detection data are analyzed one by one
The following reference scheme is given :
1. Non risk outliers detection
Be careful ! There are some conceptual distinctions , The abnormal data of this problem has the same name as the abnormal value detection in machine learning , When you search for information, you should pay attention to distinguish , The abnormal data in this article refers to the logical abnormality of the sensor .
programme 1 ) The abnormal value is judged as non risk by a separate column ( It's not very realistic , According to the meaning of the topic , Just for learning )
The title mentioned that there will be independent points in the time series , Is one of the characteristics of non risk . Therefore, the first step in the abnormal data monitoring model is to remove the abnormal points of individual columns , Use simple outlier detection .( Single column outlier elimination )
programme 2*) The global outliers judge that the outliers are non risk
Fluctuations in the sensor - Outliers , There may or may not be risks , Fluctuations caused by changes in the external environment , We think it is risk-free , If at some point ...........................
边栏推荐
- [design completion - opening report] zufeinfo 2018 software engineering major (including FAQ)
- 备战2022年金九银十必问的1000道Android面试题及答案整理,彻底解决面试的烦恼
- Jmeter接口测试,关联接口实现步骤(token)
- 35 websites ICER must know
- 五、项目实战---识别人和马
- Voiceprint Technology (III): voiceprint recognition technology
- [opencv] - input and output XML and yaml files
- Webgl Google prompt memory out of bounds (runtimeerror:memory access out of bounds, Firefox prompt index out of bounds)
- 自定义注解之编译时注解(RetentionPolicy.CLASS)
- [learn C from me and master the key to programming] insertion sort of eight sorts
猜你喜欢

C language: count the number of words in a paragraph
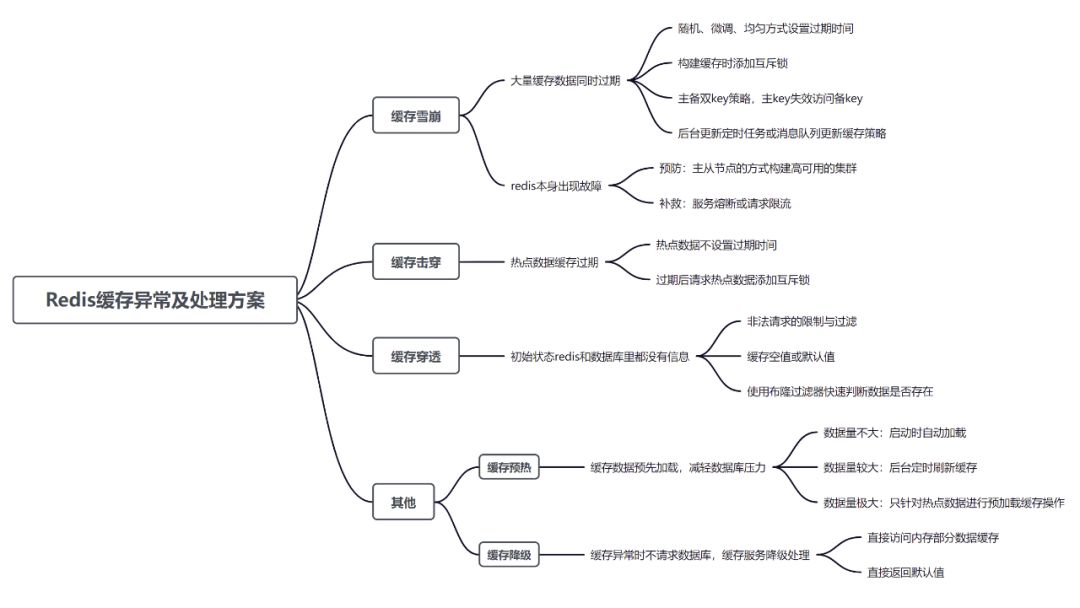
3 big questions! Redis cache exceptions and handling scheme summary

matplotlib matplotlib中axvline()和axhline()函数

Cassava tree disease recognition based on vgg16 image classification

关掉一个线程
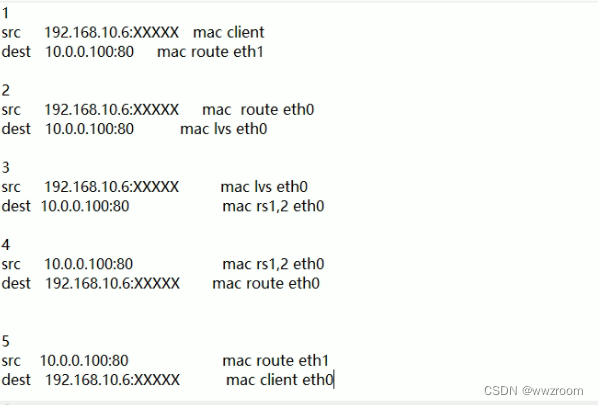
Lvs-dr mode single network segment case

On the underlying index principle of MySQL

Summarize two methods of configuring pytorch GPU environment

Nodejs using the express framework demo
![[design completion - opening report] zufeinfo 2018 software engineering major (including FAQ)](/img/b7/fb7ead787e00047f3663e8b5acfe33.jpg)
[design completion - opening report] zufeinfo 2018 software engineering major (including FAQ)
随机推荐
3、 Automatically terminate training
[opencv] - input and output XML and yaml files
《乔布斯传》英文原著重点词汇笔记(二)【 chapter one】
Close a thread
35 websites ICER must know
Register the jar package as a service to realize automatic startup after startup
Nodejs using the express framework demo
C language: count the number of words in a paragraph
Emergency administrative suspension order issued Juul can continue to sell electronic cigarette products in the United States for the time being
Atguigu---01-scaffold
Where are the hotel enterprises that have been under pressure since the industry has warmed up in spring?
浅谈Mysql底层索引原理
【OpenCV】—输入输出XML和YAML文件
Is it safe to open an account with Great Wall Securities by mobile phone?
Jmeter接口测试,关联接口实现步骤(token)
《乔布斯传》英文原著重点词汇笔记(一)【 Introduction 】
Is it safe for Huatai Securities to open an account on it? Is it reliable?
Is it safe to open an account online? Who can I ask?
Is it safe to open an account in a mobile phone or a securities company?
203 postgraduate entrance examination Japanese self-study postgraduate entrance examination experience post; Can I learn Japanese by myself?