当前位置:网站首页>Realization of a springboard machine
Realization of a springboard machine
2022-06-28 10:14:00 【InfoQ】
One 、 Introduction to the idea of springboard machine
- Linux The server
- Windows The server
- Other terminals (MySQL terminal 、Redis terminal 、 Network equipment terminal wait )
Two 、 Background knowledge
2.1 Linux Of PAM Mechanism

2.2 PAM The core competencies of

2.3 PAM Module type
- auth
- account
- session
- password
2.4 common PAM modular
- pam_unix.so modular
- pam_cracklib.so modular
- pam_loginuid.so modular
- pam_securetty.so modular
- pam_rootok.so modular
- pam_console.so modular
- pam_permit.so modular
- pam_env.so modular
- pam_xauth.so modular
- pam_stack.so modular
- pam_warn.so modular
3、 ... and 、 Springboard system architecture
3.1 Microservices and high availability design
3.1.1 Microservice design
- monitor 8080 port , Provide http Interface capabilities
- Verify whether an account exists and is normal
- Verify whether an account has login permission to a server
- Verify whether an account has a connection to a server sudo jurisdiction
- Data pulling : account number 、 host 、 Dangerous command library, etc
- yes jmp The only access to the database
- monitor 2200 port , Provide ssh Agency ability
- Direct access to Linux The server 、 Other terminals
- monitor 8080 port , Provide websocket/socket.io Connection ability
- adopt ssh Protocol forwarding socket.io Flow to jmp-ssh
- Support the connection and access of Web terminal
- monitor 8080 port , Provide socket.io Connection ability
- Realization rdp agent , For ease of operation Windows The server
- Support web based Remote Desktop Services
- Provide file upload and download capabilities , Support in jmp Pass through sftp command , Support any sftp Client connection
- visit S3, To access files
- Deployed on every Linux Server
- jmp-agent Resident process
- jmp special pam modular
3.1.2 High availability design
3.2 Interaction diagram of each sub service of the springboard machine

Four 、 Core design ideas
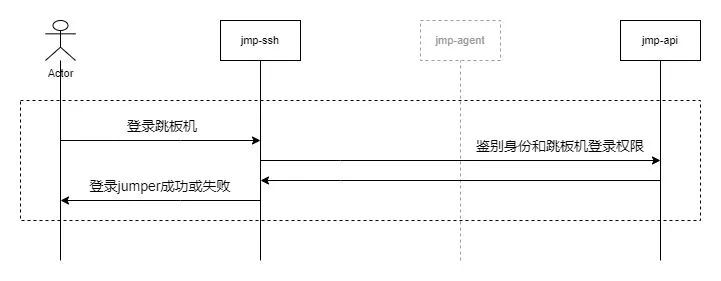
4.1 Log on to the skip machine
- The user to use ssh The client logs in to jmp-ssh service , And jmp-ssh Service interaction .
- jmp-ssh Access to services ssh Account number during session establishment 、 Password after encryption 、 Secondary authentication information .
- jmp-ssh Service access jmp-api service , Submit account number 、 Password after encryption 、 Secondary authentication information , In order to know whether the user is logged in jmp Authority .
4.2 Log in to the target server
- Only if the user has logged in to jmp-ssh Or it has passed jmp-socket You can log in to the target server only after the front-end authentication of .
- The user is in jmp-ssh Pseudo terminal input provided ssh xxxx(xxxx Is the host name of the target server or IP Address ).
- jmp-ssh adopt ssh Connect to target server , Automatically carry user name information , Try to establish a session .
- Due to... On the target server jmp-agent Took over sshd Identification and authority authentication , therefore jmp.so obtain ssh User name during session establishment , The user name and the local computer IP Address information encryption , call jmp-api Interface for authority authentication .
- jmp-api According to the built-in policy , And query authorization table , Determine whether the user has login permission to the machine .
- jmp-agent Get the authentication result , For those who have authority , be ssh Session successfully established , Otherwise, the session establishment fails .
- jmp-ssh Get the result and reason of session establishment , Return to the user ssh terminal .

4.3 Command interaction
- Only if the user has logged in to a machine , To command interaction .
- When the user ssh Typing characters on the client , Pass on to jmp-ssh,jmp-ssh Determine whether the statement ends .
- When statement ends , be jmp-ssh According to the dangerous order rules of the machine , Match statements entered by the user , Decide to alarm 、 Intercept 、 adopt .
- jmp-ssh Pass the passed statement or the statement requiring alarm to the target server , The target server executes and returns the result .

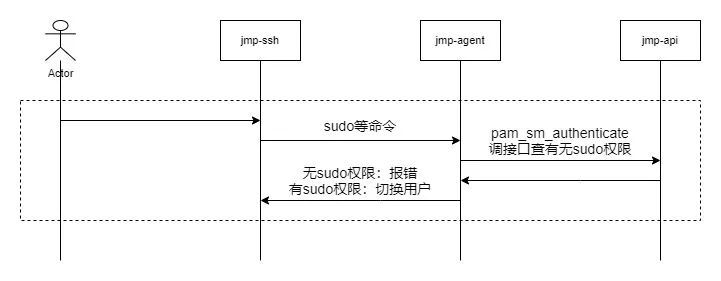
4.4 Switching users / Privileged account
- Only if the user has logged in to a machine , It is possible to trigger the behavior of switching users .
- When the user ssh Client execution sudo xxxx、su、id And so on ,jmp-ssh Transparently transmit commands to the target server .
- On the target server sshd Process execution sudo xxxx、su、id And so on command , Because the target server has been jmp-agent Took over identity failure and authority authentication , Therefore, from jmp.so Get login user name 、 Current user name 、 Local address information 、 Target user name information , transfer jmp-api Interface for sudo Permission authentication .
- jmp-api Judge whether the user has the right to switch the machine to xx Account permissions ( If there is root jurisdiction ).
- sudo、su、id Wait for the process to pass jmp.so The authentication result is obtained , Decide whether to switch users .
4.5 Use web interaction
- Only if the user has completed login through the web page ( Such as sso) The situation of .
- Users access through web pages jmp-socket service .
- jmp-socket Service to get user name information 、 Website login sso Information , Submit to jmp-api, Generate a temporary login credential .
- jmp-socket visit jmp-ssh, Submit temporary login credentials .
- jmp-ssh Initiate secondary authentication for login , Wait for the user to complete the secondary authentication .
- jmp-socket After the user completes the second authentication , To undertake the ssh Role of client , And jmp-ssh Interaction .

4.6 Dangerous command interception
- jmp-ssh After the user has logged in to the target server , In this session , Load the dangerous command rules of the corresponding service of the target machine , Initialize regular matching logic .
- jmp-ssh At the end of the user input statement , According to the dangerous order rules of the machine , Match statements entered by the user .
- jmp-ssh Match the post strategy according to the dangerous command rules , Decide to do the following for this input : The alarm 、 Intercept 、 adopt .
- For passing ,jmp-ssh Pass the command to the target server .
- For alarm ,jmp-ssh Pass the command to the target server , But to the user 、 The immediate leader of the user 、jmp The system administrator sends a danger command alarm .
- For intercepted ,jmp-ssh Refuse to pass command , At the same time, the user 、 The immediate leader of the user 、jmp The system administrator sends a danger command alarm .

4.7 Not Linux The springboard of the server
- Windows The server
- MySQL Terminals and Redis terminal
- Network device management terminal
5、 ... and 、 Permission rules and approval link design
5.1 Default permissions
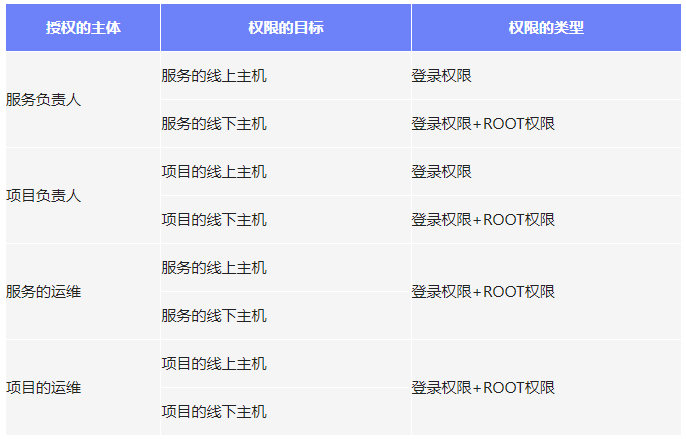
5.2 Approval link of permission application
- If you don't have default permissions , But you need to log in to the machine , Or you need to use ROOT jurisdiction , You need to apply .
- If you apply for permission for an organization , Then the organization ( department ) All members have the permission to apply for locks .

6、 ... and 、 The advantages of this realization idea
6.1 It is easy to operate , Better experience
6.2 Safe and reliable , Easy to audit
6.3 The responsibilities of the service room are clear
7、 ... and 、 Summary and prospect
边栏推荐
- Install using snap in opencloudos NET 6
- Django数据库操作以及问题解决
- Resolution: overview of decentralized hosting solution
- Proxy mode (proxy)
- Is it safe to open an account with the QR code of CICC securities? Tell me what you know
- HDI blind hole design, have you noticed this detail?
- Starting from full power to accelerate brand renewal, Chang'an electric and electrification products sound the "assembly number"
- Settings of gift giving module and other custom controls in one-to-one video chat system code
- 满电出发加速品牌焕新,长安电动电气化产品吹响“集结号”
- 理想中的接口自动化项目
猜你喜欢

纵观jBPM从jBPM3到jBPM5以及Activiti
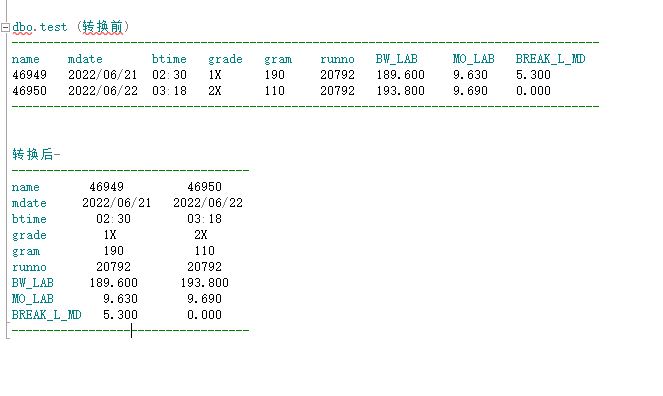
如图 用sql行转列 图一原表,图二希望转换后
![[Unity]内置渲染管线转URP](/img/a5/3ae37b847042ffb34e436720f61d17.png)
[Unity]内置渲染管线转URP
JVM family (2) - garbage collection

通过PyTorch构建的LeNet-5网络对手写数字进行训练和识别

学习机器学习的最佳路径是什么

As shown in the figure, the SQL row is used to convert the original table of Figure 1. Figure 2 wants to convert it

Interface automation framework scaffolding - Implementation of parametric tools

解析:去中心化托管解决方案概述

What is the best way to learn machine learning
随机推荐
MySQL的开发环境和测试环境有什么区别??
Install using snap in opencloudos NET 6
[unity][ecs] learning notes (III)
To enhance the function of jupyter notebook, here are four tips
How to view the web password saved by Google browser
谁知道在中信建投证券开户是不是安全的
Google open source dependency injection framework Guice Guide
Solve the problem that the value of the action attribute of the form is null when transferring parameters
[NLP] this year's college entrance examination English AI score is 134. The research of Fudan Wuda alumni is interesting
Idea failed to connect to SQL Sever
PHP curl forged IP address and header information code instance - Alibaba cloud
Naming rules and specifications for identifiers
PMP examination key summary VIII - monitoring process group (2)
Please consult me. I run the MYSQL to MySQL full synchronization of flykcdc in my local ide. This is in my local ide
一文读懂 12种卷积方法(含1x1卷积、转置卷积和深度可分离卷积等)
PyGame game: "Changsha version" millionaire started, dare you ask? (multiple game source codes attached)
错过金三银四,找工作4个月,面试15家,终于拿到3个offer,定级P7+
Chapter 5 trees and binary trees
Why does istio use spirit for identity authentication?
Explain final, finally, and finalize