当前位置:网站首页>API supplement of JDBC
API supplement of JDBC
2022-07-25 10:54:00 【Hua Weiyun】
Four 、ResultSet
ResultSet( Result set object ) effect :
1. Encapsulates the DQL The result of the query statement
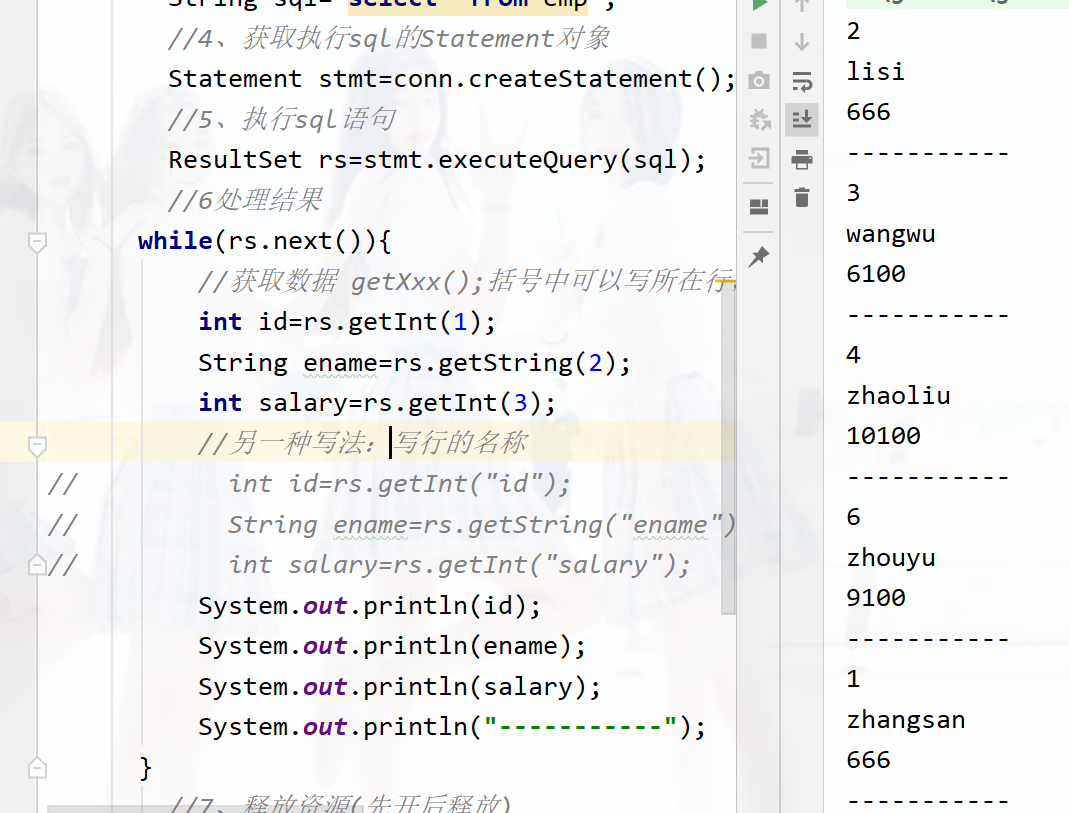
ResultSet stmt.executeQuery(sql): perform DQL sentence , return ResultSet object
Get query results
boolean next():(1) Move the cursor forward one line from the current position (2) Judge whether the current line is a valid line
Return value : The current row has data returned true, There is currently no data returned false.
xxx getXxx( Parameters ): get data
explain :xxx Represents the data type ; Such as int getInt( Parameters );String getString( Parameters );
Parameters : about int Is the number of the column , from 1 Start , about String Is the name of the column .
Use steps :
1、 Move the cursor down one line , And judge whether the line has data :next()
2、 get data :getXxx( Parameters )
Example :
example :
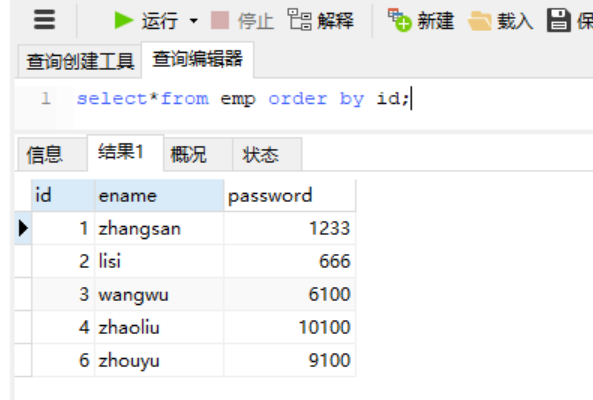
In the database emp surface
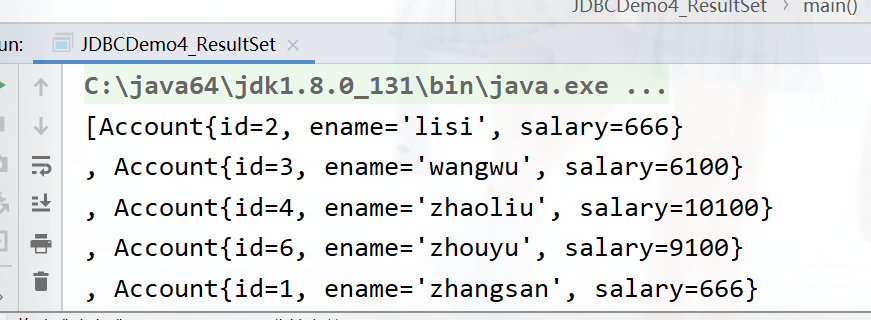
After running :
ResultSet Case study
demand : Inquire about account Account data , Encapsulated in the Account In the object , And store it in ArrayList Collection
Create a pojo package , Used to store objects .
Created a class , Provide getSet Method
jdbc In the class created under the package
Running results :
5、 ... and 、PreparedStatement
PreparedStatement effect :
1、 precompile SQL Statement and execute : The prevention of SQL Injection problem
SQL Inject
SQL Injection is to modify pre-defined by operating input SQL sentence , The method used to execute code to attack the server .
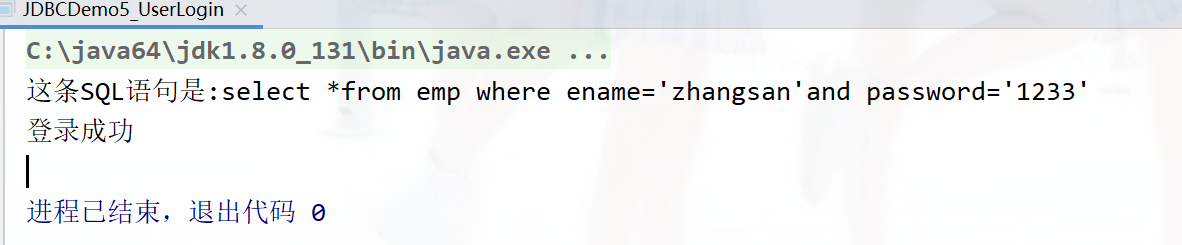
Demonstrate normal login :
First, data record kc_db1 Under the emp The table is :
Running results :
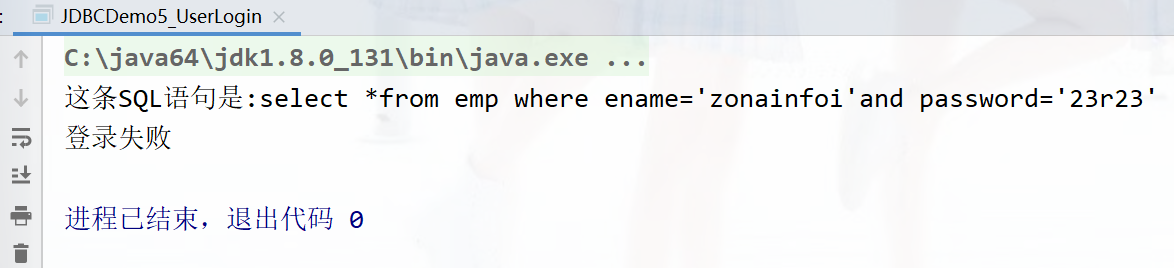
Enter other ( The reason for the failure is that there is no account with this password in the database ):
sql Inject Demo :
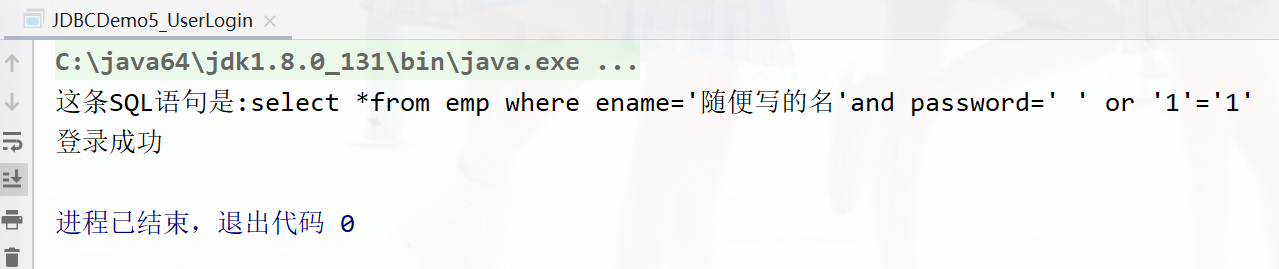
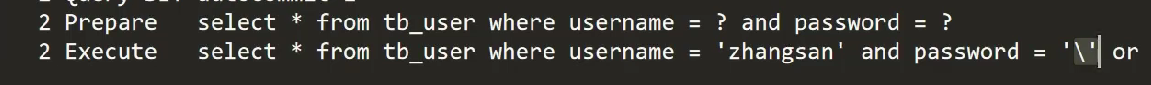
For this article sql It's not about passwords , Any account number
Running results :
This article SQL The sentence is :select *from emp where ename=' A casual name 'and password=' ' or '1'='1'
sql The essence of injection is to change the original SQL sentence , Join in or after 1=1 Always true , So this sentence is true
PreparedStatement solve SQL Inject
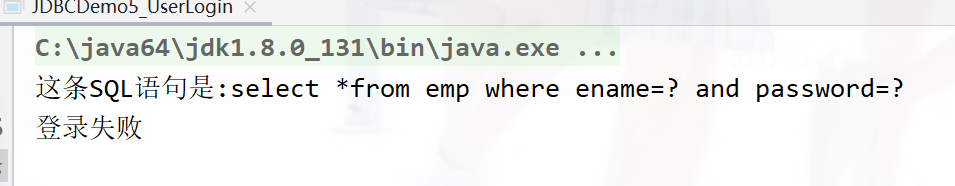
① obtain PreparedStatement object
② Set parameters
PreparedStatement object :setXxx( Parameters 1, Parameters 2): Expressed as a parameter 1(? The location of ) Assign value to parameter 2
Xxx: data type ; arbitrarily setInt( Parameters 1, Parameters 2)
Parameters :
- Parameters 1: Express ? Location number of , from 1 Start
- Parameters 2: ? Value
③ perform sql
executeUpdate();/excuteQuery(); There is no need to pass... In parentheses sql.
Create a class :
Running results :
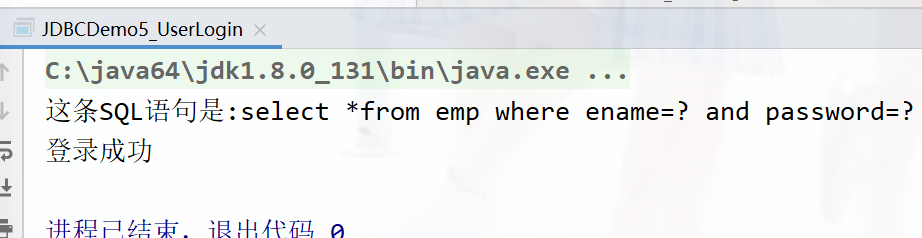
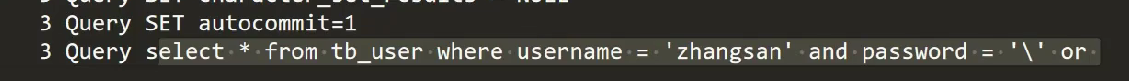
This prevents sql Inject ,setXxx The parameters passed in will be escaped , Not spliced into strings, but \' or\ ' 1\' = \' 1\'
Enter the correct :
PrepareStatement principle
PrepareStatement benefits :
1、 precompile SQL, Higher performance
2、 prevent sql Inject .
my.ini The configuration file can see the log
The precompile function is off by default
①:PreparedStatement Precompile function Turn on :userServerPrepStmts=true
stay sql sentence ? Then write the parameters
When you open it, you will prepare precompile :
After closing, there is no Prepare Stage
边栏推荐
- Install MySQL database version 5.7.29 under ubuntu20.04 system
- After switching the shell command line terminal (bash/zsh), CONDA cannot be used: command not found
- UE4 external open EXE file
- I wrote code for openharmony, and the second phase of "code" pioneer officially opened!
- HCIA实验(06)
- 思路再次完美验证!加息临近,趋势明了,好好把握这波行情!
- 一文读懂小程序的生命周期和路由跳转
- Set up lnmp+discuz Forum
- 2021 去哪儿网笔试总结
- Flask framework - flask WTF form: data validation, CSRF protection
猜你喜欢

100W了!

Flask框架——flask-caching缓存
![[Blue Bridge Cup training 100 questions] scratch Taiji diagram Blue Bridge Cup scratch competition special prediction programming question centralized training simulation exercise question No. 22](/img/d5/56173050f62d5b6fa336ff8d257fca.png)
[Blue Bridge Cup training 100 questions] scratch Taiji diagram Blue Bridge Cup scratch competition special prediction programming question centralized training simulation exercise question No. 22

JS hash table 02

Flask框架——Flask-WTF表单:文件上传、验证码

Acquisition and compilation of UE4 source code

我,AI博士生,在线众筹研究主题

2021 去哪儿网笔试总结

Analysis of event channel principle in Kraken

After switching the shell command line terminal (bash/zsh), CONDA cannot be used: command not found
随机推荐
AI系统前沿动态第43期:OneFlow v0.8.0正式发布;GPU发现人脑连接;AI博士生在线众筹研究主题
【信息系统项目管理师】思维导图系列精华汇总
4. Children next door will know all kinds of shell symbols {}[], etc
Voxceleb1 dataset Download
异步Servlet在转转图片服务的实践
【高并发】如何实现亿级流量下的分布式限流?这些理论你必须掌握!!
VLAN configuration and application (take Huawei ENSP as an example)
MySQL offline deployment
Qt | 鼠标事件和滚轮事件 QMouseEvent、QWheelEvent
推荐系统-协同过滤在Spark中的实现
HCIP(13)
Flask框架——消息闪现
String longest common prefix
微波技术基础实验一 滤波器的设计
8. SHELL file processing Three Musketeers sed
2021 致景笔试总结
Several common network diagnostic commands
Fastdfs offline deployment (Graphic)
树形动态规划
云原生IDE:iVX免费的首个通用无代码开发平台