当前位置:网站首页>F5 application strategy status report in 2022: edge deployment and load security become the focus of attention in the Asia Pacific Region
F5 application strategy status report in 2022: edge deployment and load security become the focus of attention in the Asia Pacific Region
2022-06-23 15:20:00 【TechWeb】
【TechWeb】6 month 23 Daily news , In the near future ,F5 Released for IT Annual survey report of decision makers 《2022 Annual application strategy status report 》, It reveals several cutting-edge trends in the field of application security and delivery , It also interprets the challenges and technologies that enterprises are facing .
Respondents from the Asia Pacific region are “ The most exciting technology ” This choice will be related to security technologies . Survey results show that , The mainland of China and the Hong Kong Special Administrative Region of China, etc Web The application and API protective (WAAP) Showing a higher interest .
last year ,48% Our enterprises pay more attention to vulnerability management and automation . Other key strategies include cloud security 、 Strengthen staff training and integrate safety manufacturers . future , Most enterprises will need to integrate the above strategies to effectively manage the risk of security vulnerabilities .
Worldwide , More than four fifths of the respondents (84%) Plan to deploy the workload to the edge , To enhance the employee and customer experience . Compared with the results of last year's survey , The edge deployment in the Asia Pacific region is showing an overall growth trend .
According to the report , Among the many available application security and delivery technologies , Identity and access management technologies are now the most common , by 96% Deployed by the enterprise . This change is surprising , Because the previous enterprises preferred availability technologies such as load balancing SSL VPN And firewall .
According to the analysis of the report, identity and access management technologies are highly sought after , To some extent, it reflects the popularity of zero trust security and the sharp increase in the number of remote office workers in the past two years , But it is mostly due to the microservices that can access the application at present 、 Script 、 sensor 、 The number of workloads surged . In the context of application and its supporting technology ,“ user ” The definition of has gone far beyond equipment ( Even mobile devices ) The user's concept . therefore , Most or all security solutions are moving towards identity based management , For the user ( Unlikely to be an employee , And more likely API、 Service or machine ) Do security authorization .
Besides , The whole traditional security service is second only to identity service , Is the second most commonly deployed technology , Availability technology ranks third .90% Of enterprises have deployed the above three services , have other 85% Of enterprises have deployed application delivery technology , Designed to improve performance .
边栏推荐
- How to solve the problem that iterative semi supervised training is difficult to implement in ASR training? RTC dev Meetup
- 2021-05-08
- JS中的pop()元素
- Arrays in JS
- JS创建一个数组(字面量)
- golang--文件的多个处理场景
- php 二维数组插入
- Idea view View the class file idea Class folder
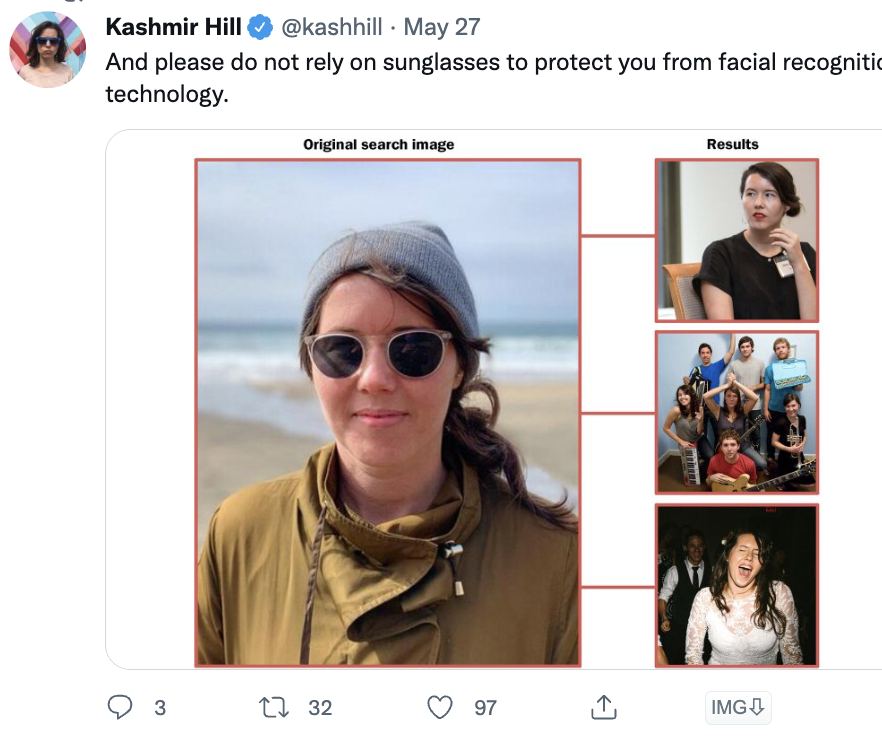
- The well-known face search engine provokes public anger: just one photo will strip you of your pants in a few seconds
- Selenium Edge的IE模式
猜你喜欢
随机推荐
【DataHub】LinkedIn DataHub学习笔记
力扣解法匯總513-找樹左下角的值
Pyqt5 工具盒使用
MySQL advanced statement I
进销存软件排行榜前十名!
期货怎么开户安全吗,期货手续费哪家期货公司比较低,适合散户开户?
An idea plug-in for automatically generating unit tests
Use of pyqt5 tool box
《墨者学院——SQL手工注入漏洞测试(MySQL数据库)》
快速排序的简单理解
JS garbage collection
RF Analyzer Demo搭建
Google &huggingface| zero sample language model structure with the strongest ability
PHP指定字段大于100正序排,小于100随机排
中国矿大团队,开发集成多尺度深度学习模型,用于 RNA 甲基化位点预测
Tencent ECS failed to send email
去 OPPO 面试, 被问麻了。。。
The new version of Alibaba Seata finally solves the idempotence, suspension and empty rollback problems of the TCC mode
Effect evaluation of regression model under credit product quota pricing scenario
Ie mode of selenium edge