当前位置:网站首页>Penetration testing knowledge - industry terminology
Penetration testing knowledge - industry terminology
2022-07-24 05:38:00 【Net security beginner】
Penetration testing knowledge --- Industry jargon
information gathering :ping、nmap、netcraft、curl、whois
Web Application vulnerability scanning :AWVS、Appscan、burp suite
System vulnerability scanning :Nessus
Elevated privileges :Mecasploit Framework

Manual testing
Test items :SQL Inject 、 Cross-site scripting attacks (XSS)、 Cross-site request forgery (CSRF)、 Server request forgery (SSRF)、XML External entity attacks (XXE)、CRLF Inject 、 Upload any file 、 Any file next station / Read 、 Catalog / path traversal 、 Leakage of sensitive information 、URL Redirect 、 Remote command execution 、 Weak password 、 Plaintext transmission, etc .


The system we control 、 Program 、 But if the other party doesn't know, it's called a meat machine .
Remote control , Remotely control each other's computers
Web Trojan :
Insert your own code directly into the normal web page file , When someone comes to visit , Web Trojans will use each other's browsers or systems Vulnerability automatically downloads the configured Trojan horse directly to the visitor's computer for execution .
Black Pages :
After the hacker invaded the computer , In order to prove his existence , Modify the homepage of the website , Thus leaving the attacker's information , This kind of web page is usually called black page .( Generally, hackers are not stupid enough to do this )
Hang a horse :
Is to put the webpage Trojan horse into the website file of the person , Or sneak your own code into each other's files , In order to make the viewer in the horse (js Script loading )
Malaysia :
It's a powerful Trojan horse , Can execute files , operating system , Connect to database
The pony :
Houmeng Trojan horse with single function , Usually upload to keep asp Malaysia , Or a marginal note asp The pony
In a word, Trojans :
A very small page code backdoor , You can connect with the client , Control the site . Such as Chinese kitchen knife , The server is a back door .
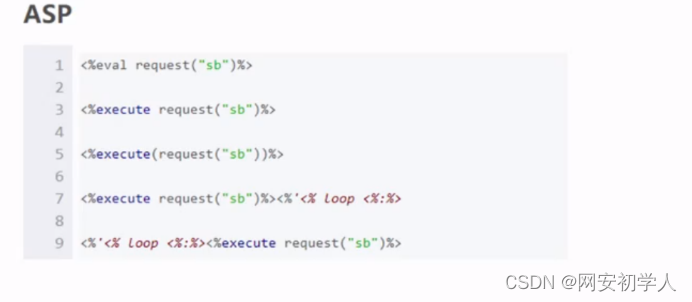
back door :
This is a figurative metaphor , After the attacker successfully controls the target host by using some methods , You can embed specific programs into each other's systems , Or change some settings , On the surface, these changes are hard to detect , But the attacker can use the corresponding program or method to easily establish a connection with this computer , Take control of this computer again , It's like the attacker got the key to your room , You can go in and out at any time without being found . Usually most Trojans (Trojan Horse) Programs can be used by attackers to create backdoors .
Destorehouse : Export data from the database
Social worker library :
It is a product of the combination of hackers and big data , Hackers integrate and analyze the leaked user data , And then centralized filing in one place .
Storehouse :
Hackers collect user names and passwords that have been leaked on the Internet , Generate corresponding dictionary table , After trying to bulk login to other websites , Get a list of users who can log in . Many users use the same account and password on different websites , Therefore, hackers can try to login by obtaining the user's account on the website B website , This can be interpreted as a collision attack .( Data will be washed out when there is an account )
Raise the right :
Improve your permissions in the server , Like in Windows You are logged in test Account , Become a super administrator by raising rights (root), With management windows All permissions of . Raising power is a professional term for hackers , It is generally used in website intrusion and system intrusion .
phishing :
Phshing, yes Fishing and Phone The combination of , Because the originator of hackers had committed crimes by telephone at first , So use Ph Instead of F Got the word , However , Today's phishing attacks use deceptive electronic right buttons and forged Web Site to carry out fraud activities , Victims often disclose their financial data , Such as credit card number 、 Account user name 、 Password and social security number .
Social engineering attacks ( abbreviation “ A social worker ”)
It is a psychological weakness through the attacker 、 Instinctive response 、 Curiosity 、 trust 、 Psychological traps such as greed, such as deception 、 Injury and other harmful means , The means of gaining self-interest . Hacker social engineering attack is to maximize the means of hacker intrusion attack , Not only can we exploit the weakness of the system to invade , It can also invade through the weakness of human nature , When hacker attacks are integrated with snake and engineering attacks , Generally, there is no so-called safe system
Rootkit
It's used by attackers to hide their tracks and keep them root( Administrator rights ) Access tools . Usually , An attacker can gain from a remote attack root Access right , Or you can first use password guessing to obtain general access to the system , After entering the system , Re pass , The security vulnerability of the other party's system memory obtains the root jurisdiction . then , The attacker will install rootkit, In order to achieve their own long-term control of each other's purpose ,rootkit It's similar to the Trojan horse and back door we mentioned earlier , But far more hidden than them , Hackers are typical rootkit, Yes, I did ntroorkit It's good to wait rootkit Tools .
IPC$
It's sharing “ Command pipeline ” Resources for , It is to allow inter process communication two open command pipelines , You can obtain the corresponding permissions by verifying the user name and password , Use when remotely managing computers and viewing shared resources on computers .
Weak password
Not strong enough , Easy to guess , Such as admin、123456 Such a password , common top100、top1000 Weak password
Default share :
The default share is WINDOWS2000/XP/2003 When the system starts the sharing service, it will automatically open the sharing of all hard disks , Because of the addition of ”$” Symbol , So you don't see a shared holding chart , Also become covert sharing .( View the default shared usage net share Command view )

Shell
Refers to a command-line environment , For example, we turn on windows Of cmd The command execution window is shell Execution environment , Usually, the environment for executing commands that we get after successfully overflowing the remote computer with the remote overflow program is the other party's shell.
Interaction shell( The form of accessing the back door is not interaction shell)
The interaction mode is shell Wait for you to enter the command , And execute the order you submit . This pattern is called interactive because shell Interact with users . This pattern is also familiar to most users ; Sign in , Execute some orders 、 Sign off . When you sign back ,shell It's over .
Webshell
Namely asp、php、jsp perhaps cgi I'll see a command execution environment in the form of web pages , It can also be called a web back door . After hackers attacked a website , Usually these prices asp perhaps php Backdoor file and web server WEB Normal web page files in the directory are mixed together , Then you can use the browser to access these asp perhaps php back door , Get a command execution environment , In order to control the website server . You can upload and download files , view the database , Carry out arbitrary orders .
overflow
“ out of buffer ”, That is, the program does not perform effective detection on the received input data, resulting in errors , The result could be a program crash or execution of an attacker's command . It can be roughly divided into two categories :· Heap overflow · Stack overflow
Inject :B/S( client ) Development of pattern application development , More and more programmers write programs in this mode , However, due to the uneven level of programmers, a large number of applications have security risks . Users can submit a database query code and return results according to the program , Get some data , This is it. SQLinjection,SQL Inject .
Injection point
Even where injection can be implemented , It's usually a connection to access a database , According to the permissions of the running account of the injection point database , The permissions obtained are also different .
边栏推荐
- Mapboxgl + GeoServer configuration local map tutorial
- 函数多种类型
- 项目免费部署到公网(内网穿透)
- Vulnhub-Funbox: Rookie(Funbox2)靶机渗透
- 再次聊聊浏览器缓存
- visibility:hidden 和 display:none
- haclabs: no_name(HL.ova)靶机渗透-Vulnhub
- 【百度地图API】您所使用的地图JS API版本过低,已不再维护,为保证地图基本功能 正常使用,请尽快升级到最新版地图JS API
- What is the function of key
- Vscode configuring autoprefixer
猜你喜欢
随机推荐
Substrate 技术及生态6月大事记 | Polkadot Decoded 圆满落幕,黑客松获胜项目为生态注入新生力量
MySQL之CRUD
4. Draw a red triangle and a yellow square on the screen. Triangle in the back, small; Square in front, big. Using the fusion technology, the triangle can be seen through the square, and the source an
Interpretation of the randomness of POS mechanism, how does poca's randomness principle work?
flex布局
稀缺性之于Web3:如何成为去中心化世界的胜利者
Promise续(尝试自己实现一个promise)更详细的注释和其它接口暂未完成,下次咱们继续。
Substrate 技术及生态5月大事记 | Square One 计划启动,波卡上线 XCM!
canvas - 旋转
利用流媒体将RSTP流转成WEB端播放(二)[可回看]
函数多种类型
Programmer tools collection! (Reprinted)
Unknown collation: ‘utf8mb4_0900_ai_ci‘的解决方法
16进制转rgb
OpenGL draws two points on the screen, a blue point on the right, using anti aliasing technology, and a red point on the left, without anti aliasing technology. Compare the difference between the two
visibility:hidden 和 display:none
PyCharm设置代码模板
网页播放rtsp视频流
Canvas - round
Canvas - rotate