当前位置:网站首页>Packaging and unpacking process of ESP message under IPSec transmission mode
Packaging and unpacking process of ESP message under IPSec transmission mode
2022-06-23 12:47:00 【Mengfei】
First map
Packaging process
- In the original IP In the message payload( It may be carrying TCP message ) Add later ESP trailer Information .
- ESP trailer Including three parts :Padding, Pad length, Next header. Since the selected encryption algorithm may be block encryption , So it may need to be filled (Padding); Fill length attached (Pad length) It is convenient to remove the filled data when unpacking ;Next Head Used to indicate the original IP The message payload The type of agreement , Such as 6 Express TCP.
- The original IP In the message payload And ESP trailer Proceed as a whole encryption , The encryption algorithm and key are provided by SA(Security Association) give .
- For the first time 2 Add the encrypted data obtained in step ESP header, Encrypted data and ESP header Collectively known as “Enchilada”, Yes “Enchilada” Make one Abstract , Get an integrity measure (ESP Message Authentication Data), And add to the end , Integrity measurement algorithms include the following The authentication key to be used is provided by SA give .
- ESP header It consists of two parts :SPI (Security Parameter Index),Sequence number. SPI Used with SA Association , from SAD Get information about the IPSec Packet protocol algorithm, key and other information ;Sequence number It is initially established as 0, Each packet sent will increase automatically 1, Used to resist retransmission attacks .
- Put the original IP The head of the protocol Change the field to 50( Indicates that the upper layer agreement is ESP), And add to ESP header front , Complete packaging .
Unpacking process
- The receiver receives IP After the message , The protocol type found is 50, That means this is one ESP package . First see ESP header, adopt SPI Determine the corresponding... Of the data message SA , Get the corresponding pattern (tunnel/transport mode) And safety regulations .
- Calculation “enchilada” A summary of the section , And attached at the end Authentication Data comparing , Verify data integrity ; Check the sequence number , Make sure the data is “ fresh ” Of , Prevent replay attacks .
- according to SA Encryption algorithm and key provided , Decrypt Encrypted data , Get the original IP The message payload And ESP trailer.
- according to ESP trailer Of Next Header Judge ESP The type of message protocol encapsulated ( Such as TCP), And according to Padding Length Fill in length information , Find the length of the filled field , Delete and get the original IP The message payload.
- take IP Tou and Yuan IP The message payload Combine , Then we get the complete original IP message .
Classic illustration
notes :payload( Load data ) Is relative , about IP Protocol message ,payload yes TCP header + TCP payload, So pay attention to distinguish between the above words and pictures payload describe .
边栏推荐
- 生态 | 万里数据库与卫士通完成兼容认证 共筑网络安全生态体系
- Localization information | aikesheng and China kefangde complete product compatibility and mutual certification
- Playing in Singapore in the hot summer: an inventory of indoor attractions and good places for night trips
- QT knowledge: QT widgets widget function [02]
- 群晖万兆网络配置与测试
- How to uninstall and reinstall gazebo
- 这两所985大学,共享同一位校长!校方:属实
- 唐人街徒步:在异国情调的纽约感受浓厚的中式气息
- mysql中innodb下的redo log什么时候开始执行check point落盘的?
- 判断测试结束的标准有哪些?
猜你喜欢

Halcon principle: correlation matching

Ecological Wanli database and Westone completed compatible certification to jointly build a network security ecosystem

Wallys/DR6018-S/ 802.11AX MU-MIMO OFDMA / 2* GE PORTS/WIFI 6e / BAND DUAL CONCURRENT

生态 | 万里数据库与卫士通完成兼容认证 共筑网络安全生态体系

Design of routing service for multi Activity Architecture Design

New project, how to ensure the coverage of the test?

QT5知识:字符串列表QStringListModel

Stimulsoft Ultimate Reports 2022.3.1

跟循泰国国内游宣传曲MV,像本地人一样游曼谷
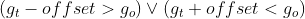
Halcon knowledge: dyn_ Usage of threshold (scratch detection)
随机推荐
M & A and capital increase may be expected to start Neusoft's new momentum?
手机开户有什么风险吗?开户安全吗?
Qt5 knowledge: DNS query
mysql中innodb下的redo log什么时候开始执行check point落盘的?
Oracle数据库的主导地位被云竞争对手逐渐侵蚀
首次曝光!唯一全域最高等级背后的阿里云云原生安全全景图
【UVM入门 ===> Episode_7 】~ sequence、sequence item、sequencer、driver
测试人员跳槽到新公司,工作怎样快速上手?
【基础知识】~ 数据位宽转换器
[no title] 2022 pressure pipeline patrol inspection and maintenance test questions and online simulation test
「开发者说」钉钉连接器+OA审批实现学校学生假勤场景数字化
Photon网络框架
20年上海站D题Walker(二分,简洁)
2022 construction worker - Equipment direction - post skill (construction worker) test question simulation test platform operation
面试题:举例说一下工作中你的接口测试是怎么做的?
Huawei cloud gaussdb heavily released HTAP for commercial use, defining a new paradigm of cloud native database 2.0
The project experience of resume and several problems that testers should pay attention to in writing
If there is a problem with minority browsers, do you need to do a compatibility test?
"Developer talk" nail connector +oa approval to realize digitalization of school students' leave and work scenes
安装Rstudio Desktop和Rstudio Server免费版本