当前位置:网站首页>When kubernetes encounters confidential computing, see how Alibaba protects the data in the container! (Internet disk link attached)
When kubernetes encounters confidential computing, see how Alibaba protects the data in the container! (Internet disk link attached)
2020-11-08 11:01:00 【Programmer interview】
Today I share with you the internal information of Alibaba , When Kubernetes Encounter secret Computing , How does Ali protect the data in the container ! Pull down at the end of the text to get the link to the network disk
- Introduction to confidential Computing
1.1 Application container security status 
1.2 The age of secret computing is coming 
1.3 Computing confidential business scenarios 
1.4 The difference between secure containers and secret Computing 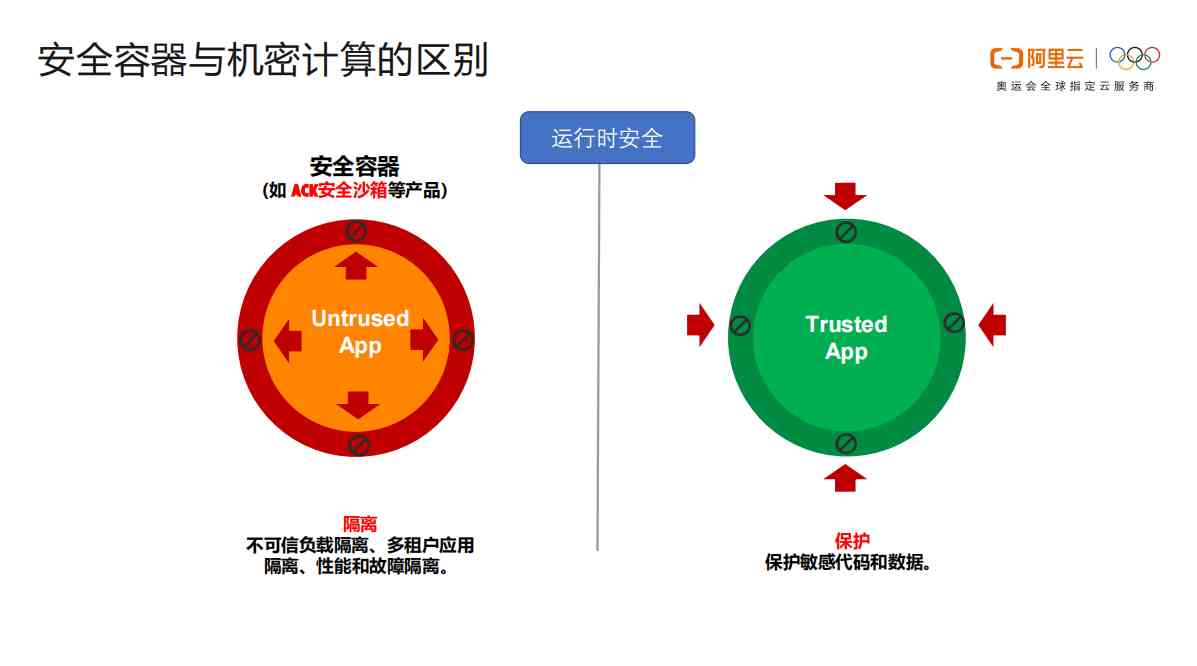
1.5 TEE Hardware platform 
1.6 Intel SGX There are smaller ones TCB(Trusted Computing Base) 
1.7 be based on Intel SGX Trusted application development and use process of 
- InclavareContainers Protect sensitive applications and data
2.1 Inclavare Containers The goal and value of 
2.2 Inclavare Containers framework 
2.3 shim-rune Workflow 
2.4 Client side signature and server side signature 
2.5 Multi team cooperation 
2.6 Inclavare Containers Open source project 
2.7 Inclavare Containers Milepost 
2.8 2020 Secret computing technology industry 
- ACK-TEE
3.1 ACK-TEE brief introduction 
3.2 ACK-TEE 1.0 
3.3 ACK-TEE 2.0 
Click on the link to get the full document link :https://pan.baidu.com/s/112GDueQO4SRsXM7VpnDckQ Extraction code :ejaq
※ Part of the article comes from the Internet , If there is infringement, please contact to delete ; More articles and materials | Click on the text directly after ↓↓↓ 100GPython Self study Kit Alibaba cloud K8s Actual combat manual [ Alibaba cloud CDN Pit guide ]CDN ECS Operation and maintenance guide DevOps Practice Manual Hadoop Big data combat manual Knative Cloud native application development guide OSS Operation and maintenance manual White paper on cloud native architecture Zabbix Enterprise level distributed monitoring system source document 10G The interview questions of large factories are marked with
版权声明
本文为[Programmer interview]所创,转载请带上原文链接,感谢
边栏推荐
- How to deploy pytorch lightning model to production
- Automatically generate RSS feeds for docsify
- Analysis of istio access control
- C语言I博客作业03
- Top 5 Chinese cloud manufacturers in 2018: Alibaba cloud, Tencent cloud, AWS, telecom, Unicom
- 盘点那些你没想到的云计算应用场景(上)
- 虚拟机中安装 macOS 11 big sur
- PCIe 枚举过程
- 笔试面试题目:盛水最多的容器
- python_ scrapy_ Fang Tianxia
猜你喜欢

2天,利用下班后的4小时开发一个测试工具

How does spotify drive data-driven decision making?

第二次作业

Spotify是如何推动数据驱动决策的?

vivoY73s和vivoY70s的区别 vivoY73s和vivoY70s哪个值得入手

Review the cloud computing application scenarios you didn't expect (Part 1)

Introduction to mongodb foundation of distributed document storage database

虚拟机中安装 macOS 11 big sur

Mate 40 series launch with Huawei sports health service to bring healthy digital life

Installing MacOS 11 Big Sur in virtual machine
随机推荐
Installing MacOS 11 Big Sur in virtual machine
Hematemesis! Alibaba Android Development Manual! (Internet disk link attached)
Dogs can also operate drones! You're right, but it's actually an autonomous drone - you know
It's worth seeing! EMR elastic low cost offline big data analysis best practice (with network disk link)
Ali! Visual computing developer's series of manuals (with internet disk link)
Top 5 Chinese cloud manufacturers in 2018: Alibaba cloud, Tencent cloud, AWS, telecom, Unicom
软件测试就是这么回事?!
Mate 40系列发布 搭载华为运动健康服务带来健康数字生活
吐血整理!阿里巴巴 Android 开发手册!(附网盘链接)
Top 5 Chinese cloud manufacturers in 2018: Alibaba cloud, Tencent cloud, AWS, telecom, Unicom
What is the difference between vivoy73s and vivoy70s
Shiyou's numerical analysis assignment
vivoY73s和vivoY70s的区别 vivoY73s和vivoY70s哪个值得入手
软件测试培训班出来好找工作么
仅用六种字符来完成Hello World,你能做到吗?
TiDB 性能竞赛 11.02-11.06
学习小结(关于深度学习、视觉和学习体会)
还不快看!对于阿里云云原生数据湖体系全解读!(附网盘链接)
Test requirements for MIC certification of Bluetooth 2.4G products in Japan
Japan PSE certification