当前位置:网站首页>Hackingtool of security tools
Hackingtool of security tools
2022-07-24 07:07:00 【Xijing swordsman】
List of articles
- Safety tools hackingtool
- Security Tools menu
- Anonymous surfing
- information gathering
- Password attacks
- Wireless attack
- SQL Injection tool
- Social media attacks
- Android attack
- Phishing attacks
- Network attack
- After exploration
- Forensic Tools
- Payload generator
- Using the framework
- Social media finder
- steganography
- DDoS Attack tools
- XSS Attack tools
- IDN Homomorphic variant characters
- Email Verifier
- Hash cracking tool
- stay Linux Install in
- Kali Linux and Parrot OS
Safety tools hackingtool
github: https://github.com/Z4nzu/hackingtool
All in One Hacking tool For Hackers
All tools for hackers
Security Tools menu
- Anonymous surfing
- information gathering
- Password attacks
- Wireless attack
- SQL Injection tool
- Phishing attacks
- Cyber attack tools
- Later use
- Forensic Tools
- Payload creator
- Router uses
- Wifi interfere
- XSS Attack tools
- Social media finder
- DDos Attack tools
- Steganography tools
- IDN Homograph attack
- Hash cracking tool
- Social media attacks
- Android hackers
- Update system
Anonymous surfing
Anonymous surfing
Multi rotor
information gathering
Map
mapping
Port scanning
Host to IP
Xerosploit
There's information - E-mail OSINT
Reconnaissance spiders
RED HAWK( All in one scanning )
Scout dog
striker
The seeker
Port scanner
vandals
Password attacks
Kup
Thesaurus creator
Goblin word generator
Credential reuse attack
Wordlist( contain 14 Billion passes )
Wireless attack
WiFi- pumpkin
Elf
Bluetooth honeypot GUI frame
flux
Phishers
Wireless network
Evil twins
SQL Injection tool
sqlmap Tools
NoSqlMap
Damn small SQLi Scanner
Development
Blisqy - Use time-based blindness SQL Inject
Leviathan - Extensive large-scale audit toolkit
SQLScan
Social media attacks
Instagram attack
AllinOne Social media attacks
Facebook attacks
Application checker
Android attack
Keyboard robot
My message
Lockphish( Grab the target LOCK PIN)
DroidCam( Capture images )
EvilApp( Hijack session )
Phishing attacks
tool kit
Social fish
Occult eye
Evilginx2
shellfish
Black eyes
I-See-You( Use phishing attacks to get location )
SayCheese( Capture the webcam photos of the target )
QR code jacking
Network attack
Lazy monkey
Bonito
Subdomain finder
Check the website
burning hot
Subdomains take over
After exploration
Vegile - Ghost in the shell
Chrome Keyboard recorder
Forensic Tools
Batch extractor
Disk cloning and ISO Image acquisition
Automatic spy
Tosley
Line shark
Payload generator
Fat rat *
savage
seam
MSFvenom Payload creator
venom Shellcode generator
Spy camera
Mob robot
Using the framework
Router Sploit
WebSploit
comic
Web2 attack
Fast SSH
Social media finder
Find social media through facial recognition systems
Find social media by user name
Shylock
Social scanning
steganography
SteganoHide
StegnoCracker
blank
DDoS Attack tools
Lazy monkey
SYN The flood DDoS weapons
UFO net
Golden eye
XSS Attack tools
DalFox(XSS Finder )
XSS Load generator
senior XSS Test kit
Extended XSS Searchers and finders
XSS freak
X Spear
XSSCon
XanXSS
IDN Homomorphic variant characters
Evil website
Email Verifier
Knock mail
Hash cracking tool
Hash nemesis
stay Linux Install in
This tool must be in ROOT body Copy run
git clone https://github.com/Z4nzu/hackingtool.git
chmod -R 755 hackingtool
cd hackingtool
sudo pip3 install -r requirement.txt
./install.sh
sudo hackingtool
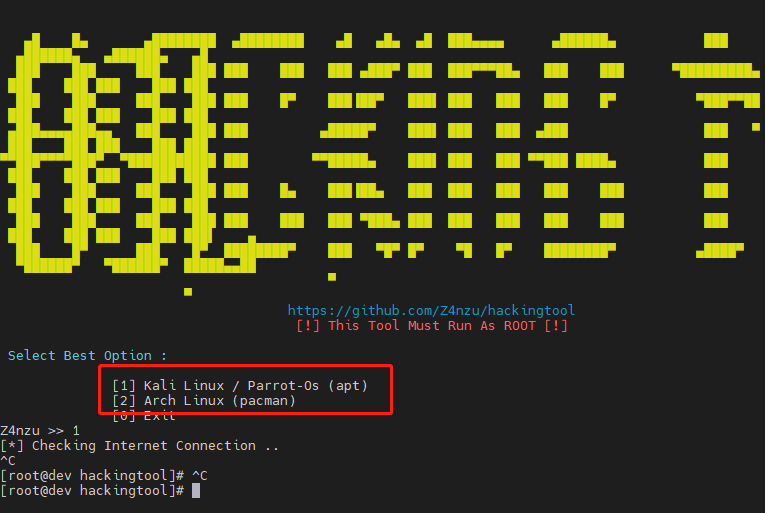 Above , perform ./install.sh install , Will let you choose the operating system .
Above , perform ./install.sh install , Will let you choose the operating system .
Pacman It's a package manager , As ArchLinux Part of the distribution . Simply speaking , That's right. apt-get To Ubuntu equally ,pacman Namely Arch Of apt-get.
- Whether it's Kali Linux Good , still Parrot OS Let it be , Are very suitable for penetration testing 、 Network security 、 And safety audit Linux operating system .
After all the steps , Simply enter :
[email protected]:~ hackingtool
Kali Linux and Parrot OS
Kali Linux and Parrot OS, Which is more suitable for safety ?
Reference resources URL: https://baijiahao.baidu.com/s?id=1707764336639803556
Whether hackers 、 Loophole Bounty Hunter 、 Penetration tester 、 Or security researchers , Can tell you what is suitable for their daily work and operation Linux Distribution version . among , The most famous is Kali Linux and Parrot OS. They are currently in the daily testing and penetration attack activities of moral hackers and penetration testers , Favorite operating system .
边栏推荐
- It can be written in 10 minutes -- 25~30k foreign enterprise recruitment interview questions, isn't it easy~
- [C language] operator details (in-depth understanding + sorting and classification)
- 渗透学习-SQL注入篇-靶场篇-安全狗的安装与绕过实验(后续还会更新)
- Three level classification / menu query tree structure
- Nodejs enables multi process and inter process communication
- 【学习笔记】网页出现白屏可能的原因与优化方法
- Prompt for garbled code when CHM file is opened
- 三级分类/菜单的查询——树形结构
- [learning notes] Web page rendering process
- 第二部分—C语言提高篇_4. 二级指针
猜你喜欢

STM32 ADC based on Hal library uses DMA multi-channel sampling and solves the problems encountered

Redis sentinel mechanism

Redis 主从机制

Penetration learning - SQL injection - shooting range - installation and bypass experiment of safety dog (it will be updated later)

Redis master-slave mechanism

C语言中extern,static, register,volatile 关键字的作用;保姆级教学!

Metaltc5.0 realizes webrtc version IPC of Junzheng pure C

17. 什么情况用ArrayList or LinkedList呢?

聚合型新生态模式-分享购,会员及奖励制度

GE口:SGMII模式和serdes模式
随机推荐
聚合型新生态模式-分享购,会员及奖励制度
owasp top10 渗透测试
【方向盘】IDEA的代码审查能力,来保证代码质量
metaRTC5.0实现君正的纯C的webrtc版IPC
Design a function print to print the string. If only the string parameter s is passed, the string length is compared with 10, greater than 10, print the first 10 characters, less than 10, and output a
Penetration learning - SQL injection - shooting range - installation and bypass experiment of safety dog (it will be updated later)
在线问题反馈模块实战(十二):实现图片删除功能
17. 什么情况用ArrayList or LinkedList呢?
Geek planet ByteDance one stop data governance solution and platform architecture
Redis 分片集群
[learning notes] possible reasons and optimization methods for white screen on Web pages
Thinking of data analysis -- analyzing the retail industry as a whole -- an all-round and multifaceted detailed analysis
lambda表达式对list对象进行多字段排序
Ue4/5 cannot open the file "xxx.generated.h" (cannot open file xxx.generated.h) solution summary
你就是你,没有人可以取代
Redis persistence
Jsonobject is sorted in A-Z order of key
上传图片base64
Mac can't connect to local MySQL server through socket '/tmp/mysql Sock '(2) problem
【方向盘】超爱的IDEA提效神器Save Actions,卸载了