当前位置:网站首页>Front and back management system of dessert beverage store based on SSM framework dessert mall cake store [source code + database]
Front and back management system of dessert beverage store based on SSM framework dessert mall cake store [source code + database]
2022-06-22 14:33:00 【Flying page】
One 、 Project brief introduction
This project is based on SSM The front and back management system of the dessert beverage store realized by the framework is the dessert mall cake store , It is mainly aimed at the students who are completing the design of computer related majors and those who need project practice Java Learners' .
contain : Project source code 、 Database script, etc , The project with all the source code can be used as a complete set .
The project has been strictly debugged ,eclipse and idea Ensure that it can run !
The system has perfect functions 、 Beautiful interface 、 It's easy to operate 、 The function is all ready 、 Easy to manage , It has high practical application value
Two 、 Technical realization
ssm frame , namely :spring,springmvc,mybatis,mysql
The front end uses :jsp,jquery,css
Operating environment and development tools :jdk8,idea perhaps eclipse,maven,Navicat
3、 ... and 、 system function
1、 The front desk functions mainly include :
User login and registration functions
Home page display List of best selling recommended desserts , New product recommendation list
Commodity classification management : Including the classic collection , French series , Children series , Snack series , Ice cream series
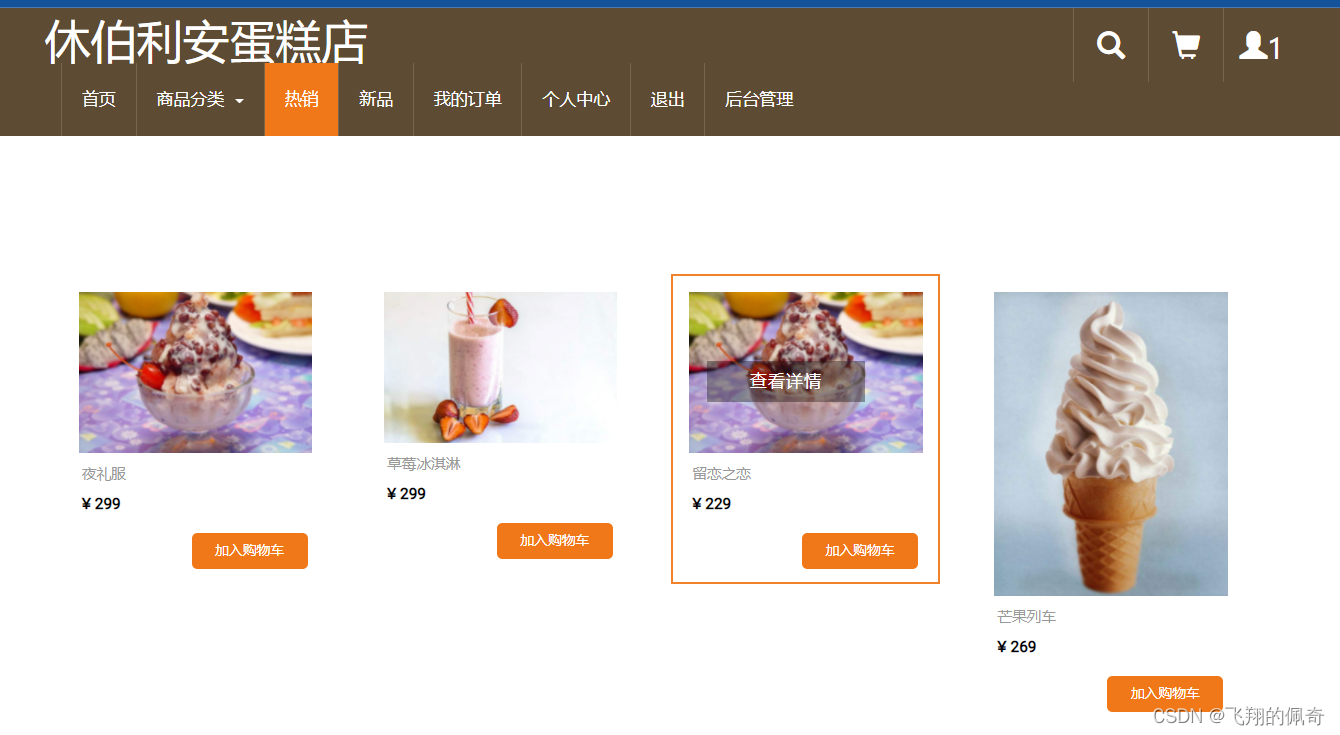
Hot selling module : Show a list of all the best selling items , And each dessert can be clicked to see the details , You can also add it directly to the shopping cart
New product module : Show a list of all new product recommendations , And each dessert can be clicked to see the details , You can also add it directly to the shopping cart
My order module : Show the dessert information that has been ordered
Personal center module : Include the name of the consignee 、 Telephone 、 Address , And login user name and password , And it can be modified
My shopping cart module : View the product information added to the shopping cart , And can increase , Reduce , Delete item , And the total amount will be automatically reduced
Exit function
2、 Background functions mainly include :
Order management : Include a list of all order information , List of unpaid order information , List of paid order information , Order information list in distribution , Completed order information list
Customer management module 、 Commodity management module 、 Category management module 、 Change password module 、 Exit function
Four 、 Screenshot of the page





5、 ... and 、 Database screenshot

6、 ... and 、 Source code address
边栏推荐
- How many days are there between the two timestamps of PHP
- 天润云上市在即:VC大佬田溯宁大幅减持,预计将套现2.6亿港元
- 基于SSM框架实现的甜品饮品店前后台管理系统甜品商城蛋糕店【源码+数据库】
- Transformers vit image model vector acquisition
- C#泛型_泛型类
- What is the difference between Z-score and deltf/f?
- How to use SQL to modify in the database & delete
- uniapp app 端截屏且保存到本地
- unity防止按钮btn被连续点击
- Z-Score和deltf/f有什么区别?
猜你喜欢

VR panoramic shooting breaks the deadlock of traditional propaganda that wild geese pass without leaving traces

程序员要不要选择软件人才外包公司?

Understand the quality assurance of open source software (OSS)
Implementation of redis+caffeine two-level cache

JS advanced programming version 4: learning iterators

Installing and using protobuf-c

Flink状态管理

一文彻底弄懂建造者模式(Builder)

融云:让银行轻松上“云”

3dMax建模笔记(一):介绍3dMax和创建第一个模型Hello world
随机推荐
机器学习之随机森林
Cve - 2022 - 22965 Resume
Chengdu test equipment development_ Array introduction of C language for single chip microcomputer
Aliyundrive fuse that allows jellyfin to directly mount alicloud disks
What you must understand before you are 30
BSN发展联盟理事长单志广:DDC可为中国元宇宙产业发展提供底层支撑
Verification code is the natural enemy of automation? See how the great God solved it
数据库中如何使用SQL进行修改&删除
History of hash index design
Excuse me, is Zhongyan futures reliable? Is the fund safe?
哈希索引设计发展史
How to protect WordPress websites from cyber attacks? It is important to take safety measures
Cat agile team coaching workshops - August 20
How location coding (PE) works in transformers
After reading this article, I will teach you to play with the penetration test target vulnhub - drivetingblues-5
Double hands of daily practice of Li Kou 2day9
C generic_ Generic class
Flink状态管理
Kukai TV ADB
Go Web 编程入门:验证器
