当前位置:网站首页>XSS white list
XSS white list
2022-07-24 13:42:00 【Amitabha @ Moda】
const xss = require('xss')
export default function (string) {
// xss White list
const whiteList = Object.assign(xss.whiteList, {
marquee: [],
label: [],
fieldset: [],
legend: [],
blockquote:[]
})
const options = {
whiteList
}
return xss(string, options)
}
边栏推荐
- 户外广告牌不能“想挂就挂”!广州城管部门加强户外广告安全管理
- 网络安全——服务漏洞扫描与利用
- Odoo+ test
- 【无标题】rhcsa第一次作业
- How to generate expected data? Emory University and others' latest "deep learning controllable data generation" review, 52 page PDF, covering 346 documents, comprehensively expounds the controllable g
- Simulate the implementation of the library function memcpy-- copy memory blocks. Understand memory overlap and accurate replication in detail
- Network security - file upload competitive conditions bypass
- 爱可可AI前沿推介(7.24)
- Network security - use exchange SSRF vulnerabilities in combination with NTLM trunking for penetration testing
- Analysis of device restart jamming -reboot jamming
猜你喜欢

Pointer advanced part (1)

网络安全——文件上传黑名单绕过
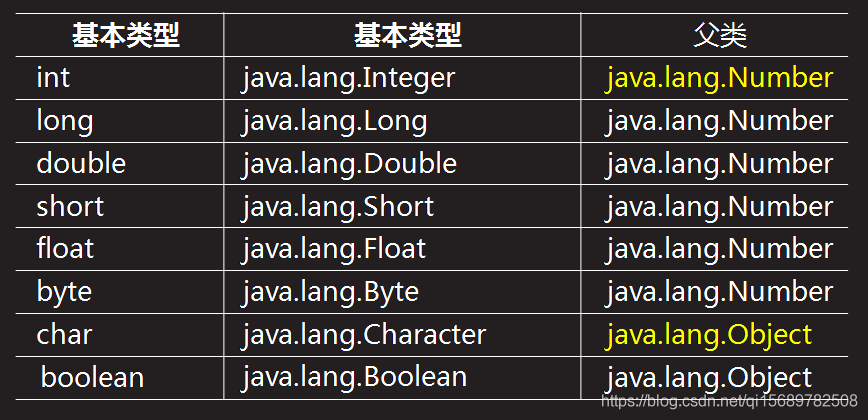
Packaging class (mutual conversion between types)

Network security - file upload whitelist bypass

Representation and basic application of regular expressions

Explain the edge cloud in simple terms | 2. architecture

Aike AI frontier promotion (7.24)
网络安全——过滤绕过注入

【无标题】

开放环境下的群智决策:概念、挑战及引领性技术
随机推荐
Wildcard (Pan domain name) SSL certificate
Statistical table of competition time and host school information of 2022 national vocational college skills competition (the second batch)
Atcoder beginer contest 261 f / / tree array
rhcsa第六次笔记
Aike AI frontier promotion (7.24)
Network security - Web penetration testing
使用Activiti创建数据库表报错,
R语言使用epiDisplay包的summ函数计算dataframe中指定变量在不同分组变量下的描述性统计汇总信息并可视化有序点图、自定义cex.main参数配置标题文本字体的大小
Data formatting widget
为什么函数式接口 Comparator 中有 “两个抽象方法”?
Notes on Linear Algebra -- lesson 25 -- projection of vectors on axes
如何用WebGPU流畅渲染百万级2D物体?
Adjust the array order so that odd numbers precede even numbers
支持鹏程系列开源大模型应用生态演化的可持续学习能力探索
网络安全——文件上传黑名单绕过
Network security - use exchange SSRF vulnerabilities in combination with NTLM trunking for penetration testing
Network security - file upload blacklist bypass
【无标题】rhcsa第一次作业
网络安全——报错注入
Browser type judgment