当前位置:网站首页>Penetration testing - logic vulnerability topic
Penetration testing - logic vulnerability topic
2022-06-22 02:28:00 【amingMM】
Special topic on logical vulnerabilities
1.3 Password recovery vulnerability ~1





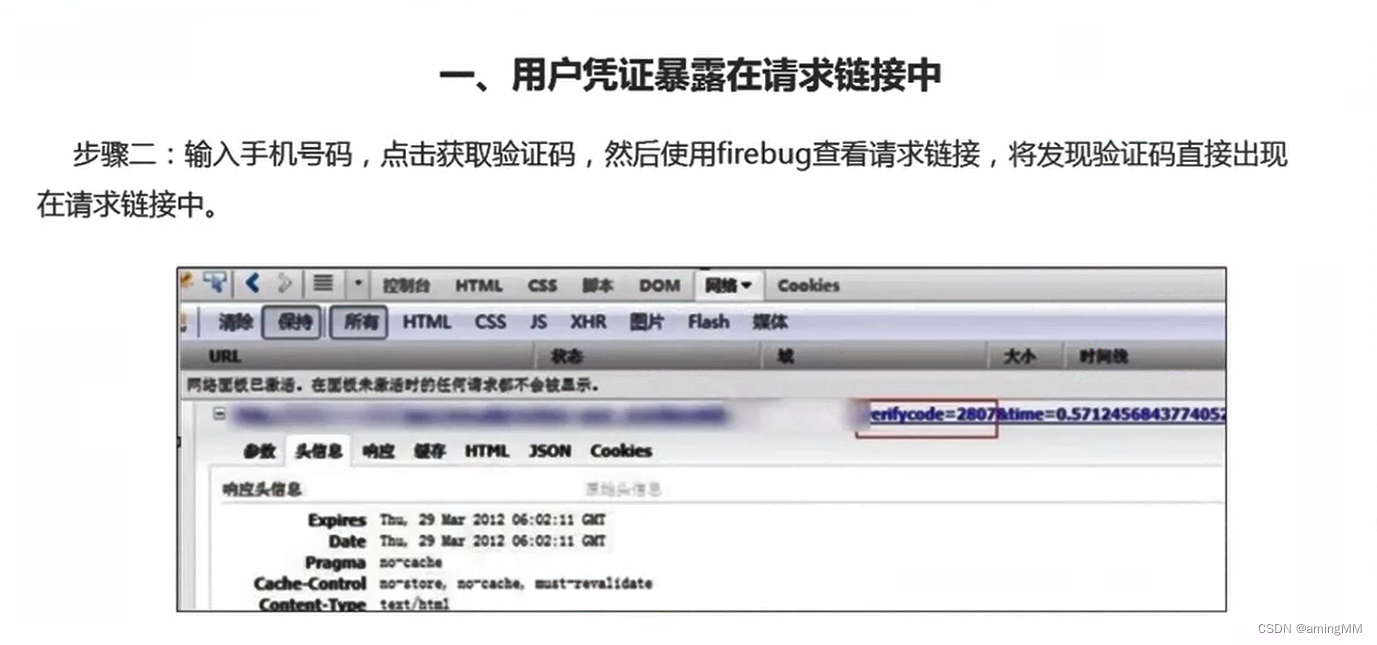
























1、 Password reset
The general design of password reset is divided into the following four steps :
1. Enter account name



2. Verify identity


3. Reset password



4. complete
Usually vulnerabilities exist in 2 perhaps 3 In the step , Let's take a look at some common ways to reset password vulnerabilities .
2、 Use at will
3、 Unauthorized operation
The idea of digging logical loopholes
1、 Various echo ( Verification code echo , Echo user credentials , Personal information echo )
2、 Various reversible ( There is a danger of collision at the landing site , User credentials found )
3、 Logical order ()

Ultra vires
















Payment logic loopholes





























Unauthorized access holes -Over permission Management account ultra vires
Unauthorized access holes
Over permission If you use A User's authority to operate B User's data ,A Is less than B Authority , If it works successfully , It is called ultra vires operation .
The reason for ultra vires loopholes is that the background uses Unreasonable permission verification rules lead to . General ultra vires vulnerability is easy to appear in the permission page ( The page you need to log in to ) increase 、 Delete 、 Change 、 Where I checked ,
When the user performs these operations on the information in the permission page , The background needs to Verify the permissions of the current user , See if it has the right to operate ,
And then give the response , However, if the rules of verification are too simple, it is prone to ultra vires loopholes . therefore , In authority management, you should follow :
1. Use the principle of minimum permission to empower users ;2. Reasonable use ( Strictly ) Permission verification rules ;3. Use the background login status as a condition for permission judgment , Don't blindly use the conditions transmitted from the front end ;














Ultra vires loophole
1.1 Privilege bypass vulnerability Next ~1
Vertical ultra vires









Log out after replay This packet

To generate the form 




Delete user packet replay after logging out


Modify the operating







Not logged in Just change the password
边栏推荐
- Wechat applet film and television comment exchange platform system graduation design (2) applet function
- PMP备考相关敏捷知识
- Array common methods
- 并查集dsu
- In 2022, the number of mobile banking users in Q1 will reach 650million, and ESG personal financial product innovation will be strengthened
- 华阳智能冲刺深交所:拟募资4亿 复星惟盈是股东
- Chapter 24 image and video processing based on Simulink -- matlab in-depth learning and practical collation
- Wechat applet film and television comment exchange platform system graduation design (3) background function
- 带你区分几种并行
- atguigu----列表渲染
猜你喜欢

EMC整改小技巧

idea----bookmark

优秀的 Verilog/FPGA开源项目介绍(二十七)- 小型CPU

word文档转markdown文档?

Minecraft 1.18.2 biochemical 8 module version 1.3 3D objects + more complex villages

PMP备考相关敏捷知识

剑指offer 26:树的子结构

微信小程序影视评论交流平台系统毕业设计毕设(6)开题答辩PPT

微信小程序影视评论交流平台系统毕业设计毕设(4)开题报告

DAST black box vulnerability scanner part 4: scanning performance
随机推荐
The "cloud" end of the 6th world intelligence conference will be held soon
论文笔记: 多标签学习 ACkEL
Atguigu---- filter
关于PMP考试,你想知道的知识都在这里了
In the era of industrial Internet, there is no real center
Chapter 19 signal lamp image simulation control technology based on speech recognition
Automated tools - monitoring file changes
Chapter 25 digital watermarking technology based on Wavelet Transform
Input system learning ----- inputfilter
Get to know unity3d (project structure, third-party plug-in of probuilder)
EMC Radiation Emission rectification - principle Case Analysis
EMC radiation emission rectification - principle case analysis
FPGA-Xilinx 7系列FPGA DDR3硬件设计规则
[Chapter 20 video target detection based on inter frame difference method -- Application of MATLAB software in-depth learning]
剑指offer 26:树的子结构
Introduction to Apache ActiveMQ Artemis
微信小程序影视评论交流平台系统毕业设计毕设(7)中期检查报告
Rely on the robustness of trusted AI to effectively identify deep forgery and help banks fight identity fraud
Paper notes: multi label learning ackel
zap语法糖