当前位置:网站首页>Installation and configuration of grayog new generation log collection early warning system
Installation and configuration of grayog new generation log collection early warning system
2022-06-27 20:24:00 【51CTO】
In the company, I have been responsible for the construction of the monitoring system of the whole company , It mainly includes the hardware monitoring of the underlying server 、 System level monitoring 、 Monitoring of network equipment 、 Middleware and application level monitoring, etc . although Zabbix Support log monitoring , Because in the data volume 、 Search and log display are relatively weak , Only simple log alarms can be made . Therefore, log monitoring still needs to be done through professional tools . I compared it ELK、 Business log tool Splunk and Graylog, Later, I chose Graylog.Graylog Simply put, it is an open source log aggregation 、 analysis 、 Audit 、 Presentation and early warning tools . comparison ELK,Graylog A lightweight ,UI The interface is more beautiful , There are abundant and perfect API Interface . Currently, the logs of network devices are collected 、MySQL Error log 、Linux System logs, etc , We will consider accessing the microservice log later . Various logs are statistically analyzed according to the error level , By looking at Dashboards The report can confirm whether there are problems with thousands of online devices . The corresponding high-level logs pass Graylog +Python The program realizes the alarm function of wechat and e-mail .
One 、Graylog advantage
Zero development : Collect from -> Storage -> analysis -> Present the complete process .
Deployment and maintenance are simple : Integrated solutions , Unlike ELK Integration of three independent systems .
Multi day Zhiyuan access :syslog、Filebeat、Log4j、Logstash etc. .
Multi protocol access :UDP、TCP、HTTP、AMQP.
Custom panel : Provide curves 、 The pie chart 、 A rich list of graphics such as world maps .
Full text search : Support filtering and searching all logs by syntax .
Support alarm : Log analysis platform with alarm function , Currently only email is supported , Can pass API Realize wechat alarm .
Rights management : Flexible authority allocation and management .
Support clusters : The platform performance can be extended according to the application .
Two 、Graylog Architecture design , Support clusters
GrayLog: Provide GrayLog External interface , Belong to CPU Concentrated .
Elasticsearch: Persistent storage and retrieval of log files , Belong to IO Concentrated .
MongoDB: Store some GrayLog Configuration information .

3、 ... and 、 Installation configuration
3.1 adopt Docker install mongodb database .
3.2 adopt docker compose Mode of installation ES.
3.3 install Graylog service .
establish graylog Profile directory .
install graylog service .
Copy and edit graylog Configuration files and startup files .
start-up graylog service .
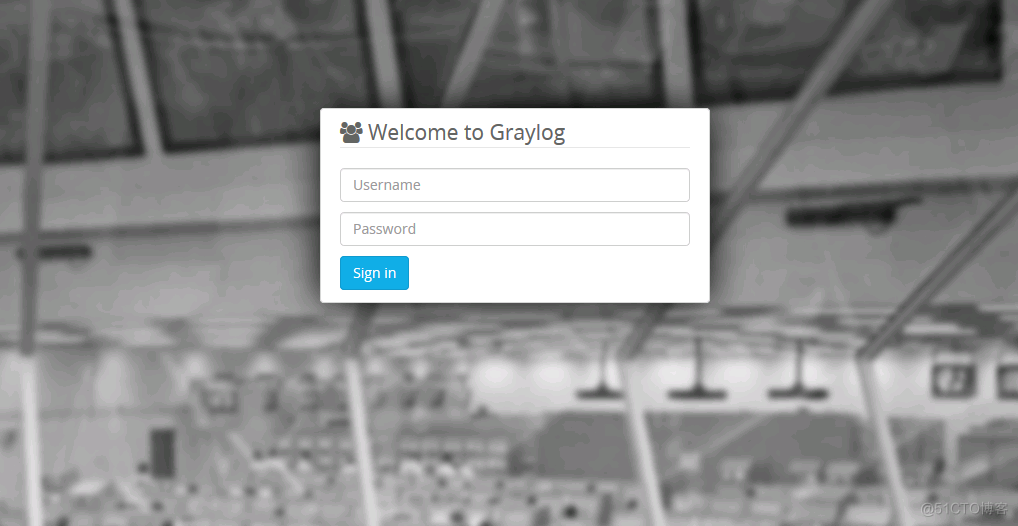
3.4 verification graylog Whether the service installation configuration is normal . adopt http://yourip:9000 To visit .
Four 、 summary
1)root_password_sha2 The password can be echo -n yourpassword | sha256sum To generate , there yourpassword Is used to log in graylog Of admin User's password . Generated root_password_sha2 Please delete the blank space and -, Otherwise, the login will not succeed .
2) edit graylog Startup file , Appoint graylog The path to the configuration file .
边栏推荐
- BAIC makes a brand new pickup truck, which is safe and comfortable
- Csdn Skills Tree use Experience and Product Analysis (1)
- Mobile low code development theme month | visual development one click generation of professional source code
- Mass lucky hash game system development - conflict resolution (code analysis)
- UE4 realizes long press function
- Redis持久化
- #yyds干货盘点#SQL 子查询
- Common shell script commands (III)
- Array exercises follow up
- 安全才是硬道理,沃尔沃XC40 RECHARGE
猜你喜欢
随机推荐
Bit.Store:熊市漫漫,稳定Staking产品或成主旋律
Web APLS phase - Section 14 - local storage
BLE蓝牙模块NRF518/NRF281/NRF528/NRF284芯片方案对比
从指令交读掌握函数调用堆栈详细过程
可观测,才可靠:云上自动化运维CloudOps系列沙龙 第一弹
【bug】上传图片出现错误(413 Request Entity Too Large)
Safety is the last word, Volvo xc40 recharge
Leetcode 989. 数组形式的整数加法(简单)
Grasp the detailed procedure of function call stack from instruction reading
Summary of submarine cable detection technology
Rust advanced ownership - memory management
Binary tree related problems 2
数据库索引
刷题笔记-树(Easy)-更新中
BAIC makes a brand new pickup truck, which is safe and comfortable
MASS幸运哈希游戏系统开发丨冲突解决方法(代码分析)
Hash table - Review
在开发数字藏品时,文博机构该如何把握公益和商业的尺度?如何确保文物数据的安全?
Common shell script commands (4)
At 19:00 on Tuesday evening, the 8th live broadcast of battle code Pioneer - how to participate in openharmony's open source contribution in multiple directions