当前位置:网站首页>Gather relevant knowledge points and expand supplements
Gather relevant knowledge points and expand supplements
2022-07-24 21:28:00 【Wang Xiaoya】
Collection aggregate
List aggregate
ArrayList It's a dynamic array , The bottom layer is an implementation Object Array . When using a parameterless constructor ArrayList() when , Initial capacity elementData by 0. Capacity during the first expansion +10. When the capacity needs to be expanded again , Expanded to the original capacity 1.5 times . When using a parameterized constructor , The initial capacity is the capacity of the parameter passed in . When expansion is needed , Expanded to the original capacity 1.5 times .
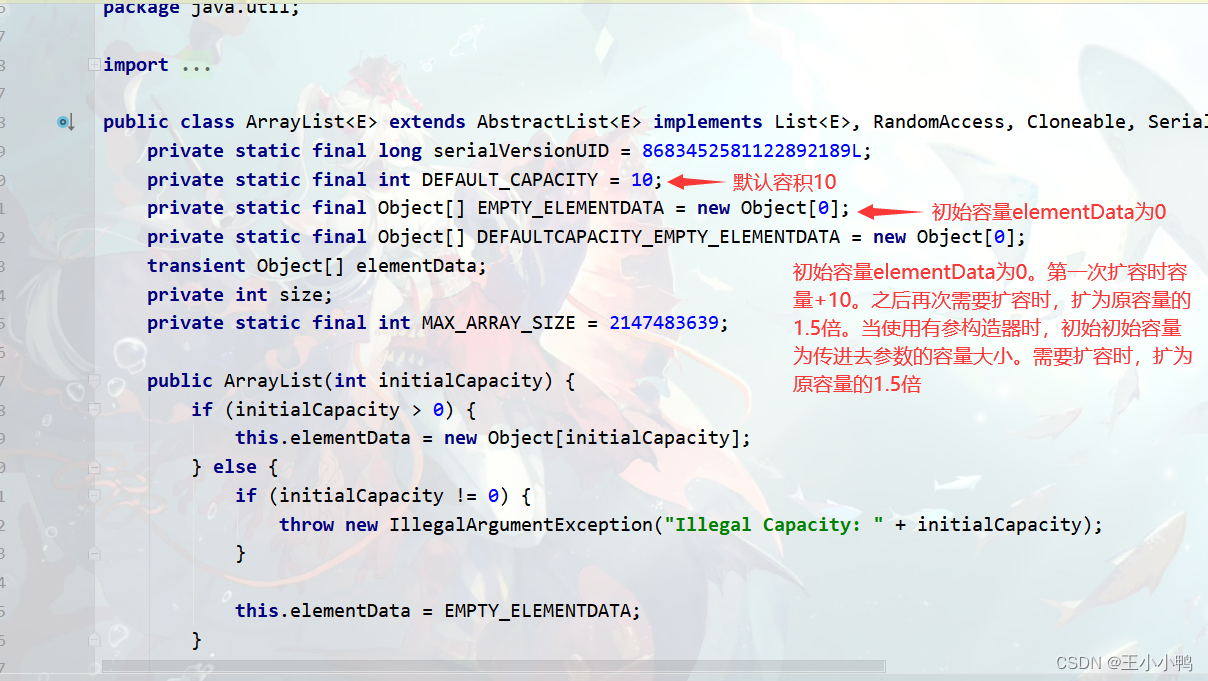
ArrayList Maximum capacity of
according to ArrayList Source code ,ArrayList The maximum capacity of is Integer.MAX_VALUE - 8 That is to say 2147483639. Why not Integer.MAX_VALUE Well ? Because some virtual machines keep some in the array header words, So reserved 8 To prevent cross-border
LinkedList
LinkedList yes java Implemented bidirectional queue , He has three member variables .LinkedList Because it is the linked list that causes the addition and deletion operations faster than ArrayList, Modifications and queries are slower than ArrayList.
Node( Find nodes by index )
LinkList Of Node() The method is to find nodes according to the index .Node() yes LinkedList The most important way , This method is required for addition, deletion, modification and query . This Node() It's not silly to go through it from beginning to end . He first judges the size of the index , If the index is greater than size/2 ( It's still a bit operation ), Then traverse forward from the tail . If the index is less than size/2, Then traverse from beginning to end .
indexOf( Find the index according to the node value )
This is really a silly traversal from beginning to end
Set
HashSet
When we new One. HashSet Then click into his constructor , We will be surprised to find HashSet The underlying implementation of HashMap. And when we pass in a collection ,HashMap The initial capacity of is max( Aggregate capacity /0.75+1,16).
HashSet The actual data of exists Node Inside key.Node Medium value A static variable is used PERSENT Occupy the pit
For details, see :
————————————————
Copyright notice : This paper is about CSDN Blogger 「OldZhangYH」 The original article of , follow CC 4.0 BY-SA Copyright agreement , For reprint, please attach the original source link and this statement .
Link to the original text :https://blog.csdn.net/qq_40679774/article/details/123229719
jdk8 HashMap Underlying principle
HashMap As Map The main implementation class of ,jdk1.2 appear , Thread unsafe , Efficient , Can be stored null Of key and value,jdk7 Its underlying structure is only : Array + Linked list ,jdk8 In its underlying structure : Array + Linked list + Red and black trees , About jdk8 Of
HashMap attribute ruxia:
1)DEFAULT_INITIAL_CAPACITY: HashMap Default Capacity :16( The initial value and can be 0)
2)DEFAULT_LOAD_FACTOR: Hash Default load factor :0.75
3)TREEIFY_THRESHOLD: When Linked list Data in the Greater than the default value , Convert to Red and black trees , The value is 8
4)MIN_TREEIFY_CAPACITY: In the bucket Node When being treelized The smallest hash Table capacity :64
5)threshold: The critical value of expansion , be equal to Capacity * Fill factor :16 * 0.75 =12
get hash After index , according to hash Index inserts data Map in .
If there is no element in that position, put it directly
If there is an element in that position , Then compare whether it is the same .( Determine whether it is the same object and equals(),( Different kinds of equals Is different . It depends on how it is rewritten ) Why not )
- Just give up if you are the same
- Different, continue to compare the elements in the linked list at this position , It's different until the end of the linked list, and it's at the end .
After the element is added to the linked list , If the length is greater than or equal to 8. - Array length is greater than or equal to 64, Tree the linked list of this location
- Otherwise, expand the array .


and JDK1.8 in ,HashMap use Array + Linked list + Red and black trees Realization , When The length of the list exceeds threshold (8) when , take Linked list Convert to Red and black trees , This greatly reduces the search time .

Details visible :http://t.csdn.cn/VUVLx
边栏推荐
- Baidu classic interview question - determine prime (how to optimize?)
- HSPF (hydraulic simulation program FORTRAN) model
- [basic data mining technology] exploratory data analysis
- 怎么在中金证券购买新课理财产品?收益百分之6
- One bite of Stream(6)
- ERROR 2003 (HY000): Can‘t connect to MySQL server on ‘localhost:3306‘ (10061)
- C synchronous asynchronous callback state machine async await demo
- Mathpix formula extractor
- Oracle primary key auto increment setting
- Five common misuse of async/await
猜你喜欢
PC port occupation release

Drive subsystem development
![[advanced data mining technology] Introduction to advanced data mining technology](/img/93/cb5ee07bff50662ad2496ca2bb39da.png)
[advanced data mining technology] Introduction to advanced data mining technology
Redis (12) -- redis server

MySQL - multi table query - seven join implementations, set operations, multi table query exercises

Case analysis of building cross department communication system on low code platform

None of the most complete MySQL commands in history is applicable to work and interview (supreme Collection Edition)

C synchronous asynchronous callback state machine async await demo

Information system project manager must recite the core examination site (47) project subcontract

Opencv learning Day2
随机推荐
[SOC] the first project of SOC Hello World
Smarter! Airiot accelerates the upgrading of energy conservation and emission reduction in the coal industry
[untitled]
Practical skills!!
Shengbang security rushes to the scientific innovation board: Qianxin is its largest customer (55.87 million); Its three-year revenue is 460 million, net profit is 95.04 million, and R & D investment
Huawei Router: basic principle and configuration of Isis (including experiment)
[Matplotlib drawing]
How to gracefully realize regular backup of MySQL database (glory Collection Edition)
Career development suggestions shared by ten CIOs
How to design the order system in e-commerce projects? (supreme Collection Edition)
[basic data mining technology] exploratory data analysis
Lenovo Filez helps Zhongshui North achieve safe and efficient file management
You must make good use of MySQL and JSON
[blind box app mall system] function introduction after online unpacking
Atcoder beginer contest 260 a~f problem solution
Five digital transformation strategies of B2B Enterprises
Is it safe for Hengtai securities to open an account?
RESNET interpretation and 1 × 1 Introduction to convolution
250 million, Banan District perception system data collection, background analysis, Xueliang engineering network and operation and maintenance service project: Chinatelecom won the bid
climb stairs