当前位置:网站首页>Easycvr platform security scanning prompt go pprof debugging information leakage solution
Easycvr platform security scanning prompt go pprof debugging information leakage solution
2022-07-24 13:22:00 【Tsingsee green rhino video】
We have shared with you in our previous blog about GO in pprof Debugging will prompt the handling method of information leakage , Interested users can read our previous articles to understand . Recently in many EasyCVR On site , When the user performs a security scan , Both reflect the following vulnerabilities :
The vulnerability prompt is EasyCVR The background monitoring mode is turned on , We can do it in /easycvr.ini File close the configuration . The operation is as follows :
1) open easycvr.ini file ;
2) take is_pprof=true, Change it to false, Pictured :
After the modification , The above vulnerability prompt will not appear .
EasyCVR Simple deployment 、 High compatibility , The platform adopts distributed deployment , It can provide unified API Interface , Connect devices 、 Connect data 、 Connect applications , Facilitate the rapid integration of third-party platforms .
The platform relies on excellent video resource access and processing capabilities , It has been applied in many project scenarios , Such as bright kitchen and bright stove 、 Smart construction site 、 Snow project 、 Ping An Village, etc . Interested users can go to the demonstration platform for experience or deployment testing .
边栏推荐
- 浅谈Node Embedding
- 30. Rearrange the linked list
- Summary of embedded network problems (packet loss of network card, unrecognized network card)
- Solution to embedded SD card /u disk read-only problem (fat read-only repair method)
- 开山之作造假!Science大曝Nature重磅论文学术不端,恐误导全球16年
- 户外广告牌不能“想挂就挂”!广州城管部门加强户外广告安全管理
- 关于如何提升TTL(UART)通信抗干扰——心得
- Analysis of abnormal problems of embedded SD card
- flinksql 在yarn上面怎么 以 perjob 模式跑啊,我在sqlclient 提交任务之
- Introduction of embedded network interface scheme and summary of driver debugging methods
猜你喜欢
This is how the permission system is designed, yyds
The core capability of accelerating enterprise data application innovation flexibility

30. Rearrange the linked list
![[stm32] internal independent watchdog iwdg](/img/7f/752528e9a76097b51c8f9463c33db3.png)
[stm32] internal independent watchdog iwdg

Nearly 65billion pieces of personal information were illegally handled in seven years, and the investigation of didi network security review case was announced

Where+or usage of SQL missing condition
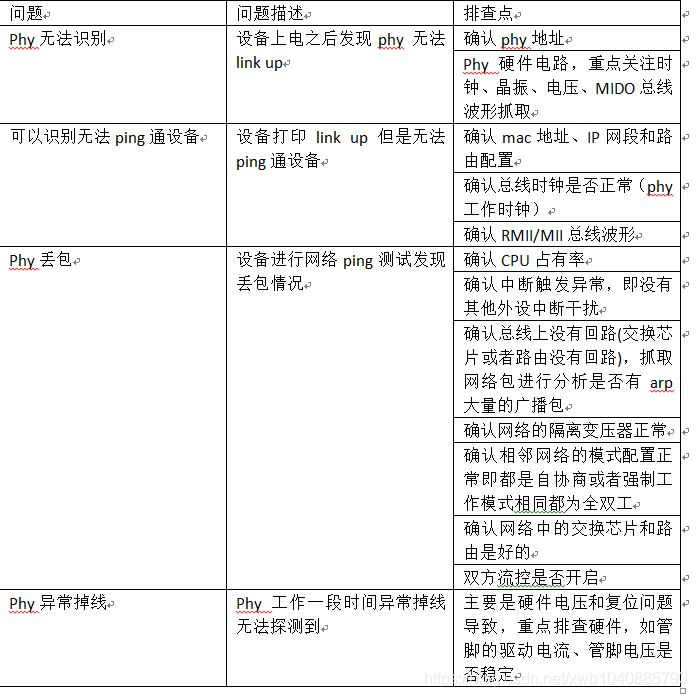
Summary of embedded network problems (packet loss of network card, unrecognized network card)
![[datasheet] interpretation of cs5480 data book of metering chip](/img/1a/e8a4ce5c393a6634b6dc8bf6d687e2.png)
[datasheet] interpretation of cs5480 data book of metering chip
About the concept of thread (1)

Copy of array and array address value
随机推荐
汉字风格迁移篇---无监督排版传输
Embedded cognitive network card PHY self negotiation
selenium环境配置和八大元素定位
jsonp
Nearly 65billion pieces of personal information were illegally handled in seven years, and the investigation of didi network security review case was announced
Question 10: find numbers in an array with rows and columns in order
Are there any useful and free redis client tools recommended?
Chrome plug-in development tutorial
About thread (4) thread interaction
flow
Notes on Linear Algebra -- lesson 25 -- projection of vectors on axes
Experience on how to improve the anti-interference of TTL (UART) communication
vscode配置用户代码片段(包括删除方法)
LEADTOOLS 22 套件 LEADTOOLS 超级套
Proxy
深入浅出边缘云 | 2. 架构
Embedded problem troubleshooting methods, network problems, SD card problems, device startup problems, serial port problems, I2C problems, SPI problems, PCIe problems, etc
Where+or usage of SQL missing condition
20201127 use markdown to draw UML diagrams, graphviz installation experience hematemesis finishing
Wang Ping, co-founder of Denglin Technology: Innovation + self research "dual core" drive, gpu+ enabling AI takes root | quantum bit · viewpoint sharing review
