当前位置:网站首页>Adb authorization process analysis
Adb authorization process analysis
2022-08-05 07:59:00 【Xiaoyuanzi 2016】
adbkey and adbkey.pub
adbkey and adbkey.pub_caibaihui's blog - CSDN blog _what is adbkey file
Experiments have shown that the public key on the mobile phone and the private key on the computer can be successfully paired, even if I modify the public key on the computer later, it will not affect the previous authorization
For example, the mobile phone has a built-in public key, and the paired private key is generated on my computer to complete the authorization

adb pull /data/misc/adb/adb_keys . The public key is stored in it
The authorization pop-up window shows that the RSA key fingerprint should be based on the public key. I don't know how to calculate it.
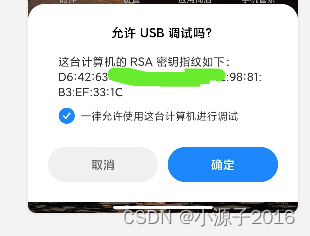
adb keygen cc can be used to generate RSA public and private keys
This information box will typically display the fingerprint (MD5) of the host's public key, not the host's
public key itself
ADB public key and private key authentication mechanism Use the following command to generate the host public key fingerprint: $ awk "{print $1}" < adbkey.pub | openssl base64 -A -d -a | openssl md5 -c | awk "{print $2}" | tr "[:lower:]" "[:upper:]" Actually, I used this command to find that the generated pop-up window is different from the one I saw, I am ready to give up and find new articles In general, it is necessary to process base64 and md5 separately For this, I need to know that the actual key in the file is the base64 encoded part, i.e. long cryptic string of characters.In my case the key field was always followed by the user-host field, i.e. something like In the latter case, I need to filter on the second field.In Windows, apparently, this is done using a Extract the key in the second field of 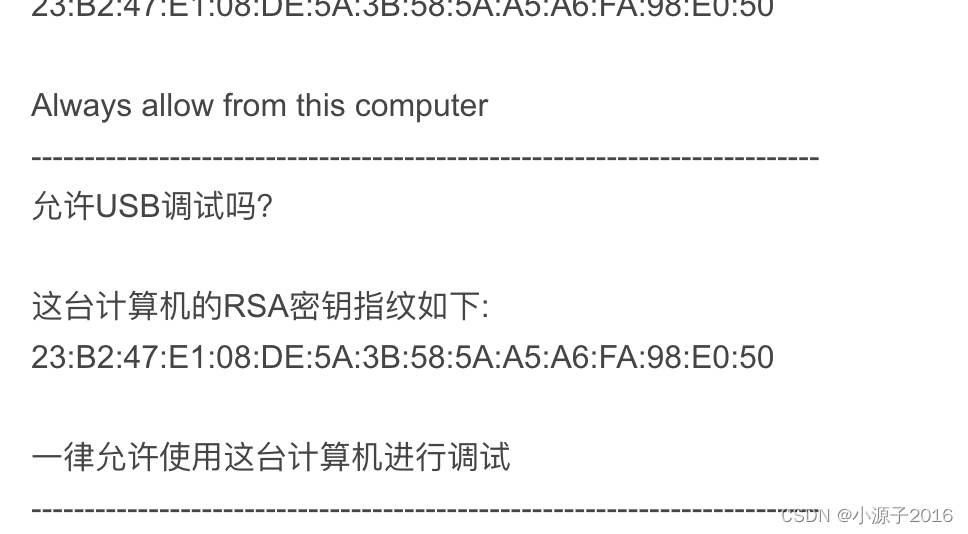
23:B2:47:E1:08:DE:5A:3B:58:5A:A5:A6:FA:98:E0:50[email protected] (also [email protected]), in some strings the case is preceded by a field containing ssh-rsa.for loop.I also send the output to a file for certUtil to do subsequent digestion, the output of which goes into the file again - containing the key which is no longer base64 encoded but in bytes - and finally hashed with MD5.id_rsa.pub into a file named tmp.key_base64:
边栏推荐
- 线程池的创建及参数设置详解
- TRACE32——SMP多核调试
- 向美国人学习“如何快乐”
- Green Apple Forum reopens
- Fiddler tool explanation
- Fiddler工具讲解
- U++ UE4官方文档课后作业
- 【 LeetCode 】 235. A binary search tree in recent common ancestor
- Basic introduction of stack and queue and C language implementation of functions such as creation, destruction, entry and exit, counting the number of elements, viewing elements, etc., as well as stac
- 【win7】NtWaitForKeyedEvent
猜你喜欢
随机推荐
GAN generates anime avatar Pytorch
v-if/v-else determines whether to display according to the calculation
剑指Offer面试题解总结1-10
TRACE32——C源码关联1
网络安全研究发现,P2E项目遭遇黑客攻击只是时间问题
餐饮大单品「真香」,却没有穿透周期的能力
MySQL: order by sorting query, group by grouping query
unity urp 渲染管线顶点偏移的实现
外企Office常用英语
软件系统测试和验收测试有什么联系与区别?专业软件测试方案推荐
Antdesign a-select 下拉框超出长度换行显示
[Untitled] Long-term recruitment of hardware engineers-Shenzhen Baoan
长期招聘嵌入式开发-深圳宝安
Fiddler tool explanation
Win10 设置锁屏壁纸提示尝试其它图片
Vulnhub target drone: HA_ NARAK
Redis常用命令
作为一个男人必须明白的22个道理
Green Apple Forum reopens
Unity—物理引擎+“武器模块”