当前位置:网站首页>Zadig + cave Iast: let safety dissolve in continuous delivery
Zadig + cave Iast: let safety dissolve in continuous delivery
2022-06-24 19:27:00 【Zadig cloud native delivery】

IAST As a kind of security testing technology, it has attracted much attention , How can we make use of Zadig Runtime environmental management capability , Fast will IAST Ability to integrate into our daily workflow ?
IAST As a kind of security testing technology, it has attracted much attention , How can we make use of Zadig Runtime environmental management capability , Fast will IAST Ability to integrate into our daily workflow ? In this paper Zadig K8s project + Java Service as an example , To understand in Zadig How to quickly access existing services in IAST Monitoring service vulnerability information , Escort the service safety .
What is IAST & DongTai?
IAST: Interactive application security testing (Interactive Application Security Testing), It is a new technology rising in recent years , By Gartner The company is listed as a leader in the field of information security Top 10 One of the technologies . It is a blend of SAST and DAST Advantages of Technology ,IAST Use the runtime proxy method to analyze in the test phase & Monitor application behavior .
DongTai Is an open source passive interactive security test (IAST) product , Through dynamic Hook And stain tracking algorithm to achieve universal vulnerability detection 、 Multi request correlation vulnerability detection ( Including but not limited to ultra vires 、 Unauthorized access )、 Third party component vulnerability detection, etc , At present, we support Java、Python Application vulnerability detection of two languages .
️ Be careful : It is mainly used for development environment and Test environment , That is, security detection can be carried out with a single access , It is not suitable for production environments with high concurrency ( Reference resources IAST Performance test report [1])
Zadig & IAST Operating principle diagram

preparation
1. Zadig To be opened IAST Functional services , Here is a sample service , service name :demo , service YAML The configuration is as follows (Zadig New service [2]):
apiVersion: apps/v1kind: Deploymentmetadata: labels: app: dongtai-java-agent-demo name: dongtai-java-agent-demospec: selector: matchLabels: app: dongtai-java-agent-demo template: metadata: labels: app: dongtai-java-agent-demo spec: containers: - name: app-container image: dongtai/dongtai-java-agent-demo:0.0.1
2. obtain DongTai backend service , There are two ways :
- Use the hole state official SaaS edition
- Use Docker-Compose perhaps Kubernetes Complete the privatization installation Installation document [3]
Let's take the first method as an example , Use the hole state official SaaS service , Sign up for a login account , Enter the project management interface :
- Click on the top right corner of the page 「+ Add Agent」
- stay 「 Download probe 」 Part can be downloaded directly or get the download link

Here we assume that the connection we get is :
AGENT_URL= http://192.168.2.169:8000/api/v1/agent/download?url=http://192.168.2.169:8000&language=javaAUTH_HEADER= 'Authorization: Token 88cab3057e199b95cb0780e2a8ab4771c8874acd' The following is the Shell Script :The following is the Shell Script :
curl -X GET "http://192.168.2.169:8000/api/v1/agent/download?url=http://192.168.2.169:8000&language=java" -H 'Authorization: Token 88cab3057e199b95cb0780e2a8ab4771c8874acd' -o agent.jar -k
establish & Deploy Inject Agent Of demo service
- stay Zadig Copy the service configuration to be tested , modify K8s resource name as well as label&selector etc. , Avoid conflicts with existing services .
- Add in configuration initContainer, Advance agent Download to the container where the service is located .
- Modify the service startup command , add to -javaagent:/path/to/agent.jar
- New service , service name :demo-with-iast, Paste the modified configuration and save , The modified service YAML The configuration is as follows :
apiVersion: apps/v1kind: Deploymentmetadata: labels: app: dongtai-java-agent-demo-iast name: dongtai-java-agent-demo-iastspec: selector: matchLabels: app: dongtai-java-agent-demo-iast template: metadata: labels: app: dongtai-java-agent-demo-iast spec: volumes: - name: dongtai-iast-agent emptyDir: {} initContainers: - name: agent-init-container image: curlimages/curl volumeMounts: - name: dongtai-iast-agent mountPath: /tmp args: - "-k" - "-X" - "GET" - ${AGENT_URL} # Replace with the previously obtained AGENT_URL - "-H" - ${AUTH_HEADER} # Replace with the previously obtained AUTH_HEADER - "-o" - "/tmp/agent.jar" containers: - name: app-container image: dongtai/dongtai-java-agent-demo:0.0.1 volumeMounts: - name: dongtai-iast-agent mountPath: /agent env: - name: JAVA_TOOL_OPTIONS value: "-javaagent:/agent/agent.jar"
5. The new service demo-with-iast Deploy to environment (Zadig Create an environment [4]), View the logs of services in the corresponding environment , The following log will mean agent Inject success .

6. Based on newly deployed demo-with-iast service , Automated testing of running services & A functional test , Trigger internal functions / Invocation of service ,agent It will automatically collect and report vulnerability information during operation .
thus , Vulnerability information has been collected and reported , You can get it just now Dongtai backend View information about current service vulnerabilities in .
Configure automated workflows
If we want to track the vulnerability information in the service in real time , We need to IAST Into our DevOps In the process . Let's assume that demo The service already has Zadig workflow & Build configuration (Zadig Workflow configuration [5])), At this time, we only need two steps to easily IAST Join our existing process .
- The service we just configured demo-with-iast And demo Build bindings for services .

2. Start workflow , Choose services demo-with-iast, Deploy and validate our latest services .

Running effect
Go back to the hole backend Interface , Click item , You can see the vulnerability analysis of the current service :
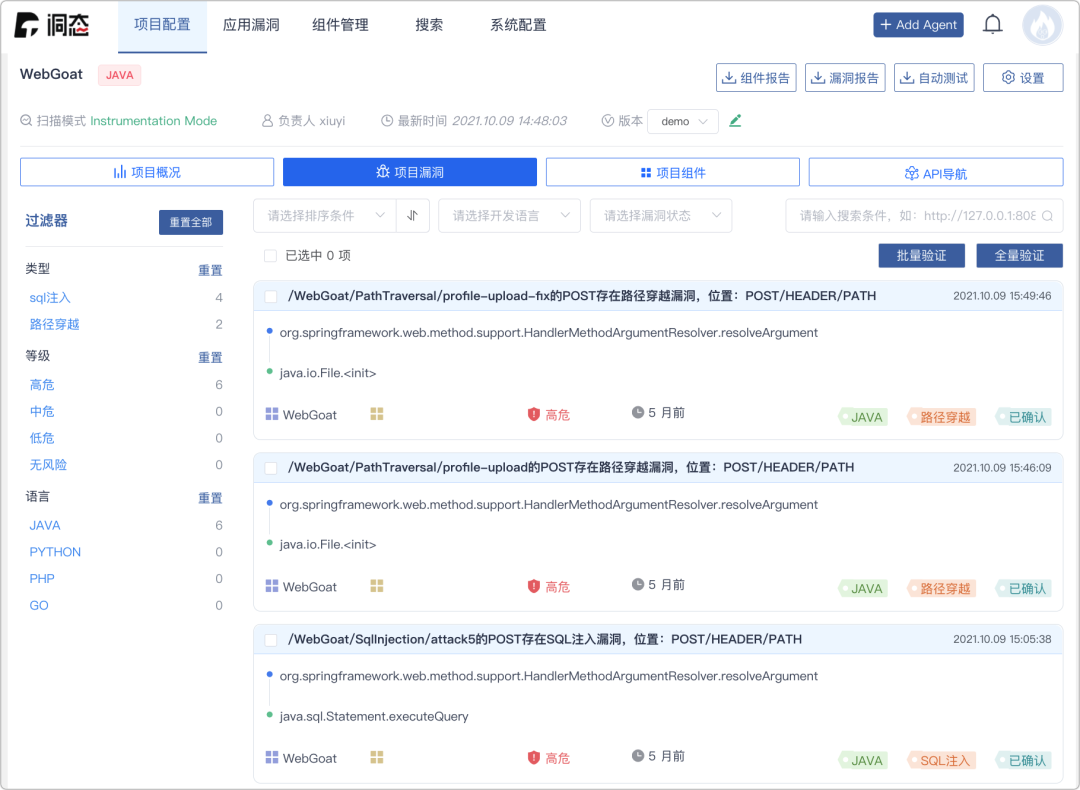
So far we have IAST Testing and Zadig The delivery process is seamlessly integrated , Engineers can detect the vulnerability of business service updates at any time , More secure and reliable iterative products .
Reference link :
[1] Cave state JAVA Agent v1.7.0 Performance testing
[2] https://docs.koderover.com/zadig/v1.12.0/project/service/k8s/# New service
[3] https://doc.dongtai.io/docs/category/server- Deployment Guide
[4] https://docs.koderover.com/zadig/v1.12.0/project/env/k8s/# Create an environment
[5] https://docs.koderover.com/zadig/v1.12.0/project/workflow/# Configure workflow
Zadig, Let engineers focus more on creating !
Welcome to join Make complaints about open source Tucao group
边栏推荐
- Xiaobai, let me ask you guys, is MySQL binlog extracted by CDC in strict order
- Will the CDC read out of order when I use SQL
- 怎么使用R包ggtreeExtra绘制进化树
- Preliminary study nuxt3
- php OSS文件讀取和寫入文件,workerman生成臨時文件並輸出瀏覽器下載
- Does finkcdc support sqlserver2008?
- 应用实践 | 海量数据,秒级分析!Flink+Doris 构建实时数仓方案
- Interpreting harmonyos application and service ecology
- 60 divine vs Code plug-ins!!
- NFT pledge liquidity mining system development technology
猜你喜欢

Necessary fault handling system for enterprise network administrator

Programmers spend most of their time not writing code, but...
对国产数据库厂商提几个关于SQL引擎的小需求

Mqtt protocol usage of LabVIEW
What other data besides SHP data

Why are life science enterprises on the cloud in succession?

R语言corrplot相关热图美化实例分析
SaltStack State状态文件配置实例

Volcano becomes spark default batch scheduler

Game between apifox and other interface development tools
随机推荐
实时渲染:实时、离线、云渲染、混合渲染的区别
ls 常用参数
通过SCCM SQL生成计算机上一次登录用户账户报告
8 challenges of BSS application cloud native deployment
我链接mysql 报这个错 是啥意思呀?
Server lease error in Hong Kong may lead to serious consequences
cdc sql表里面的datetime要用什么类型替换
Source code analysis of ArrayList
优维低代码:构件渲染子构件
three. Basic framework created by JS
TKDE2022:基于知识增强采样的对话推荐系统
NFT质押流动性挖矿系统开发技术
一文理解OpenStack网络
Volcano devient l'ordonnanceur de lots par défaut Spark
php OSS文件读取和写入文件,workerman生成临时文件并输出浏览器下载
60 divine vs Code plug-ins!!
我用sql形式的会出现cdc读取乱序吗
Volcano成Spark默认batch调度器
模块五
Introduction and download tutorial of administrative division vector data